Common Vulnerabilities and Exposures (CVE) is a publicly accessible database that identifies and catalogs known security vulnerabilities in software and hardware. Each vulnerability is assigned a unique ID, making it easier for organizations to share information, prioritize fixes, and protect their systems.
CVE helps organizations identify and prioritize security issues with documented CVE numbers and CVSS scores to plan and prioritize their vulnerability management programs.
What is the History of CVEs?
In 1999, the CVE system was established to make it easier to identify security problems. This system is managed by MITRE Corporation and supported by the U.S. government. It provides a common way to share and compare information about security issues. Before CVE, different companies had their own databases with different ways of identifying problems, making it hard to compare information. CVE fixed this by providing a standard system that everyone can use.
Although some people are worried about sharing details of problems, CVE has helped coordinate defense efforts and ensure security fixes are made quickly. CVE only includes issues that are already known to the public. Sometimes, companies keep a problem secret until they have a fix. This keeps companies safe while letting everyone share information and work together to solve problems.
What Qualifies as a CVE?
A vulnerability qualifies as a CVE if it meets specific criteria: it must be independently fixable, affect a single codebase, and be acknowledged by the vendor with documented negative security impacts. Each CVE is assigned a unique identifier to facilitate tracking and management across cybersecurity tools and platforms.
To qualify as a CVE, a vulnerability must meet all three criteria. They must be able to be fixed independently of other issues, ensuring they can be addressed without requiring changes to unrelated bugs. It also must impact only one codebase; if the same flaw affects multiple products, each product receives a separate CVE.
Additionally, the vendor must acknowledge the flaw and its potential to compromise security, or it must be documented as violating the security policy of the affected system. These criteria ensure that each CVE represents a distinct and actionable security issue, making it easier for organizations to manage their cybersecurity risks.

What is a CVE Identifier?
A CVE Identifier is a unique number assigned to a specific security vulnerability, formatted as CVE-[Year]-[Number]. Assigned by CVE Numbering Authorities (CNAs), these identifiers help standardize the tracking and management of vulnerabilities across the cybersecurity community.
CVE Identifiers ensure that each recognized vulnerability is distinct and easily traceable. The identifier format includes the year the vulnerability was reported and a sequential number assigned by the CNA.
For example, CVE-2019-0708 refers to a vulnerability in Microsoft’s Remote Desktop Protocol (RDP), commonly known as “BlueKeep.” High-profile CVEs like BlueKeep may receive informal nicknames and even custom logos, which help to raise awareness and make the vulnerabilities more recognizable in discussions among cybersecurity professionals and the media. This identification system plays a vital role in the global effort to manage and mitigate cybersecurity risks efficiently.
CVEs v. CWEs
While CVEs identify specific security flaws, CWEs (Common Weakness Enumerations) categorize the weaknesses that can lead to vulnerabilities. Think of CWE as the blueprint, describing patterns or coding errors that might result in CVEs. CWEs help security teams understand and address the underlying issues that could lead to multiple CVEs, making them essential for proactive security efforts.
Benefits of CVEs
Sharing CVE details offers significant advantages for organizations. A few of the benefits of VEs include:
- CVE IDs provide a standardized way to evaluate and compare the coverage of security tools, helping organizations determine their effectiveness.
- By referencing a specific CVE, teams can quickly access accurate information from trusted sources, enabling them to prioritize and address vulnerabilities more effectively.
- Additionally, security advisories use CVE data to identify known attack signatures, enhancing the detection and mitigation of potential threats.
Who Reports CVEs?
CVE reports are commonly submitted by researchers, white hat hackers, and vendors to a CVE Numbering Authority (CNA). These CNAs include well-known organizations like MITRE, Google, Apple, and Cisco, which collaborate to identify and document vulnerabilities. Many vendors even offer bug bounties to encourage discovering and reporting security flaws.
Anyone who discovers a vulnerability can report it to a CNA responsible for assigning a CVE identifier. Vendors often encourage the cybersecurity community to find vulnerabilities to improve their products’ security. Incentives like bug bounties and contests are frequently offered to motivate researchers and ethical hackers to participate in these efforts.
Making GenAI Work for Cybersecurity
Join Nvidia and Balbix as they explore how to apply GenAI to cybersecurity, avoid common pitfalls, ensure data privacy, and uncover the true costs of building and maintaining a GenAI solution.


