Cyber resilience is an organization’s ability to detect, respond to, and quickly recover from a wide range of cyber threats, including internal risks and external attacks like data breaches and ransomware. It goes beyond cybersecurity by preventing attacks and ensuring business continuity during and after an incident. Cyber resilience involves continuous strengthening of defenses against evolving cyber threats.
Why is Cyber Resilience Important?
Cyber resilience is crucial as cyberattacks are inevitable, and their impacts—such as financial loss, business disruptions, and reputational damage—can be severe. In 2024, the average cost of a data breach reached $4.88 million. A solid cyber resilience strategy helps organizations detect threats early, recover swiftly, and minimize damage.
In light of increased remote work and fast-evolving cyber threats, a robust cyber resilience plan ensures minimal disruption to operations and compliance with regulatory requirements. You should enhance your organization’s cyber resilience to safeguard against future threats and ensure business continuity.
What are the Components of Cyber Resilience?
Cyber resilience is more than just fending off attacks—it’s about ensuring your organization can continue operating, adapting, and thriving despite them. The key goals of cyber resilience are:
Cybersecurity
Cybersecurity is the core of cyber resilience—the technologies and processes that defend your organization’s assets from cyber threats. This involves safeguarding networks, systems, and data against various potential attacks, including malware, ransomware, and insider threats. Effective cybersecurity measures reduce the likelihood of successful breaches, thus forming the first line of defense in a comprehensive cyber resilience strategy.
Cybersecurity vs. Cyber Resilience
Cyber resilience complements cybersecurity. While cybersecurity focuses on defense, cyber resilience ensures the organization can bounce back when defenses are breached. Together, they form a holistic approach to safeguarding digital assets.
Risk Management
Risk management is identifying, assessing, and prioritizing potential threats to your organization. By understanding where your vulnerabilities lie, you can take proactive steps to mitigate these risks before they escalate into serious incidents. This might involve patching software, strengthening access controls, or implementing advanced monitoring tools. Risk management is a continuous process in a resilient organization, adapting to new threats as they emerge.
Business Continuity
Business continuity is about keeping the lights on, no matter what. Even in a cyber incident, your organization must be able to maintain essential functions. This involves a well-defined plan ensuring critical services remain operational during and after an attack. Business continuity planning includes strategies like redundancy, disaster recovery sites, and communication plans to keep stakeholders informed and operations running smoothly.
Disaster Recovery
Disaster recovery focuses on swiftly restoring systems and data after a cyber incident. This goal is crucial for minimizing downtime and restoring normal business operations quickly. Effective disaster recovery plans include regular backups, clearly defined recovery time objectives (RTOs), and recovery point objectives (RPOs), ensuring your organization can bounce back with minimal disruption.
What are the Benefits of Cyber Resilience?
Cyber resilience needs to be a core focus for organizations. The benefits of cyber resilience include:
- Reduced Downtime: Ensures business operations continue smoothly during and after cyber incidents, minimizing disruptions.
- Enhanced Recovery: Accelerates restoring systems and data, reducing recovery time and costs.
- Improved Risk Management: Identifies and mitigates potential threats proactively, decreasing the likelihood of successful attacks.
- Increased Trust: Maintains customer and stakeholder confidence by demonstrating robust measures to protect and recover from cyber threats.
- Regulatory Compliance: Helps meet industry regulations and standards for data protection and incident response.
How does Cyber Resilience Work?
A cyber resilience strategy, guided by the NIST 2.0 Cybersecurity Framework (CSF), focuses on six core functions:
- Identify: Understand and manage cybersecurity risks with asset management, risk assessment, and governance frameworks.
- Protect: Implement safeguards such as encryption, access controls, and regular patch management to secure critical assets.
- Detect: Use tools like endpoint detection and response (EDR) and intrusion detection systems (IDS) to identify threats early.
- Respond: Develop incident response plans to manage and contain cyber incidents, ensuring minimal disruption.
- Recover: Establish disaster recovery and business continuity plans to restore systems and data quickly after an attack.
- Govern: Implement a cybersecurity risk management strategy, set expectations, and define policies that guide the organization’s cybersecurity efforts.
By integrating these functions, organizations can build a robust cyber resilience program that adapts to evolving threats and ensures operational continuity.
How to Achieve Cyber Resilience?
