AI-powered cyber risk
and exposure management
One platform for exposure management
and risk quantification
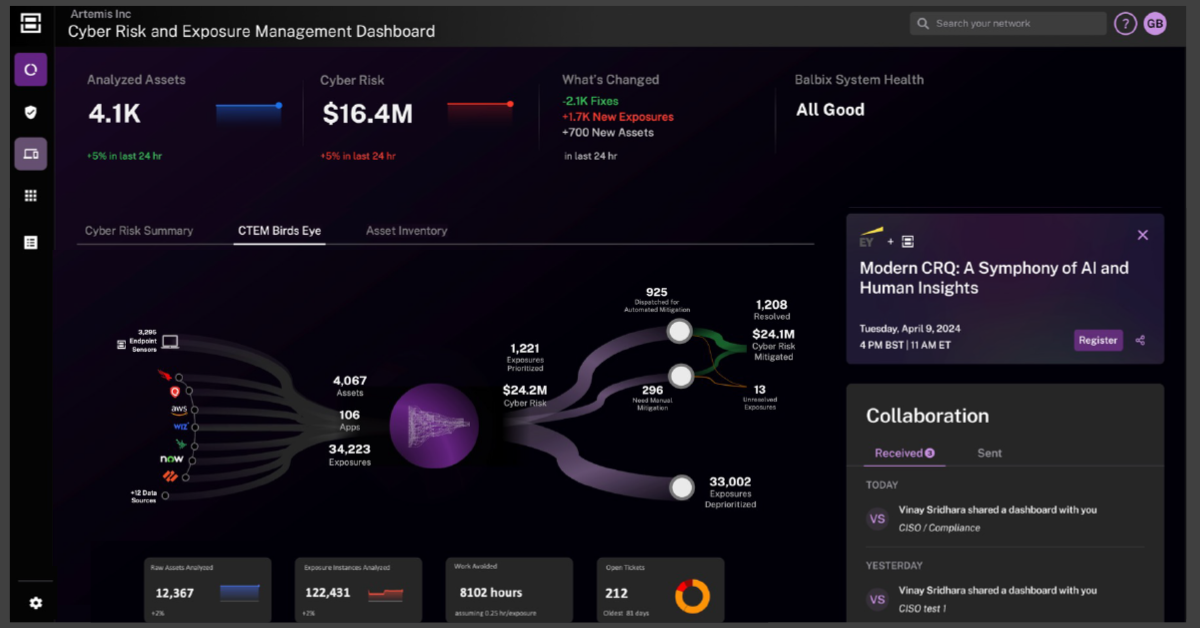
Ingest asset, vulnerability, and exposure data from hundreds of tools for a unified view of your attack surface.
Leverage AI to intelligently fill gaps in asset and exposure data, deducing missing details when native connectors provide incomplete information.
