Cloud vulnerability management involves identifying, evaluating, and addressing security weaknesses in cloud environments. The main goal is to identify potential risks before they become security issues. A cloud vulnerability management strategy will help organizations patch vulnerabilities and update configurations by regularly scanning and assessing your cloud infrastructure.
This process isn’t just about fixing problems as they arise; it’s about being proactive. By understanding your cloud environment’s current state, you can anticipate and mitigate potential threats before they cause harm. It’s all about staying ahead in cybersecurity, ensuring your cloud resources are protected and running smoothly.
What are the Most Common Cloud Vulnerabilities?
Misconfigurations
Misconfigurations in cloud settings are like leaving your front door open—they invite trouble. Simple errors, like default or incorrect permissions or open access settings, can expose sensitive data. These oversights often occur during the setup phase, where speed can overshadow precision. Regular audits and configuration reviews can help ensure your cloud settings are secure and follow best practices.
Inadequate Access Management
Access management is crucial in cloud security. Without proper controls, unauthorized users can access sensitive information. This typically happens when permissions aren’t regularly updated, or there’s no system for removing access from former employees. Implementing strict access policies and regular audits can help prevent unauthorized access and protect your data.
Insider Threats
While we often think of threats from external sources, insider threats are just as significant. Employees with ill intent or even carelessness can cause data breaches. Organizations should ensure access is granted on a need-to-know basis and that employees are trained in security best practices. Monitoring for unusual activity can also help identify potential insider threats.
API Security Vulnerabilities
APIs are integral to cloud computing, allowing different systems to communicate. However, if not secured properly, they can become entry points for attackers. Unsecured APIs can expose sensitive data and allow unauthorized actions. To protect against this, ensure that APIs are secured with authentication and encryption and regularly test them for vulnerabilities.
Unencrypted Cloud Data
Unencrypted data is like sending a postcard through the mail—anyone can read it. Without encryption, data can be intercepted and accessed by unauthorized users. Implementing encryption in transit and at rest is essential for protecting sensitive information and complying with data protection regulations.
Lack of Visibility
You can’t protect what you can’t see. A clear view of your cloud resources is essential for effective security management. A lack of visibility means potential vulnerabilities can go unnoticed until too late. Utilize comprehensive monitoring and reporting tools to ensure a clear picture of your cloud environment.
Benefits of Cloud Vulnerability Management
Better Security and Fewer Risks
Cloud vulnerability management boosts your organization’s security by identifying and fixing weak spots. It reduces the chance of data breaches and increases your protection against cyberattacks. With this approach, you can focus on growing your business without worrying about cyber threats.
More Control and Clarity Over Cloud Environments
Good vulnerability management gives you a clearer view of your cloud setup. You can monitor activities, spot unusual behavior, and react quickly to threats. With more control, your cloud resources stay optimized and secure, helping your business run smoothly.
Building Trust With Customers and Stakeholders
A strong security setup builds trust with customers and stakeholders. When they know their data is safe, they’re more likely to do business with you. Showing your commitment to security through good vulnerability management can boost your organization’s reputation and customer confidence.
