The Common Vulnerability Scoring System (CVSS) is a standardized framework for measuring information systems’ severity of security flaws. It assigns each vulnerability a score between 0 and 10, with higher scores meaning more severe issues. This system helps organizations decide which security threats need attention first based on their potential impact.
How does CVSS Scoring Work?
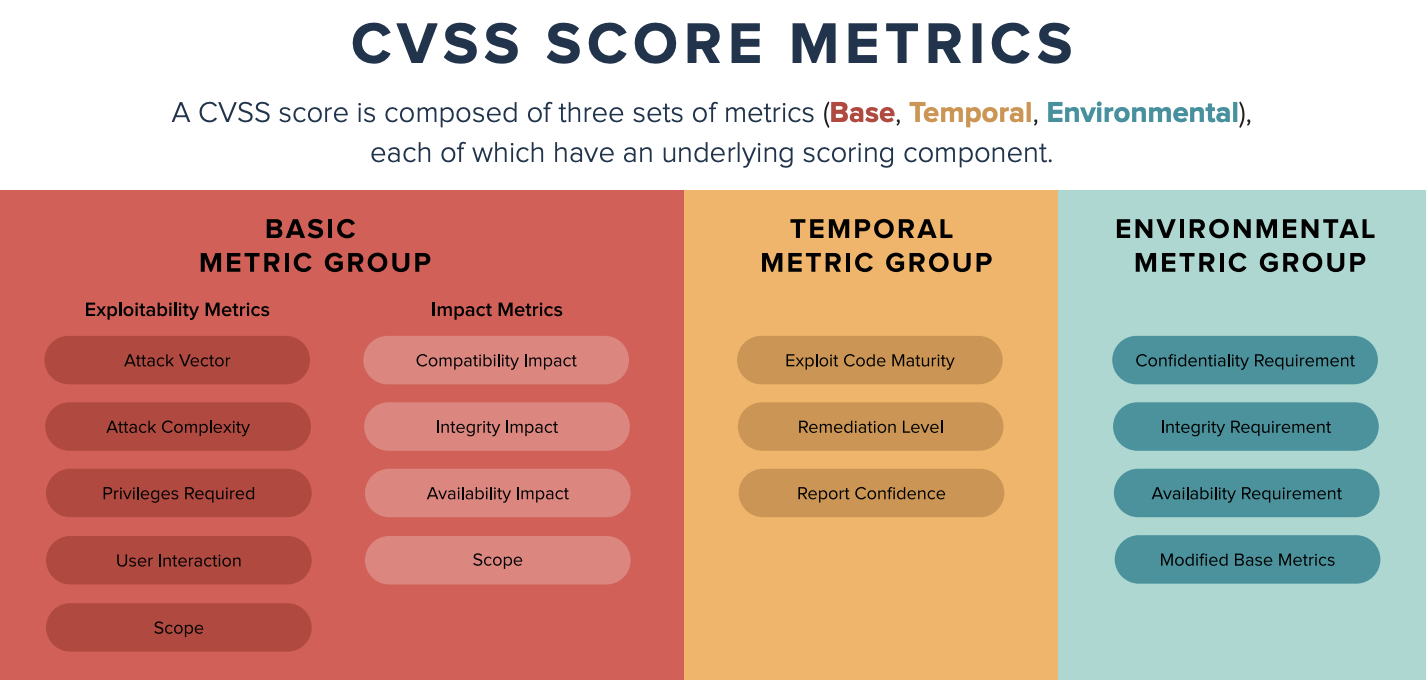
CVSS scoring assigns a number from 0 to 10 based on three main factors: Base, Temporal, and Environmental metrics. The Base score shows the inherent characteristics of a vulnerability. The Temporal score considers how those characteristics may change over time. The Environmental score evaluates how the vulnerability could affect a specific environment.
| CVSS Score | Qualitative Rating |
| 0.0 | None |
| 0.1 – 3.9 | Low |
| 4.0 – 6.9 | Medium |
| 7.0 – 8.9 | High |
| 9.0 – 10.0 | Critical |
A score of 0 means the vulnerability has minimal severity, while a score of 10 represents the most severe issues. This scoring helps organizations prioritize their responses to different security threats.
How is a CVSS score calculated?
A CVSS score is based on three sets of metrics: Base, Temporal, and Environmental. Each of these has its own scoring elements.

CVSS Base Metrics
The Base Metrics are the core components used to determine how severe a security vulnerability is. They focus on the vulnerability’s characteristics, regardless of whether it has been exploited or mitigated. These metrics include Exploitability, Scope, and Impact.
Exploitability: This metric assesses how easily a vulnerability is exploited. It is broken down into four sub-components:
- Attack Vector: Measures how an attack can be executed, with higher scores for remote attacks versus those requiring physical access.
- Attack Complexity: Evaluate the difficulty of executing the attack, with lower scores for easier vulnerabilities to exploit.
- Privileges Required: This indicator indicates the level of access needed to exploit the vulnerability, with higher scores for attacks requiring fewer privileges.
- User Interaction: Considers whether the attacker needs to involve a user in the exploit, with autonomous attacks scoring higher.
Scope: This metric assesses whether the vulnerability can affect other components beyond the initial target. The score will be higher if the vulnerability can propagate, such as compromising an entire system through a single application flaw.
Impact: This metric evaluates the potential consequences of a successful exploit, focusing on three areas:
- Confidentiality: Measures the extent of data exposure.
- Integrity: Assesses the ability of the attacker to modify data.
- Availability: Evaluate the potential disruption to system access and functionality.
While CVSS-based Base Metrics provide a crucial starting point for understanding a vulnerability’s severity, they have limitations. They do not account for Temporal Metrics, which change over time, or Environmental Metrics, which reflect an organization’s specific context, such as existing security controls and asset criticality.