Automatically enriches assets with technical, business, and risk context for informed decision-making.
Identify outdated or inactive assets in CMDB and update them to keep your CMDB up-to-date.
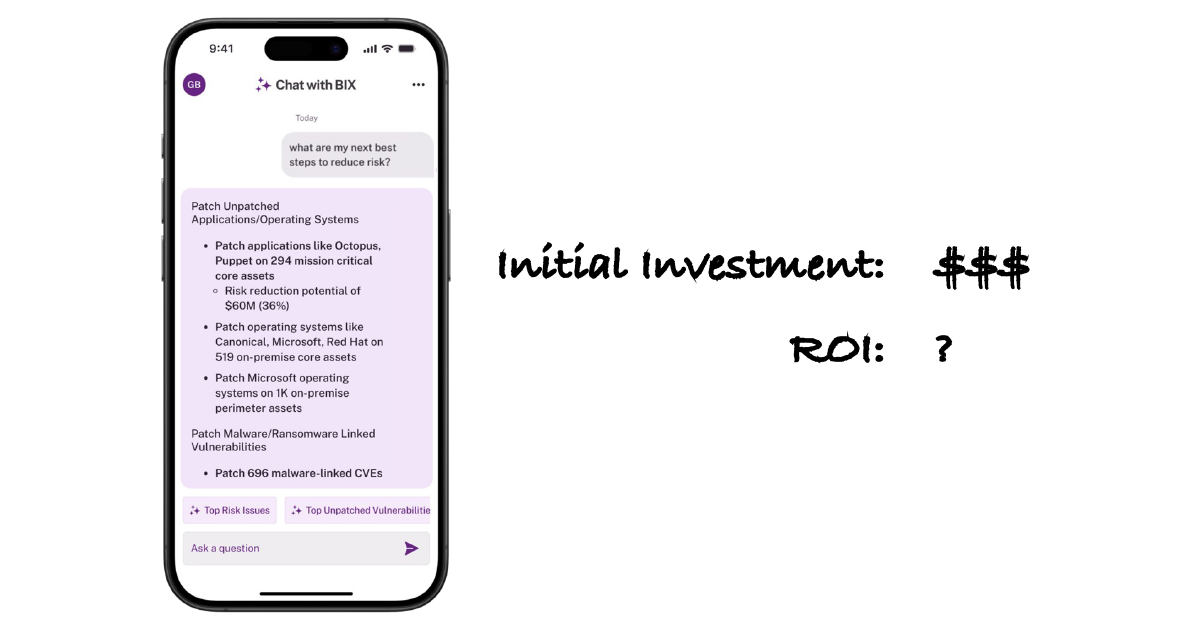
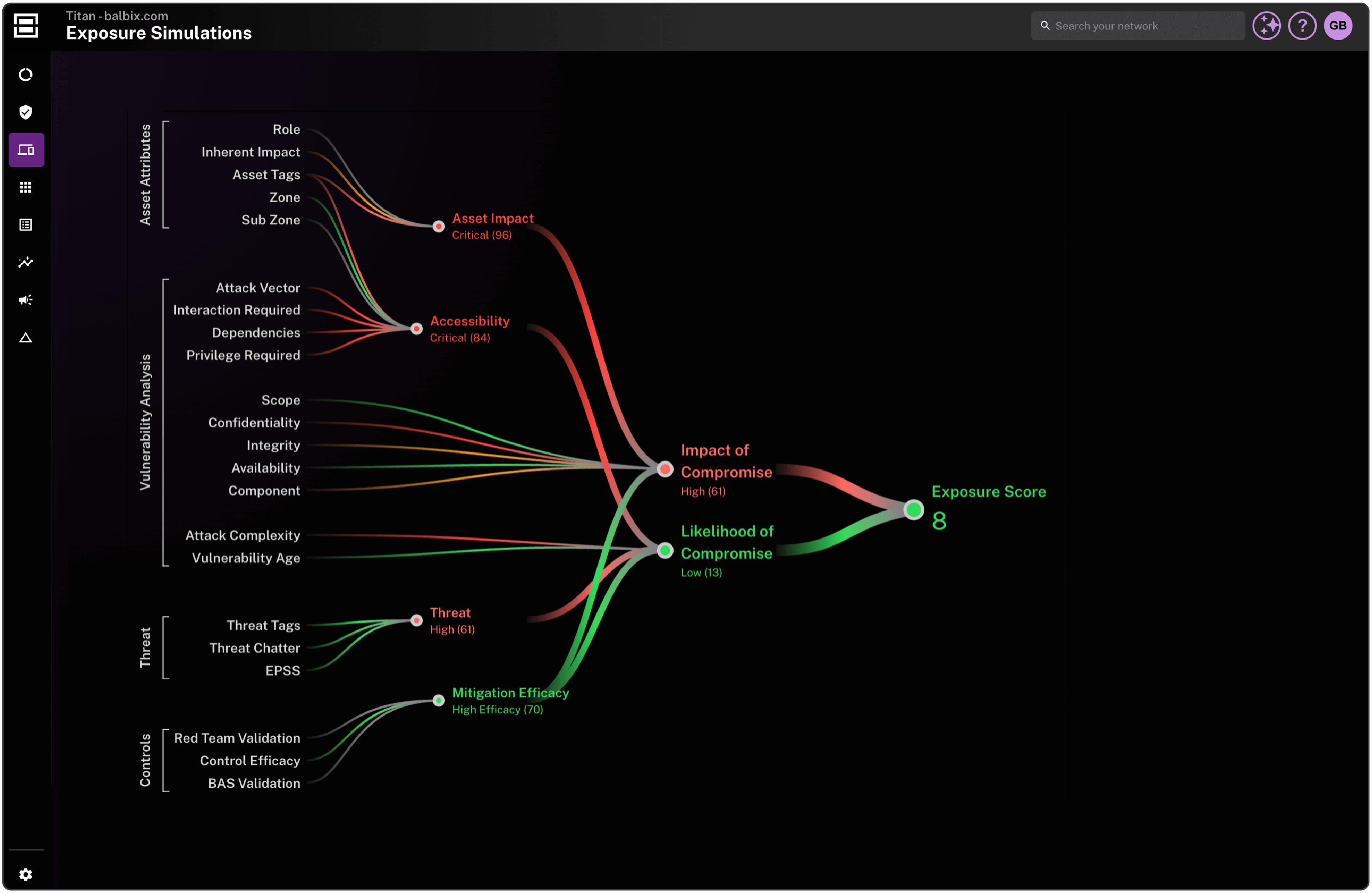
Go beyond severity to prioritize based on threat intel, mitigating controls, exploitability, and business impact.
