A vulnerability assessment is a process that identifies, classifies, and addresses security weaknesses in an organization’s IT systems. It’s akin to a routine health check for cybersecurity defenses. Organizations can fix these issues by uncovering vulnerabilities—such as outdated software, misconfigurations, or security gaps—before they become opportunities for attackers.
How Does a Vulnerability Assessment Work?
The vulnerability assessment process typically involves these steps:
1. Identification
The first step is to scan your network, systems, and applications for known vulnerabilities. Automated tools compare your systems against a database of known security flaws.
2. Classification
Not all vulnerabilities are equally dangerous. After identifying potential issues, the next step is to classify them based on their severity and exploitability. For instance, vulnerabilities that allow remote code execution are more critical than those requiring physical access.
3. Analysis
Here, the identified vulnerabilities are analyzed to understand their potential impact. This involves evaluating whether they could lead to data breaches, financial losses, or operational disruptions.
4. Remediation
The final step involves addressing the identified vulnerabilities. This may include applying patches, reconfiguring systems, or enhancing security controls. Critical vulnerabilities should be addressed immediately, while less severe issues can be scheduled for future remediation.
5 Signs Your Organization Needs a Vulnerability Assessment
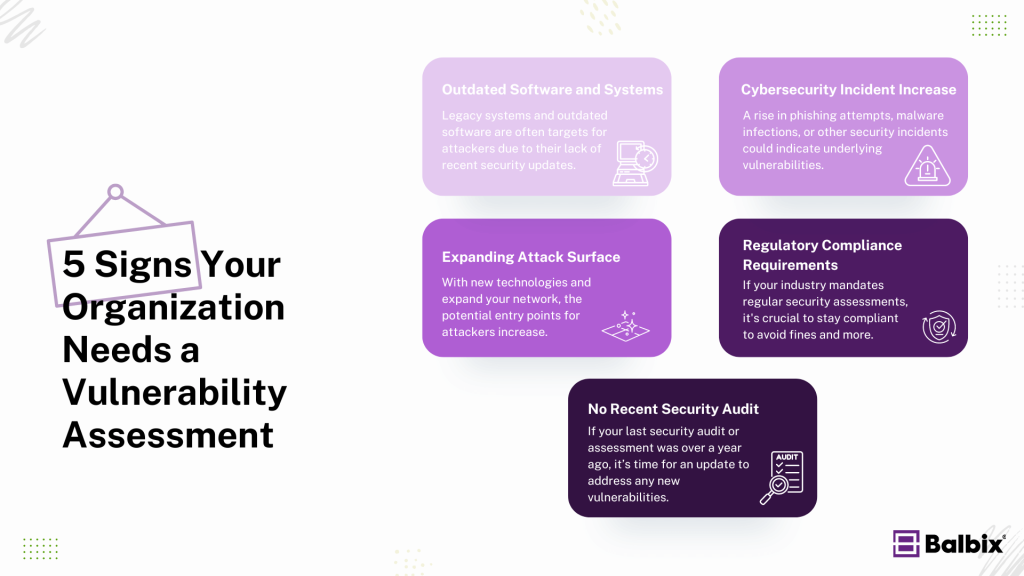
Not sure if it’s time for a vulnerability assessment? Look for these signs:
- Outdated Software and Systems
Legacy systems and outdated software are often targets for attackers due to their lack of recent security updates. - Increase in Cybersecurity Incidents
A rise in phishing attempts, malware infections, or other security incidents could indicate underlying vulnerabilities. - Expanding Attack Surface
As you adopt new technologies and expand your network, the potential entry points for attackers increase, making regular assessments essential. - Regulatory Compliance Requirements
If your industry mandates regular security assessments, it’s crucial to stay compliant to avoid fines and more. - No Recent Security Audit
If your last security audit or assessment was over a year ago, it’s time for an update to address any new vulnerabilities.
Types of Vulnerability Assessment Tools
Several tools are used to perform vulnerability assessments, each focusing on different security aspects to provide a comprehensive view of potential weaknesses. Here’s a closer look at the main types:
1. Network-Based Scanners
Network-based scanners are designed to examine an organization’s network infrastructure for vulnerabilities. These tools perform the following functions:
- Port Scanning: Identifies open ports on networked devices, which could be potential entry points for attackers if not properly secured.
