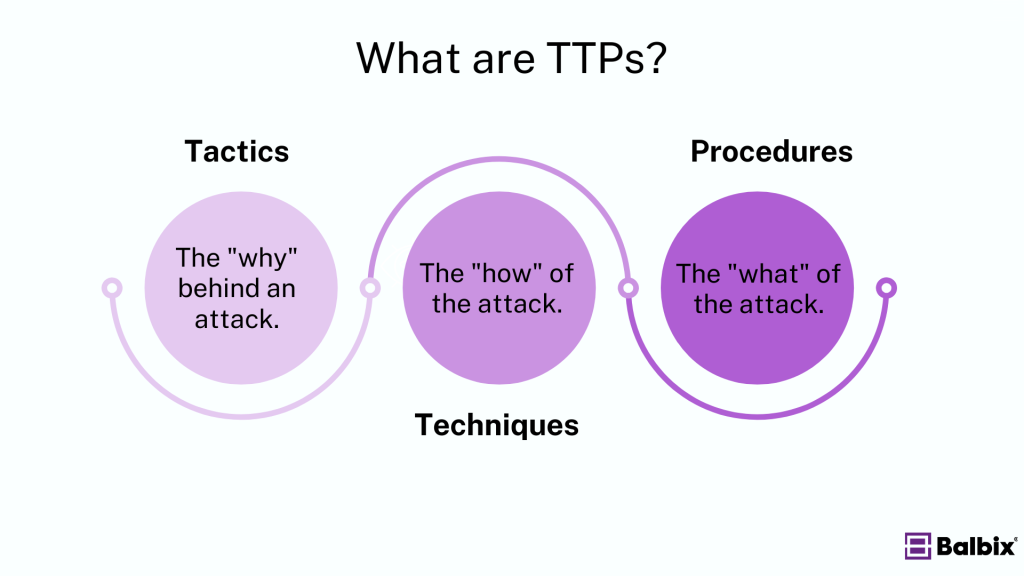
TTPs in cybersecurity describe how cybercriminals plan and execute attacks. Each component, named tactics, techniques, and procedures, offers insight into different layers of an attack, helping security teams understand and counteract potential threats.
- Tactics: The overarching goals and objectives of an attacker. These are the “why” behind the attack.
- Techniques: The methods attackers use to achieve their goals. These are the “how” of an attack.
- Procedures: The specific actions taken to implement techniques. These are the “what” of the attack at a granular level.
Understanding these components provides a blueprint for how adversaries think and operate, allowing organizations to build more robust defenses.
Breaking Down Each TTP Component
Tactics
Tactics in TTPs refer to the general objectives or strategies cybercriminals want to achieve during an attack. Tactics provide a high-level understanding of an attack’s overall direction. For example, they may seek initial network access, maintain persistence, escalate privileges, or exfiltrate sensitive data.
Techniques
Techniques in TTPs are the specific methods attackers employ to execute their chosen tactics. For instance, an attacker might use phishing to gain access to a network or leverage credential dumping to escalate privileges. Techniques show us how attackers attempt to achieve their goals and help organizations focus on preventing these methods.
Procedures
While techniques describe “what” attackers do, procedures provide detailed insights into how they do it. Procedures are the step-by-step actions attackers take to execute their strategies. For example, attackers might use specific malware, scripts, or tools to carry out their activities.
Why Understanding TTPs Matters
Cybercriminals are constantly evolving their methods, and here’s why understanding TTPs is essential for protecting organizational assets and data:
- Proactive Threat Detection: By understanding common TTPs, security teams can anticipate how attackers might behave and implement countermeasures before an attack occurs.
- Improved Incident Response: Recognizing the TTPs used in an ongoing attack enables security teams to respond faster and more effectively. They can isolate affected systems and mitigate damage.
- Enhanced Threat Hunting: Knowing TTPs allows for more focused threat-hunting efforts. Security teams can proactively search for indicators of compromise based on known TTP patterns.
