Cloud Security Posture Management (CSPM) refers to the process of continuously monitoring and managing the security configurations of cloud infrastructure and resources to ensure they align with an organization’s security and compliance standards.
CSPM tools automatically identify and remediate cloud misconfigurations, alerting organizations to potential vulnerabilities before attackers can exploit them. This process reduces the risk of data breaches and other security incidents by maintaining a secure cloud environment across multi-cloud and hybrid cloud setups.
Why is Cloud Security Posture Management Important?
Cloud environments offer agility and scalability but introduce unique challenges that traditional security tools may not address. The 2024 DBIR states that after misdelivery, “Misconfiguration is the next most common error and was seen in approximately 10% of breaches.”
The complexity of cloud infrastructures can lead to misconfigurations, which cybercriminals often exploit. CSPM solutions offer continuous visibility into these environments, ensuring organizations can promptly detect and correct configuration drift, compliance violations, and other risks.
1. Addressing Visibility Challenges
Due to their dynamic nature, maintaining complete visibility into resources in cloud environments takes a lot of work. CSPM tools provide continuous monitoring, helping organizations detect blind spots, such as unauthorized services or shadow IT, that could introduce security vulnerabilities and increase the risk of data loss.
2. Risk Context and Prioritization
CSPM tools prioritize based on the severity of alerts, focusing on addressing the most critical threat alerts first. This approach helps organizations to allocate resources for mitigation and remediation efforts effectively, although it doesn’t take the business criticality of workloads into account.
3. Compliance and Regulatory Requirements
As businesses move to the cloud, they must still meet strict regulatory standards such as HIPAA, PCI-DSS, and GDPR. CSPM tools automate compliance checks, enabling continuous alignment with industry regulations, reducing manual efforts, and minimizing the risk of non-compliance fines.
4. Operational Efficiency and Cost Reduction
CSPM automates the detection and remediation of security issues, reducing the workload on IT and security teams. By proactively addressing misconfigurations and risks, organizations save costs related to manual fixes and avoid potential breaches that could lead to costly recovery efforts.
How Does CSPM Work?
CSPM solutions integrate with cloud service providers (CSPs) like AWS, Microsoft Azure, and Google Cloud. They continuously scan the cloud environment, providing insights into security configurations, policy violations, and risk exposure.
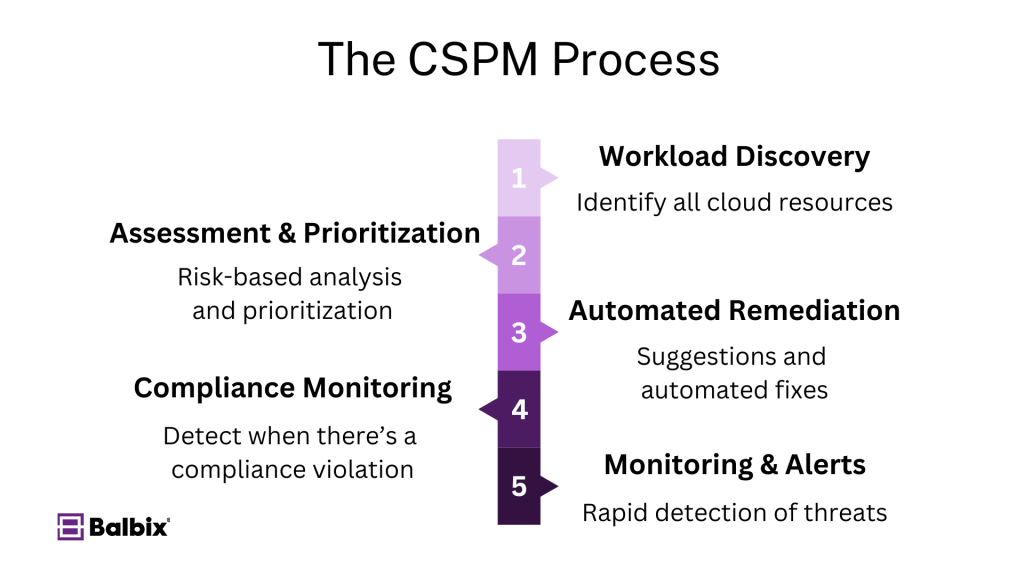
1. Workload Discovery
A primary function of CSPM tools is to discover and improve visibility into cloud workloads. CSPM tools identify all cloud resources, including virtual machines, storage services, containers, and serverless components. This real-time discovery ensures that every workload is handled properly, reducing the risk of shadow IT.
Making GenAI Work for Cybersecurity
Join Nvidia and Balbix as they explore how to apply GenAI to cybersecurity, avoid common pitfalls, ensure data privacy, and uncover the true costs of building and maintaining a GenAI solution.


These tools continuously scan cloud environments to map all workloads, applications, and configurations, ensuring no unmanaged or unauthorized workloads go unnoticed. This end-to-end visibility is crucial for accurately understanding the organization’s cloud posture.
2. Risk Assessment and Prioritization
Once all workloads are identified, CSPM tools assess security configurations for potential risks, analyzing each misconfiguration and vulnerability. As mentioned above, these tools prioritize remediation efforts based on the severity of alerts, focusing on addressing the most critical threat alerts first to enhance security efficiency and effectiveness.