Use a consistent scoring model for CVEs and non-CVEs to help you prioritize the risk that truly matters in your environment.
Incorporate findings from BAS tools, red team exercises, and pen tests to prioritize exposures.
Add business context using tags to enrich assets with information such as mission-critical or sensitive data for risk-based prioritization.
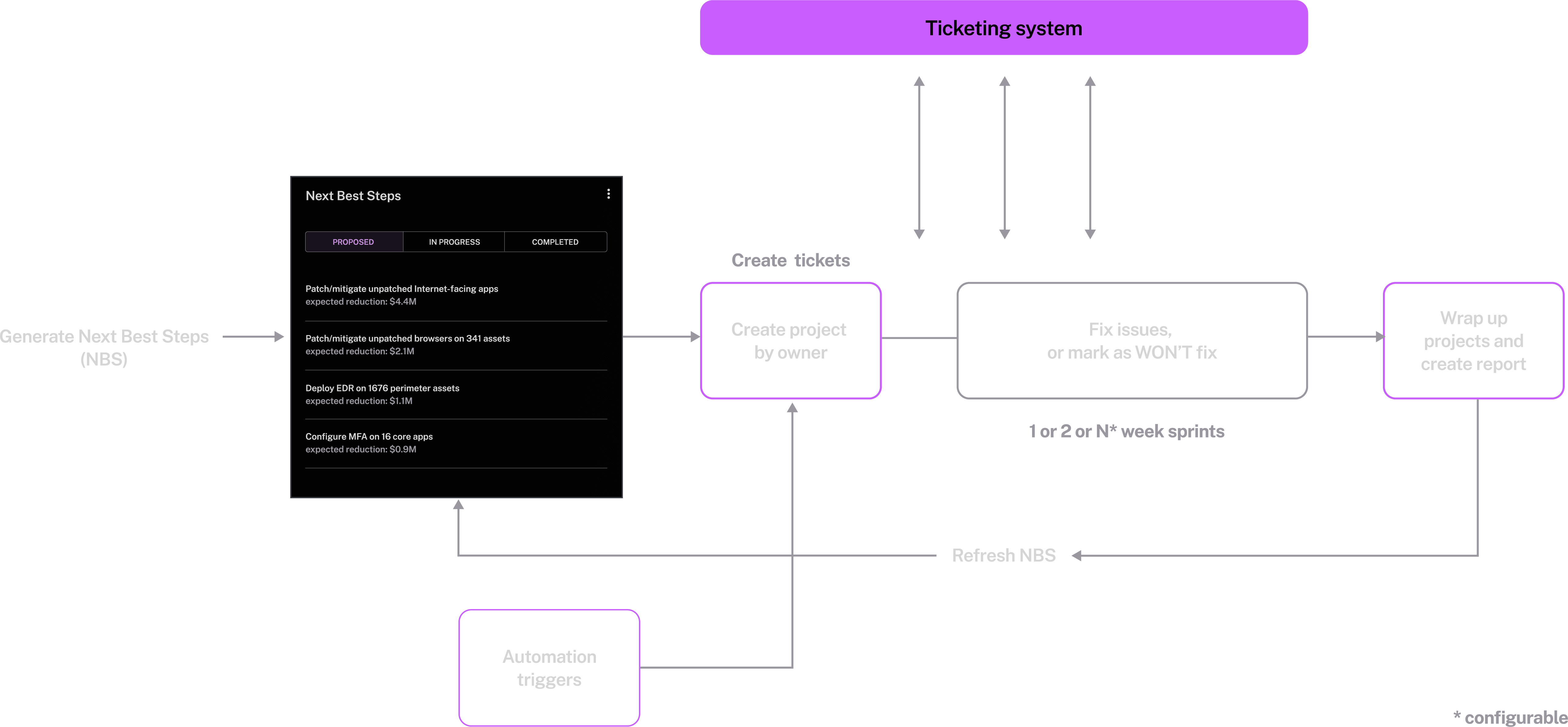
Build risk reports, synthesize complex security data, and take remediation action to speed up work.