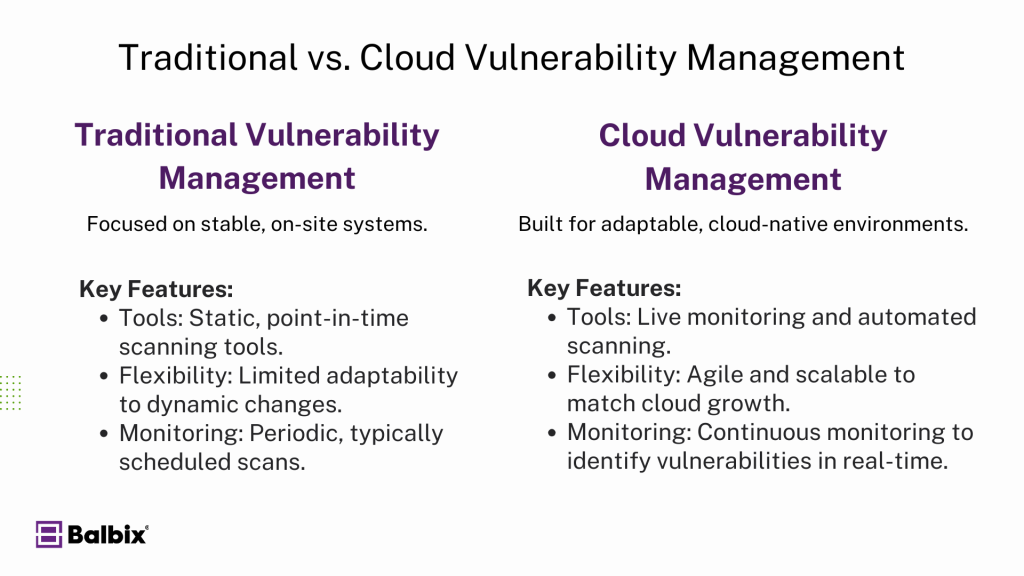
Traditional Vulnerability Management vs. Cloud Vulnerability Management
Traditional vulnerability management usually focuses on on-site systems, using tools meant for stable setups. But when dealing with cloud environments, you need tools and methods that match their ever-changing nature. You’ll want live monitoring and automated scanning to identify and fix vulnerabilities quickly.
Cloud-native solutions are key for handling vulnerabilities in the cloud. They’re built to align with cloud services, offering better growth and flexibility. This lets you adjust your security practices to tackle the unique challenges of cloud computing so your data and apps stay safe.
Key Features for Cloud Vulnerability Management Tools
Automated Scanning and Reporting
It is important to keep the data and information stored and processed within cloud tools safe; automation plays a huge part. Automated tools can regularly check your cloud setup for any weaknesses and give you updates and alerts right away. This means you can address any threats quickly, reducing the chances of data breaches and downtime.
Integration With Existing IT and Security Systems
Your tools must work well with what you already have in place. This allows you to easily share data and work together, simplifying managing weak spots across your setup. Integration helps keep things running smoothly and simplifies keeping your security plans on track.
Real-Time Monitoring and Alerts
Watching things in real time helps you spot and fix issues fast. You can act quickly to keep your data safe when you get alerts. Staying on top of things helps stop problems before they happen and keeps your cloud environment secure.
Support for Multi-Cloud Environments
Most companies use numerous cloud providers, so your tools must accommodate that. Multi-cloud support lets you manage weak spots across all your cloud environments, giving you a clear view of your security posture. With multi-cloud support, you can adhere to the same security practices and protect your data no matter where it’s stored.
Best Practices for Cloud Vulnerability Management
Keeping your data safe in the cloud is important for smooth operations. Let’s discuss a few best practices to help an organization stay secure.
- Keep Systems Updated and Patched: Keeping your systems updated is important for security. Regular updates fix known weaknesses, lowering the risk of attacks. Set up a routine for updates to keep your cloud environment safe.
- Use Strict Access Controls: Access controls protect sensitive data. Implement strict policies so only authorized users can access resources. Regularly review and update these policies to accommodate organizational changes and prevent unauthorized access.
- Conduct Frequent Security Audits: Regular security checks help find vulnerabilities in your cloud environment. Conduct these assessments regularly to confirm that your security measures are effective and current. This lets you address issues before they become major incidents.
- Educate Employees About Security Protocols: Training your team is key to good security management. Ensure your employees understand security protocols and best practices and provide regular training on the latest threats and strategies. An informed team is your first line of defense against cyberattacks.
Conclusion
Managing cloud vulnerabilities is key to keeping your cloud environment secure. Knowing common vulnerabilities and using cloud vulnerability management strategies can protect your data and support your organization’s security posture.
Balbix makes managing cloud vulnerabilities easier by constantly identifying and prioritizing risks in your cloud environment. This way, you know what needs your attention. With automated risk checks, you can fix issues faster, keeping your cloud assets safe without the hassle of manual work. Balbix also integrates seamlessly with your cloud platforms to provide real-time visibility, making it easy to stay ahead of threats.


