An advanced persistent threat (APT) is a prolonged, targeted cyberattack in which an intruder establishes an undetected presence in a network to steal sensitive data over an extended period. Unlike traditional hit-and-run attacks, APTs are characterized by their stealth, patience, and adaptability.
APTs differ from traditional cyberattacks in their complexity, persistence, and the vast resources behind them. Often sponsored by nation-states or well-funded criminal groups, APT attackers employ advanced techniques to gain a foothold in the target network and maintain long-term access.
APT attackers are usually sophisticated, well-funded teams with significant resources. These threat actors—often linked to nation-states or organized crime groups—carefully plan their attacks to infiltrate specific high-value targets such as government agencies, defense contractors, or large enterprises.
What are the Motives Behind APT Attacks?
Advanced persistent threats, or APTs, are complex cyberattacks with big goals. They often involve strategies that steal important secrets, like trade info or tech innovations, to gain power or market advantages.
APTs also aim to make money by selling stolen data or demanding ransoms, targeting the systems that keep our society running to cause disruption, and planting themselves deep within networks to stay ahead of future attacks. They can gather useful information and prepare for their next move.
While APTs have traditionally targeted government and defense sectors, the range of potential targets has expanded to include any organization with valuable data or resources. No industry is immune to this threat, from financial institutions to healthcare providers to critical infrastructure operators.
How does an Advanced Persistent Threat occur?
The primary goal of an APT is to achieve ongoing access to the targeted network rather than execute a quick smash-and-grab attack. By maintaining a persistent presence, the attackers can continuously monitor their target, intercept communications, and exfiltrate sensitive data while remaining undetected.
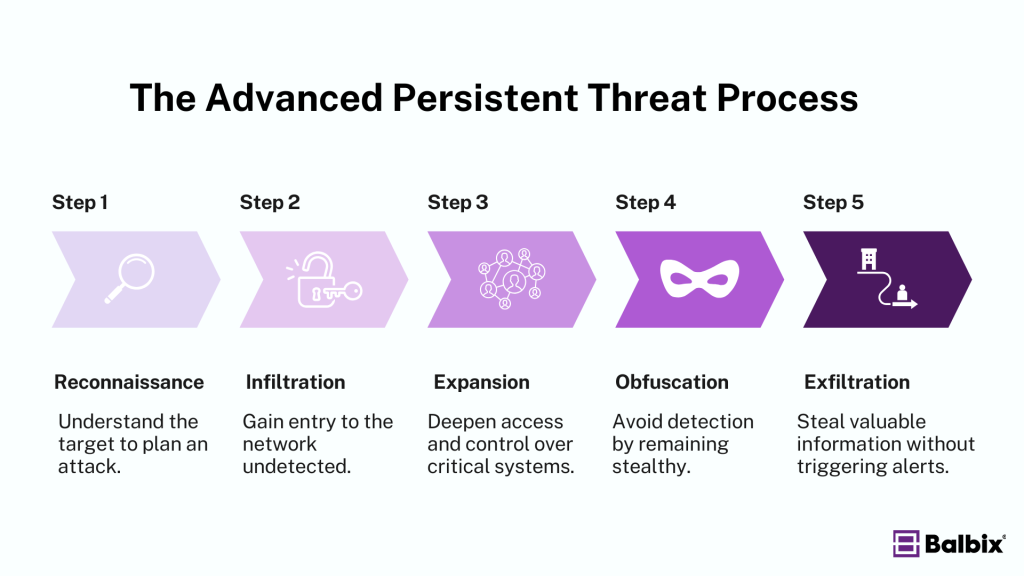
Executing an APT attack requires more time, skill, and resources than a conventional cyberattack. The process typically involves:
- Reconnaissance: Attackers conduct thorough research on the target, identifying weak points such as unpatched systems or exploitable human behaviors. This phase often involves gathering data from public sources or probing the network for vulnerabilities.
- Infiltration: Attackers gain initial access to the network by using spear-phishing emails or exploiting zero-day vulnerabilities. This step may involve tricking employees or bypassing weak security defenses.
- Expansion: Once inside, attackers deploy malware to create backdoors, escalate privileges, and move laterally through the network, gaining deeper access to sensitive systems and data.
- Obfuscation: To avoid detection, attackers use anti-forensic techniques and “living off the land” (using legitimate tools and processes) to blend in with normal activity, making it difficult for security teams to notice their presence.
- Exfiltration: Attackers gradually collect and transfer valuable data out of the network. This is often done during distraction events like DDoS attacks, which overwhelm defenses and draw attention away from the data theft.
The stealthy nature of APTs makes them particularly challenging to detect and defend against. Attackers continually adapt their tactics to circumvent security measures, often leveraging legitimate credentials and built-in system tools to blend in with regular network activity.
White Noise Attacks
A white noise attack is a cybersecurity threat where attackers flood a system with large amounts of random, meaningless data, making it harder for security tools to detect real threats.