3. Automated Remediation
Automation is key in modern cloud security. CSPM tools offer remediation suggestions for each identified risk and, in many cases, automated fixes.This means misconfigurations or vulnerabilities can be automatically corrected based on predefined policies, reducing human error and speeding up response times. For example, if a public-facing S3 bucket is detected in AWS, the CSPM tool can automatically reconfigure it to private access, minimizing the risk of data exposure.
4. Continuous Compliance Monitoring
CSPM tools continuously monitor cloud environments against regulatory and compliance standards, automatically generating reports and alerting security teams when a violation is detected. These tools simplify audit preparation and offer customizable policies for different regulatory standards.
5. Continuous Monitoring and Alerts
CSPM tools continuously track changes in the cloud environment, alerting security teams of new risks as they arise. This ensures rapid detection of emerging threats, enabling swift mitigation actions before a vulnerability can be exploited.
In a cloud environment where changes are frequent, CSPM tools provide continuous monitoring to detect new risks as they arise. Real-time alerts and detailed reports allow organizations to stay ahead of threats and maintain a secure cloud posture.
CSPM vs. Other Cloud Security Solutions
Understanding the differences between CSPM and other cloud security solutions helps organizations choose the right tools.
CSPM vs. Cloud Workload Protection Platform (CWPP)
While CSPM focuses on securing cloud configurations and ensuring compliance, CWPP protects individual cloud workloads such as virtual machines, containers, and serverless functions. CWPP typically includes vulnerability scanning and runtime protection, whereas CSPM focuses on misconfiguration management and policy enforcement across cloud services.
CSPM vs. Cloud Access Security Broker (CASB)
A CASB solution sits between cloud users and cloud service providers to enforce security policies related to data access and usage. CSPM, on the other hand, monitors and manages the security posture of the cloud infrastructure itself, focusing on misconfigurations and compliance at the cloud service level.
CSPM vs. Cloud Infrastructure Entitlement Management (CIEM)
CIEM focuses on managing identities, roles, and permissions within cloud environments to reduce the risk of excessive access. CSPM complements this by ensuring that infrastructure configurations are secure and compliant, but it does not focus specifically on access entitlements.
CSPM vs. Security Information and Event Management (SIEM)
CSPM addresses cloud misconfigurations and compliance, while SIEM collects and analyzes security events and logs across the organization to detect potential threats across cloud and on-premises environments.
CSPM vs. Data Security Posture Management (DSPM)
CSPM manages cloud configurations and security posture, while DSPM focuses on securing sensitive data by ensuring proper storage, access controls, and data classification.
Benefits of Cloud Security Posture Management
Organizations implementing CSPM gain significant advantages by contributing to security and operational efficiency.
- Enhanced Visibility: CSPM offers unparalleled visibility into cloud configurations, providing real-time insights into misconfigurations, risks, and compliance violations across all cloud services.
- Risk Reduction: By automatically identifying and remediating misconfigurations and vulnerabilities, CSPM tools drastically reduce the risk of data breaches, insider threats, and other security incidents stemming from poorly configured cloud environments.
- Compliance Automation: CSPM tools continuously monitor cloud environments for compliance with industry regulations, automatically generating reports and alerting security teams to violations. This reduces the burden on IT and security teams and ensures that organizations always stay audit-ready.
- Operational Efficiency: CSPM tools automate the detection and remediation of cloud security issues, enabling security teams to focus on high-priority tasks rather than manually checking configurations. This efficiency leads to reduced costs and faster response times when addressing cloud security risks.
Organizations must prioritize managing their cloud security posture as cloud adoption grows to maintain a secure, compliant, and resilient cloud infrastructure. Cloud Security Posture Management (CSPM) offers a proactive, automated approach to securing cloud environments, providing visibility into risks, automating compliance checks, and reducing the likelihood of costly security breaches.
Balbix integrates with Cloud Security Posture Management (CSPM) platforms, facilitating a cohesive inventory management system that encompasses all assets and workloads throughout the enterprise and Cloud Service Providers (CSPs). This integration empowers businesses to effectively assess and manage risks within a hybrid environment.
Frequently Asked Questions
- How long does it take to implement a CSPM solution, and what are the typical challenges during deployment?
-
Implementation timelines for CSPM vary but can range from a few weeks to several months, depending on the complexity of the cloud environment.
There are typical challenges encountered during this process, which include the need for clearly defined policies, the requirement to integrate CSPM solutions with pre-existing workflows effectively, and the necessity of aligning the automated remediation processes with the DevOps practices already in place.
To handle these challenges more effectively, a phased rollout of CSPM is often recommended. Starting to gain comprehensive visibility into the cloud environment’s security posture can help organizations mitigate deployment challenges gradually. This approach allows for a smoother transition and more effective implementation of CSPM practices.
- What are the real-world consequences of not using CSPM, and how often do misconfigurations lead to breaches?
-
Failure to use CSPM can lead to unchecked cloud misconfigurations, a leading cause of data breaches. Misconfigured cloud services, such as open storage buckets or exposed databases, can easily be exploited. Studies show that cloud misconfigurations account for a significant percentage of breaches, making CSPM critical for identifying and addressing these risks before they result in costly incidents.
- How does CSPM handle security in hybrid or multi-cloud environments?
-
CSPM is designed to provide unified visibility and risk management across hybrid and multi-cloud environments. It connects to cloud providers, such as AWS, Azure, and Google Cloud, to monitor configurations, enforce security policies, and detect misconfigurations. It integrates cloud and on-prem data in hybrid setups, ensuring consistent security posture management across all workloads.