Organizations must consider these additional factors to fully assess and prioritize vulnerabilities, which can significantly alter the perceived risk and required response.
CVSS Temporal Metrics
CVSS Temporal Metrics evaluate the changing nature of a vulnerability over time. These metrics assess a vulnerability’s current exploitability and the availability of remediating controls, such as patches. Key subcomponents of Temporal Metrics include:
- Exploit Code Maturity: A vulnerability is less threatening until a method to exploit it becomes available. As exploit code matures and becomes more widespread, its associated score increases, reflecting the heightened risk.
- Remediation Level: A vulnerability may not initially have a patch or workaround. As temporary fixes or official patches are released, the vulnerability score decreases, indicating reduced risk.
- Report Confidence: This measures how well a vulnerability is validated, ensuring it is both real and exploitable—higher confidence results in a higher score.
CVSS Environmental Metrics
CVSS Environmental Metrics allow organizations to adjust the Base CVSS score based on their specific Security Requirements and modifications of Base Metrics.
- Security Requirements: These metrics consider the criticality of the affected asset. Mission-critical systems, like a database containing all customer data, receive higher scores than less critical assets, such as a non-privileged user’s workstation.
- Modified Base Metrics: Organizations can modify Base CVSS Metrics based on existing mitigations. For instance, “air gapping” a server—disconnecting it from external networks—lowers the Attack Vector score since remote exploitation is no longer possible.
By considering both Temporal and Environmental Metrics, organizations can achieve a more tailored and accurate assessment of a vulnerability’s actual risk to their specific environment.
History of the CVSS
CVSS has been crucial to assessing vulnerabilities since 2003/2004 when it was introduced by the National Infrastructure Advisory Council (NIAC). Since 2005, it’s been managed by the Forum of Incident Response and Security Teams (FIRST). The latest version, CVSS v4.0, was released in 2023 to improve scoring accuracy and address user feedback.
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

Despite its importance, CVSS has faced criticism. Some argue it oversimplifies the complex nature of vulnerabilities, especially in earlier versions. Even with improvements in v4.0, the system can still overwhelm security teams with high-severity vulnerabilities that may not be the most urgent.
Organizations now complement CVSS with additional metrics and systems, such as the Exploit Prediction Scoring System (EPSS) and Risk-Based Vulnerability Management (RBVM). EPSS predicts the likelihood of exploiting a vulnerability, while RBVM considers business impact, asset criticality, and existing security controls. These methods offer a more tailored approach to vulnerability prioritization.
CVSS vs. CVE
The main difference between CVSS and CVE lies in their roles. CVE (Common Vulnerability Enumeration) gives unique identifiers to specific security vulnerabilities, making them easier to track. CVSS (Common Vulnerability Scoring System) provides a score that shows how severe each CVE is. For example, the Heartbleed vulnerability (CVE-2014-0160) has a CVSS score 7.5, indicating high severity.
CVSS Limitations
The Common Vulnerability Scoring System (CVSS) has several limitations that organizations need to consider:
- Limited Context: CVSS scores don’t account for the specific risks to your organization. They tell you if a vulnerability is dangerous, but not if it’s dangerous to you.
- Example: Suppose two organizations—a financial institution and a small retail store—face the same vulnerability. CVSS might rate it as severe, but for the retailer, the risk might be minimal due to fewer sensitive assets, whereas for the financial institution, it could be critical due to the high value of their data.
- Subjectivity: CVSS scores can vary depending on the context, leading to inconsistencies.
- Example: A vulnerability in a widely used software might receive a high CVSS score based on its potential impact. However, the risk might be lower if a company has strong security operation controls. Yet, another organization with weaker controls might find the same vulnerability far more threatening, leading to different assessments.
- Limited Scope: CVSS doesn’t fully consider the importance of specific assets or existing controls.
- Example: CVSS might score a vulnerability in an out-of-date software as low because it’s not internet-facing. However, if that software version is critical to a company’s operations, the low score underestimates the risk, missing the asset’s importance.
- Complexity: The system requires a deep understanding of scoring factors. Understanding how to calculate and interpret CVSS scores requires familiarity with several factors, such as attack vectors, complexity, and impact.
- Example: This complexity can lead to misinterpretations or misuse of scores for organizations without dedicated security expertise.
- Potential for Oversights: Relying solely on CVSS scores can lead to missed opportunities to address the most pressing threats.
- Example: If an organization relies solely on CVSS scores, it might overlook threats that don’t score highly but are significant in their specific context—like vulnerabilities in internal systems that an insider could exploit.
Organizations should adopt a risk-based vulnerability management approach incorporating CVSS Base Scores and Temporal and Environmental factors to address these limitations. This tailored approach requires understanding the organization’s risks, including business criticality, existing controls, and the current threat landscape.
Frequently Asked Questions
- What is the purpose of the CVSS calculator?
-
The CVSS (Common Vulnerability Scoring System) calculator assesses the severity of vulnerabilities by providing a numerical score based on various metrics. This score helps organizations prioritize vulnerabilities based on their potential impact and exploitability.
- Is CVSS a risk score?
-
CVSS is not a risk score; it measures the severity of vulnerabilities. While it provides a numerical score indicating the potential impact, it does not account for an exploit’s specific context or likelihood.
- Is CVSS a threat model?
-
CVSS is not a threat model. It is a scoring system that quantifies the severity of vulnerabilities but does not comprehensively analyze threats or their interactions with vulnerabilities.
- What is the main reason for performing vulnerability assessment?
-
The main reason for performing a vulnerability assessment is to identify and evaluate security weaknesses in a system. This helps organizations prioritize remediation efforts, reduce risk, and enhance their overall cybersecurity posture.