In an advanced persistent threat (APT), a white noise attack distracts the system by flooding it with irrelevant data and overwhelming security tools and analysts. This “noise” helps hide the attackers’ activities, allowing them to move undetected, steal data, or establish control.
White noise attacks typically occur during the Obfuscation or Exfiltration stages to mask lateral movement or distract security teams while data is stolen. This tactic helps APTs stay hidden longer, making it harder for organizations to detect and respond to threats.
What are the Key Characteristics of APTs?
Advanced persistent threats (APTs) are distinguished by their calculated focus and precision. These threats are not random; they meticulously target specific organizations, with attackers dedicating substantial resources to understanding the intricacies of their intended victim’s network and defenses. The depth of reconnaissance allows attackers to pinpoint weak spots, facilitating a more effective breach.
Diverse Attack Vectors
APTs employ a sophisticated blend of techniques that extend beyond typical cyber methods. Attackers utilize a combination of digital exploits, physical intrusions, and psychological manipulation to penetrate and maintain their presence within a network.
Cyberattack tactics often involve leveraging zero-day exploits and deploying tailored malware. At the same time, social engineering and physical infiltration add additional layers of complexity, making it difficult for traditional security measures to detect and respond effectively.
Persistence and Adaptability
The hallmark of an APT is its relentless pursuit of long-term objectives. Attackers do not seek immediate gains; instead, they focus on embedding themselves deeply within the target’s infrastructure. This requires an ability to readjust strategies in response to evolving defensive measures. APT actors continuously refine their tactics to circumvent detection, often using legitimate system tools and credentials to remain inconspicuous.
Establishing Footholds
To sustain their presence, APTs strategically establish multiple covert points of entry within the network. These entry points are carefully crafted to ensure continuity of access, even if one is compromised.
Attackers can seamlessly navigate the network by employing a combination of malware and legitimate credentials, enabling them to explore and exploit additional vulnerabilities as opportunities arise. This approach secures persistent access and facilitates undetected lateral movement within the network infrastructure.
How Can Organizations Prevent APTs?
To keep advanced cyber threats at bay, companies must build a strong security plan that does more than just the basics. It’s like layering up in winter; you need multiple layers of protection working together to stay warm. This way, every part of your security system works together, making it harder for hackers to find a way in.
Use Threat Intelligence
It’s important to stay updated on the latest hacker tactics using solutions like assimilating and analyzing information on indicators of compromise (IOCs) and the tactics, techniques, and procedures (TTPs) used by adversaries so organizations can anticipate and mitigate emerging threats.
Enhanced Monitoring and Rigorous Access Controls
Solutions focused on monitoring network traffic can detect anomalies that suggest attempts at unauthorized data extraction. They help spot anything odd that might mean hackers are trying to sneak in. At the same time, enforcing stringent access controls ensures that users have the minimum access necessary for their functions, helping keep things even safer.
Active Threat Hunting and Employee Education
By actively probing for signs of APT activity, organizations can expose and address vulnerabilities that might otherwise remain hidden. Furthermore, consistent security awareness training equips employees to identify and counteract social engineering tactics. Educating staff about the latest phishing schemes and other manipulative techniques strengthens the human element of security, decreasing the likelihood of successful breaches.
However, achieving this level of protection requires a comprehensive understanding of your unique risk profile and the implementation of tailored security solutions. That’s where Balbix comes in. Request a demo today to learn more about how our platform can help you defend against APTs and strengthen your overall cybersecurity posture.
Frequently Asked Questions
- What is an example of an APT?
-
An example of an Advanced Persistent Threat (APT) is the Stuxnet worm, discovered in 2010. It targeted Iran’s nuclear facilities, specifically designed to damage centrifuges used in uranium enrichment.
Stuxnet demonstrated sophisticated techniques, including exploiting multiple zero-day vulnerabilities and being capable of spreading across networks while remaining undetected for a significant period, showcasing the characteristics of an APT. This cyber attack is notable for its complexity and the fact that it targeted industrial control systems.
- What is the typical goal of an APT?
-
The typical goal of an Advanced Persistent Threat (APT) is to stealthily infiltrate a targeted network to monitor activity and steal sensitive information over an extended period. Unlike other cyber threats, APTs focus on maintaining long-term access to the target’s environment without being detected rather than causing immediate damage or disruption. This allows attackers to regularly gather valuable data, compromising security and privacy.
- How Do Most Advanced Persistent Threats (APTs) Begin?
-
Most Advanced Persistent Threats (APTs) typically start with reconnaissance, where attackers carefully gather information about their target’s vulnerabilities. This phase often involves social engineering tactics or the exploitation of public-facing services.
Once a weakness is identified, attackers exploit it to gain initial access, setting the stage for further infiltration and establishing a foothold within the network while remaining undetected for as long as possible.