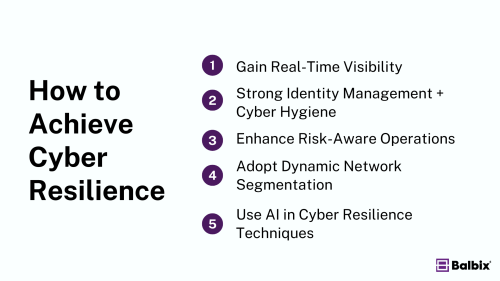
Here are five essential steps to enhance your organization’s cyber resilience:
1. Gain Real-Time Visibility
Your organization needs comprehensive visibility into its attack surface to manage cyber risks effectively. Traditional methods, like periodic vulnerability scans, are insufficient. Instead, implement advanced systems that continuously analyze your network, devices, and applications to provide real-time insights into potential threats.
Making GenAI Work for Cybersecurity
Join Nvidia and Balbix as they explore how to apply GenAI to cybersecurity, avoid common pitfalls, ensure data privacy, and uncover the true costs of building and maintaining a GenAI solution.


For large organizations, this means processing billions of data signals to accurately predict and manage breach risks. Leveraging self-learning systems for continuous observation and analysis is crucial for achieving this level of visibility.
2. Implement Strong Identity Management and Cyber Hygiene
Strong identity management is critical for securing both users and devices. This involves deploying robust authentication mechanisms and protecting user identities against theft or misuse.
Use solutions like Identity and Access Management (IAM) systems and password managers to enforce multi-factor authentication and maintain good password hygiene. Additionally, address common vulnerabilities such as unpatched systems and weak passwords to secure your internet-facing assets.
3. Enhance Core Systems Cyber Hygiene and Risk-Aware Operations
Focus on improving the security of your core systems, which are critical but not exposed to the internet. Even behind a firewall, these systems are vulnerable if compromised from the extended perimeter.
Implement risk-based vulnerability management to identify and prioritize threats based on their potential impact continuously. Automate vulnerability tracking and remediation and utilize advanced AI for effective incident response. Ensure that your Security Operations Center (SOC) can efficiently handle and analyze large volumes of security data.
4. Adopt Dynamic Network Segmentation
Network segmentation involves dividing your network into distinct zones to limit attackers’ movement. Implement segmentation to separate critical systems from less secure areas, reducing the risk of lateral movement within your network. Utilize modern segmentation solutions that dynamically adjust based on real-time risk assessments and security requirements. This approach helps create virtual barriers, making it harder for attackers to access valuable systems.
5. Advance to Sophisticated Cyber-Resilience Techniques
Take network segmentation to the next level with advanced solutions that incorporate AI for real-time risk assessments. Implement controls considering user identity, device state, and geographic location to manage access dynamically. For example, ensure that access to sensitive resources requires up-to-date authentication, device compliance, and contextual risk analysis. This comprehensive approach enhances your ability to prevent unauthorized access and manage potential threats effectively.
How Does Balbix Help Build Cyber Resilience?
Balbix enhances cyber resilience by providing a comprehensive platform for proactive risk management. Using AI and automation, Balbix continuously analyzes your entire attack surface, identifying vulnerabilities and prioritizing them based on business impact. This allows organizations to focus on the most critical risks and implement effective protection measures.
Balbix also aids in exposure management, automated response, and continuous monitoring, ensuring quick recovery and minimizing disruption from cyber incidents. Balbix simplifies governance and adapts to evolving threats by integrating with existing security tools, strengthening your overall cyber resilience strategy.
Frequently Asked Questions
- What does good cyber resilience look like?
-
Good cyber resilience encompasses a comprehensive approach to managing and responding to cyber threats. It not only involves having effective cyber defense mechanisms in place but also the ability to quickly adapt to disruptions, ensuring business continuity and the protection of data integrity.
- What are the 6 pillars of cyber resilience?
-
The six pillars of cyber resilience are identification and protection of critical assets, threat protection, detection of cybersecurity events, response to identified threats, recovery from incidents, governance, risk management, and compliance. Together, they provide a holistic framework for safeguarding against and recovering from cyber threats.
- What is the difference between cybersecurity and cyber resilience?
-
The main difference between cybersecurity and cyber resilience lies in their focus and scope. Cybersecurity primarily concentrates on preventing unauthorized access and attacks on systems and data, while cyber resilience expands this focus to include the ability to anticipate, withstand, recover from, and adapt to adverse conditions, cyberattacks, or breaches.