Get interactive dashboards, MITRE TTP mapping, and gamification to accelerate the performance of your security program.
Built-in workflows to manage remediation as sprint projects with clear milestones, metrics, and owners, resulting in faster risk burndown.
Out-of-the-box KPIs, such as MTTP, MTTR, and MOVA, to track the success of EM and VM programs.
Balbix integrates with hundreds of IT, security and business tools to consolidate assets, applications, exposure and vulnerabilities in a single platform.

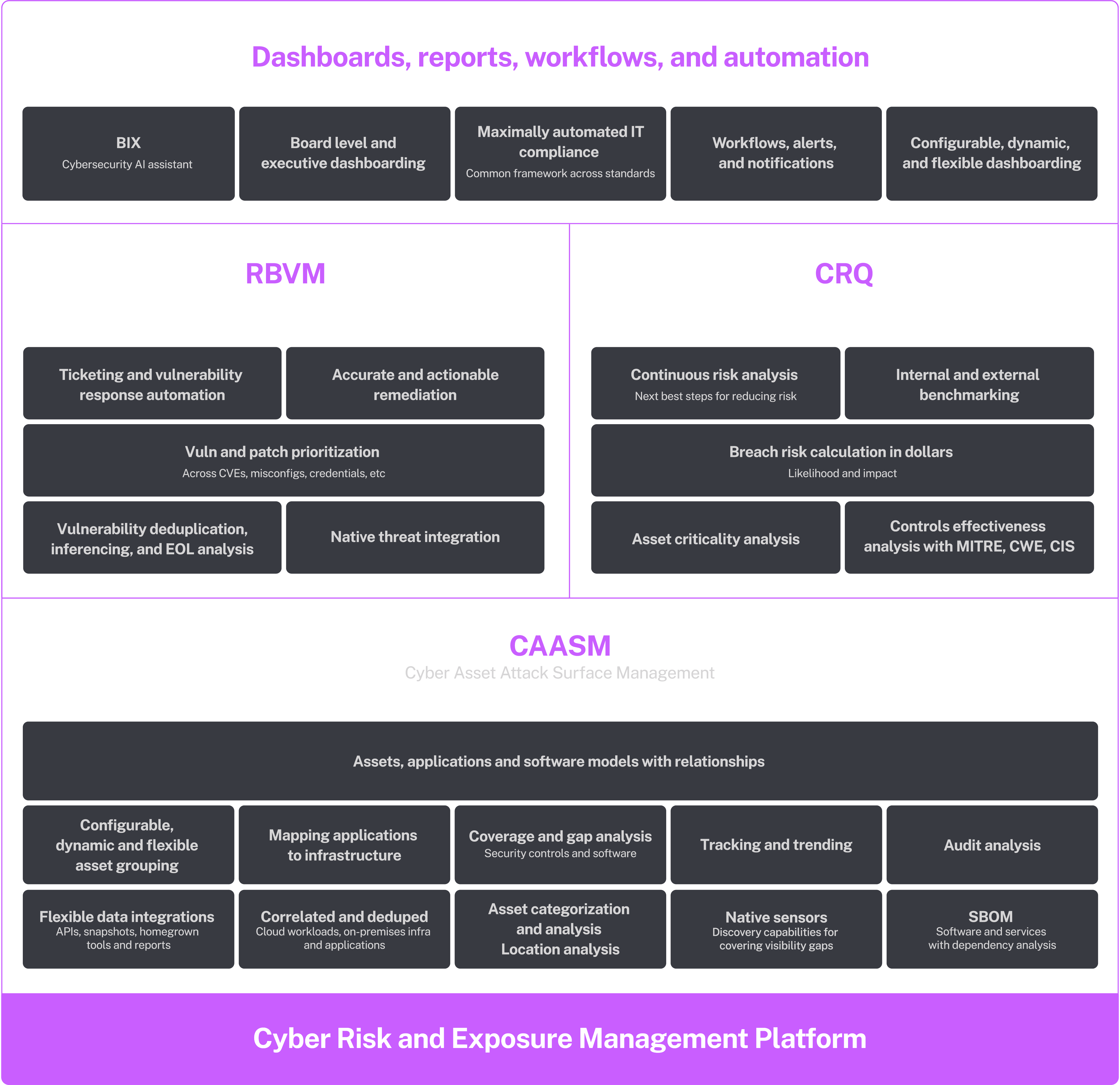
The Balbix platform was designed as a flexible offering to help you solve a wide variety of security challenges without needing to re-do your security architecture.
