Vendor risk management (VRM) involves identifying, assessing, monitoring, and addressing risks from third-party vendors and suppliers, focusing on cybersecurity. It helps protect your organization’s data, systems, and operations from risks associated with working with external vendors.
VRM is a key part of a broader third-party risk management program. While that program covers financial, operational, and brand reputation risks, VRM specifically tackles the rising threat of cyber risks, which are becoming more sophisticated and frequent.
The main goal of VRM is to ensure vendors meet your security standards. This means evaluating their security controls, monitoring their performance, and assuming responsibility for fixing any vulnerabilities. By staying proactive, you reduce the risks vendors may pose to your organization.
Why Vendor Risk Management Matters
With more businesses relying on third-party vendors, managing vendor risks has never been more critical. Vendors help deliver streamlined, critical services, but their security practices can directly impact your organization’s cybersecurity.
Past breaches like SolarWinds and Kaseya show how vulnerabilities in vendor ecosystems can lead to severe disruptions. Effective vendor risk management (VRM) ensures your vendors meet high-security standards, reducing exposure to potential threats.
Moreover, staying compliant with regulations that require strict vendor oversight protects your business from fines and reinforces your commitment to data security.
What are Vendor Cybersecurity Risks?
Vendor cybersecurity risks can compromise your data, systems, and business operations if not managed effectively. Here are the main risks:
- Data Breaches: Vendors often need access to your sensitive information, which creates weak points for potential data breaches. To lower these risks, tighten data access controls and review vendor practices.
- System Compromise: When vendors connect to your systems, they can open the door to cyberattacks. Implementing strong access control measures can protect more critical areas.
- Compliance Violations: If your vendors don’t comply with regulations like GDPR, it can hurt your business. Make compliance part of your vendor contracts and conduct regular checks to stay compliant.
- Operational Disruptions: Vendor issues can halt essential processes, affecting a service’s delivery. Plan for vendor contingencies in your business continuity plans to keep operations running smoothly.
Vendor Risk Assessment and Monitoring
Before signing a contract, assess a vendor’s security controls. Use security questionnaires, audits, and independent ratings to get a complete picture of their practices. Once onboard, continuously monitor their access and activities to stay ahead of potential risks.
Assign financial value to risks to prioritize the most critical vulnerabilities. This helps align your risk management with broader business goals.
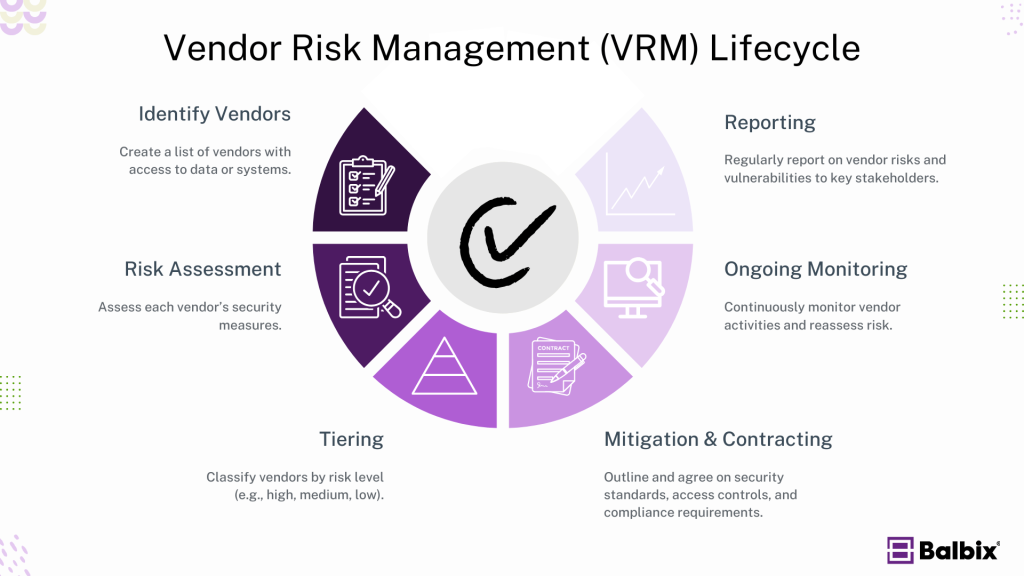
Building a Vendor Risk Management Program
To start a VRM program, first, build a complete list of all your vendors. Document every third-party interaction with your data and systems. Centralizing this information makes managing contracts and vendor details easier, improving communication and oversight.
Define Risk-Based Tiers
Not all vendors carry the same risk. Classify vendors by the sensitivity of the data they access and the importance of their service. This helps you create custom management strategies for each tier. For example, vendors handling sensitive data need more frequent reviews than those with limited access.
Assess and Address Risks
Vendor risk assessments should begin before onboarding. Use questionnaires, audits, and security ratings to evaluate vendors. But don’t stop there—ongoing assessments ensure they adhere to your security standards. Work with vendors to resolve issues, build a trusted relationship and reduce risk.
Monitor and Report
Continuous monitoring helps you closely monitor vendor activities. Regular reports and risk metrics help senior leadership make informed decisions. Clear communication about vendor risks ensures everyone stays aligned with your broader business objectives.
Balbix makes vendor risk management easier by using AI to assess and prioritize vendor risks automatically. It continuously monitors vendor security practices and highlights vulnerabilities that need attention.
With Balbix, you’ll get easy-to-understand insights that help you focus on the biggest risks, fix problems faster, and stay compliant—all without the hassle of manual work. It streamlines everything, from vendor assessments to monitoring, so you can keep your business secure with less effort.
Frequently Asked Questions
- What is the difference between CRM and VRM?
-
CRM (Customer Relationship Management) focuses on how businesses manage their interactions with customers, with the overall goal to improve relationships and increase repeat sales. VRM (Vendor Relationship Management), on the other hand, encourages businesses to manage their own data and relationships with vendors, giving them more control over their interactions.
- What is an example of a vendor relationship?
-
A vendor relationship is a business partnership where one company provides goods or services to another. For example, a coffee shop might work with a supplier who delivers coffee beans regularly, ensuring the shop always has fresh coffee to serve customers.
- What is the difference between vendor management and supplier management?
-
Vendor management focuses on managing the relationships and performance of third-party providers who deliver products or services. Supplier management, on the other hand, deals specifically with those who supply goods or materials needed for production, emphasizing procurement and quality control. Both aim to optimize business efficiency.