The list of CNAs includes major tech companies and organizations such as Adobe, IBM, Intel, and CERT. These organizations work together to ensure vulnerabilities are documented and addressed efficiently, contributing to the overall security of digital products and services.
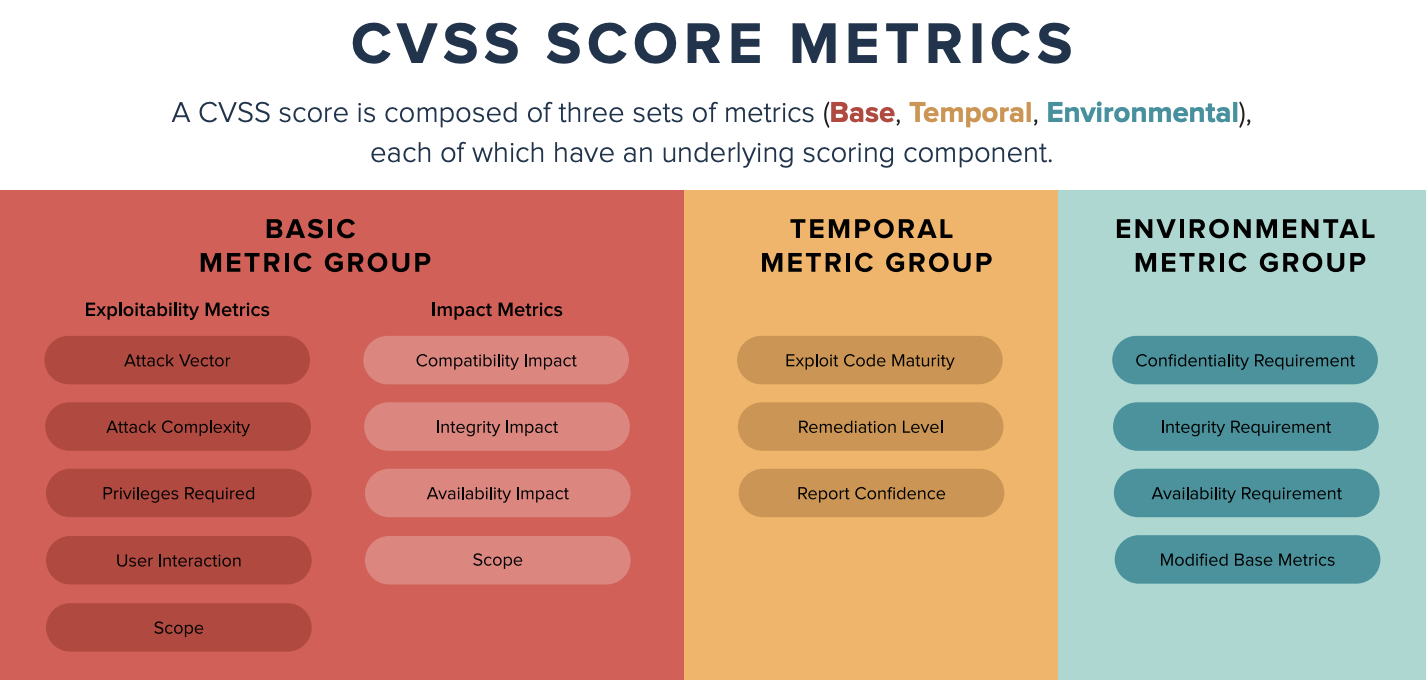
What is the Common Vulnerability Scoring System (CVSS)?
The Common Vulnerability Scoring System (CVSS) is a standardized framework for assessing the severity of security vulnerabilities. It assigns a numerical score from 0 to 10, helping organizations prioritize which vulnerabilities to address based on their potential impact. CVSS is widely used in vulnerability management to guide remediation efforts.
For more information, see our overview of CVSS scoring.
What are the Challenges of CVEs?
While CVEs are essential for identifying and tracking security vulnerabilities, they come with several challenges and limitations that organizations need to consider:
- Limited Information: CVE entries only briefly describe the vulnerability and basic references, and more comprehensive details are needed for thorough vulnerability management. Users must consult additional resources like vendor advisories or the NIST National Vulnerability Database (NVD) for more in-depth information.
- Not a Complete Vulnerability Database: CVE is not designed to be full-fledged. It serves as a standardized identifier rather than a repository of all necessary data for vulnerability management. Organizations must rely on other databases, like the NVD, for critical information such as CVSS scores, mitigation steps, and technical details.