Balbix Core provides you with CAASM capabilities and more – unified asset inventory, deduplicated, correlated and enriched with cybersecurity, IT and business context.
Identify and prioritize vulnerabilities and patches based on risk. Drive remediation workflows and reduce MTTR and MOVA.
Quantify cyber-risk in dollars broken down by risk owners and types. Demonstrate the ROI of your security program.
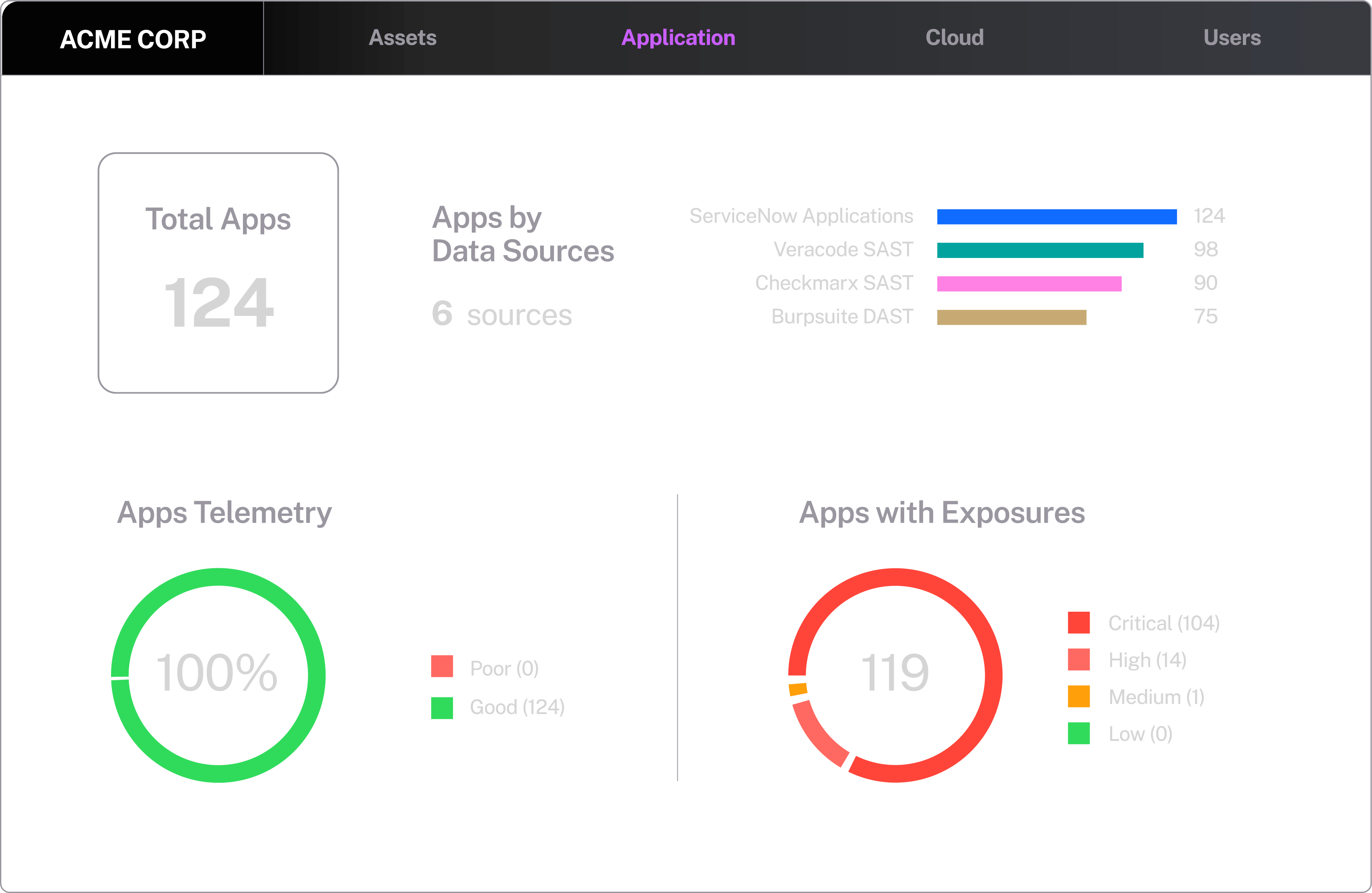
Map business applications to infrastructure, OS and DAST/SAST vulnerabilities as well as security controls.
Compensate for coverage gaps, and provide a runtime software bill of materials.
Improve accuracy of your CMDBs by updating assets attributes missed by CMDB reconciliation processes.