- Strengthened Cyber Defense: TTPs can guide the development of more robust security policies, ensuring that preventive measures are tailored to specific threat actors and their methods.
- Adversary mindset: Threat actors will reuse successful TTPs against new targets to gain a foothold in an organization’s assets.
In short, understanding TTPs allows organizations to shift from reactive to proactive security, reducing the likelihood of a successful attack.
How TTPs Work in Practice
TTPs are used by both attackers and defenders in the cybersecurity ecosystem. Attackers rely on well-developed TTPs to execute their campaigns, while defenders use them to analyze, predict, and counteract malicious activity.
Examples of TTPs in Action
- Phishing is a common tactic for tricking individuals into revealing sensitive information. The technique might involve sending fraudulent emails that appear legitimate, and the procedure could include using a specific email template or spoofing tool.
- Privilege Escalation occurs when attackers often seek to escalate their privileges within a network to access more sensitive data. A common technique for this tactic is credential dumping, where attackers extract passwords and hashes. The procedure may involve running specific scripts or malware designed to target Windows or Linux systems.
TTPs and Threat Intelligence
Threat intelligence frameworks, such as MITRE ATT&CK and MITRE D3FEND, help categorize TTPs and help organizations map out potential threats. These frameworks provide a shared vocabulary for cybersecurity teams, making it easier to understand and defend against specific attack methods.
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

MITRE ATT&CK is one of the most widely used threat intelligence tools, categorizing TTPs into various stages of an attack—from initial access to data exfiltration—helping organizations monitor, detect, and respond to threats based on real-world data.
CVE (common vulnerabilities and exposures) help an attacker determine what tools or methods will be successful in the target environment.
How Cybersecurity Professionals Use TTPs
Cybersecurity teams leverage TTPs in several ways to improve security posture and reduce risks:
- Behavioral Analysis: Cybersecurity professionals can detect abnormal behaviors that indicate a potential attack by monitoring known TTP patterns.
- Incident Response Plans: TTP knowledge informs the development of incident response playbooks, allowing teams to act quickly when specific attack patterns are detected.
- Sharing Threat Intelligence: Organizations share TTPs through threat intelligence networks, which helps to broaden the understanding of emerging threats and ensure cybersecurity strategies are continuously updated.
- Penetration Testing: Ethical hackers use TTPs to simulate real-world attacks during penetration testing, allowing organizations to identify and fix vulnerabilities before they can be exploited.
- Attack Path Understanding: The Balbix platform can assist in this task by understanding a TTP and using a CVE’s security teams to identify landing zones for threat actors.
Understanding TTPs is more crucial than ever. It allows security teams to anticipate potential attacks, respond quickly to incidents, and build more effective defenses.
Cybersecurity professionals can better protect their organizations from increasingly sophisticated cyber threats by leveraging tools like the MITRE ATT&CK framework and staying informed on adversaries’ latest TTPs. As CVEs change over time, the methods (TTPs) and attack tooling will remain constant.
Frequently Asked Questions
- What are TTPs in ransomware?
-
TTPs in ransomware are Tactics, Techniques, and Procedures.
- Tactics are their overall strategies, like how they plan their attacks.
- Techniques are the specific methods they use, such as phishing emails to trick people.
- Procedures are the step-by-step actions they take to carry out their plans, like encrypting files to demand a ransom. It’s like understanding the moves of a chess opponent to better defend against them.
- What is an example of TTP in cyber?
-
A cybersecurity example of a TTP is when an adversary may use brute force techniques to access accounts with unknown or encrypted passwords.
Another example of TTP would be phishing emails. Hackers use this technique to trick individuals into revealing personal information by sending emails that appear legitimate but are actually malicious.
- What is the difference between tactics and techniques?
-
Tactics and techniques may seem similar, but they’re actually different. Think of tactics as the overall plan or strategy used to achieve a goal—like the game plan a coach devises for a team.
Techniques, on the other hand, are the specific skills or methods used to execute that plan. Imagine the individual moves a player practices, like dribbling or shooting in basketball. Tactics set the direction, while techniques are about execution.