- Focus on Unpatched Software: CVEs primarily address vulnerabilities in unpatched software, overlooking other vulnerabilities that pose risks, such as configuration issues, outdated systems, or even human factors. Modern, risk-based exposure management approaches require a broader scope that CVEs alone cannot provide.
- Exclusion of Non-CVE Vulnerabilities: Many vulnerabilities that do not fit the CVE criteria are not included in the CVE list. This exclusion can leave organizations unaware of specific risks that may not be categorized under traditional CVE definitions but still require attention to ensure comprehensive security.
- Dependency on External Sources for Complete Analysis: Since CVE entries are limited in detail, security teams must depend on external sources like the NVD or vendor websites to gather the complete information necessary for assessing and mitigating risks. This can complicate and slow down the vulnerability management process, making it harder to prioritize and address threats effectively.
Difference Between a Vulnerability and an Exposure
A vulnerability is a specific flaw in software or systems that attackers can exploit to gain unauthorized access or cause harm. Vulnerability management focuses on finding and fixing these weaknesses. Exposure, however, is a broader term that includes vulnerabilities and other risks like misconfigurations and outdated systems. Exposure management assesses all potential risks, prioritizing them based on their impact and likelihood of exploitation.
Staying Updated on CVEs
To stay updated on CVEs, regularly monitor databases like the National Vulnerability Database (NVD) or MITRE’s CVE list. Tools like vulnerability scanners and cyber risk and exposure management platforms can automate CVE tracking and assessment, providing real-time alerts for new vulnerabilities.
Subscribe to security advisories, newsletters, or RSS feeds from trusted sources to keep up with the latest CVEs. Additionally, leverage CVSS scores to prioritize and assess the impact of CVEs on your organization.
Balbix for Exposure Management
Implementing an exposure management platform like Balbix moves organizations beyond traditional vulnerability management by identifying and prioritizing CVE and non-CVE exposures. With Balbix, you can address misconfigurations, end-of-life systems, weak credentials, and more, ensuring a comprehensive approach to managing cyber risk.
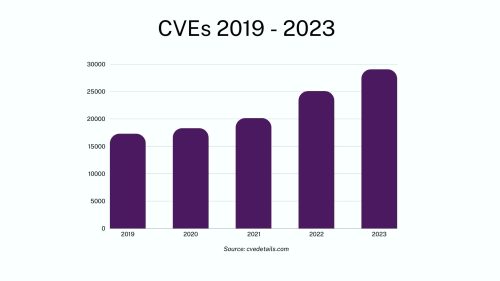
As the number of new vulnerabilities and security findings grows, managing cyber risk effectively requires identifying all CVE and non-CVE exposures and prioritizing them ruthlessly. Organizations must evolve their vulnerability management strategy to exposure management, focusing on common vulnerabilities (CVEs) and non-CVE exposures, such as misconfigurations, end-of-life systems, application security findings, weak and stolen credentials, control gaps, and user risks.
Learn more in our Exposure Management article.
The Future of CVEs
The future of CVEs will likely involve more regulation and standardization, driven by the growing need for comprehensive cybersecurity measures. AI and machine learning will play a key role in automating the detection, tracking, and prioritization of CVEs, making it easier to manage vulnerabilities. Additionally, as exposure management becomes more prominent, organizations may focus on non-CVEs, like configuration errors or other security gaps, to build a more holistic defense strategy.
Frequently Asked Questions
- What does CVE stand for?
-
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures.
- When would you use CVE?
-
By using the CVE ID for a particular vulnerability or exposure, organizations can quickly and accurately obtain information about it from a variety of information sources and coordinate their efforts to prioritize and address these vulnerabilities to their organizations more secure.
- Does every vulnerability have a CVE?
-
No, not every vulnerability has a CVE (Common Vulnerabilities and Exposures) identifier. CVEs are assigned to publicly known vulnerabilities noted as significant enough to be tracked and addressed. Many vulnerabilities, especially those in less widely used software or those not yet discovered, might not have a CVE. Organizations often use other methods for identifying and managing vulnerabilities in these cases.
- What is the Difference Between CVE and CVSS?
-
CVE is the database of known vulnerabilities and exposures. Every entry in that database has a corresponding CVSS score. The CVSS score calculates the severity of the CVE. For a more in-depth analysis of the differences between CVE and CVSS, check out this link.