- Service Detection: Determines which services and applications are running on open ports, helping to identify outdated or vulnerable services.
- Configuration Checks: Assesses network devices like routers and firewalls for misconfigurations that could expose the network to attacks.
- Vulnerability Identification: Compares the discovered services and configurations against a database of known vulnerabilities to flag potential risks.
2. Host-Based Scanners
Host-based scanners focus on individual servers, workstations, and other devices within your network. These tools are used to:
- Scan for Unpatched Software: Detect outdated software and operating systems that may have known vulnerabilities.
- Check System Configurations: Evaluate system settings and configurations to identify potential security weaknesses or compliance issues.
- Analyze File Integrity: Monitor critical files and directories for unauthorized changes or signs of tampering.
- Detect Malware: Identify malware infections or suspicious activities that could compromise system security.
3. Application Scanners
Application scanners are specialized tools that assess the security of web applications. They focus on:
- Static Analysis: Examines application code without executing it to find vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure direct object references.
- Dynamic Analysis: Tests the application while running to detect issues such as session management problems and runtime vulnerabilities.
- API Security Testing: Evaluates the security of application programming interfaces (APIs) for issues like insecure data handling and improper authentication.
4. Database Scanners
Database scanners are designed to analyze the security of databases, which are critical for storing sensitive information. They focus on:
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

- Configuration Reviews: Checks for misconfigurations that could expose the database to unauthorized access or attacks.
- Data Encryption: Ensures that sensitive data is encrypted both in transit and at rest to protect it from unauthorized access.
- User Privileges: Reviews database user accounts and permissions to ensure that users have the appropriate level of access and that overly permissive accounts are restricted.
- Patch Management: Identifies outdated database software that may have known vulnerabilities.
5. Cloud-Based Scanners
With the growing adoption of cloud computing, cloud-based scanners are becoming increasingly important. They focus on:
- Cloud Configuration Checks: Assesses cloud infrastructure settings to identify misconfigurations that could lead to security breaches.
- API Security: This function evaluates the security of cloud-based APIs to ensure they are protected against unauthorized access and data leakage.
- Identity and Access Management (IAM): Reviews cloud user permissions and access controls to prevent unauthorized access to cloud resources.
- Cloud Service Provider (CSP) Security: Analyzes the security posture of cloud services provided by third-party vendors to ensure they meet security standards.
Consider More than a Vulnerability Assessment
Organizations should consider more than just a vulnerability assessment because vulnerabilities evolve, and new threats emerge continuously. A one-time assessment may not capture these dynamic changes.
Ongoing monitoring with Balbix provides continuous visibility into your security posture, automatically identifying and prioritizing emerging threats and vulnerabilities. This proactive approach ensures timely responses to new risks, maintains compliance and protects against evolving cyber threats. Balbix’s real-time insights and automated risk management help organizations stay ahead of attackers and continuously fortify their defenses.
Frequently Asked Questions
- What are the key differences between network-based, host-based, and application scanners, and how do I choose the right one for my organization?
-
Network-based scanners look for vulnerabilities in your entire network, host-based scanners focus on specific devices or servers, and application scanners check for weaknesses in web applications.
Choosing the right one depends on what you’re safeguarding. If it’s your overall network, go with network-based. If you’re concerned about individual computers or servers, host-based is better. And if web apps are your main concern, application scanners are the way to go.
- Can vulnerability assessments be conducted internally, or is it recommended that external experts be hired for a more unbiased evaluation?
-
Vulnerability assessments can be done both internally and by hiring external experts. Doing it internally saves money and utilizes in-house knowledge.
However, external experts provide a fresh, unbiased perspective and may identify issues that internal teams overlook. So, the choice depends on the organization’s specific needs, budget, and the criticality of what’s being assessed.
- How do vulnerability assessments integrate with other cybersecurity practices, such as penetration testing and incident response planning?
-
Vulnerability assessments are like checking your house for weak spots where a thief could break in. They help find these weaknesses so you can fix them. This is the first step.
Then, penetration testing is like having a friend try to break in to see if the fixes worked. It’s a test attack to make sure your defenses are strong.
Lastly, incident response planning is like having a plan ready in case someone does break into your house, so you know exactly what to do to minimize damage and recover quickly. Together, these practices make your cybersecurity much stronger.