Patch management is a crucial process in cybersecurity that involves updating and applying software patches to fix vulnerabilities, enhance functionality, and ensure compliance. These patches—typically released by software vendors—address security flaws, bugs, and performance issues, providing critical updates to maintain a secure and efficient IT environment. Effective patch management minimizes the risk of cyberattacks by ensuring that systems are always up to date with the latest protections.
This article will cover the importance of patch management, its lifecycle, benefits, best practices, and how it compares to vulnerability management.
Why is Patch Management Important?
Patch management plays a critical role in safeguarding your organization’s IT infrastructure. It reduces the risk of cyber threats, protects sensitive data, and ensures compliance with evolving regulations. A few important benefits of patch management include:
- Strengthened Security: Cybercriminals actively seek out unpatched vulnerabilities to exploit. Regular patching significantly reduces the attack surface, blocking potential threats before they can infiltrate your network.
- System Stability & Uptime: Unpatched software is more prone to crashes and performance issues. Applying patches ensures smoother, more reliable operations, minimizing unexpected downtime that can disrupt critical services.
- Regulatory Compliance: Many industries enforce strict compliance standards, such as GDPR, HIPAA, and PCI DSS, requiring timely patching. A consistent patch management process prevents regulatory fines and fosters trust among customers and stakeholders.
- Optimized Performance & Features: Patches aren’t just about security. They often deliver performance enhancements and feature updates, ensuring your systems run efficiently and leverage the latest innovations.
- Cost Savings: The costs of cyberattacks and downtime can be astronomical, from lost revenue to recovery expenses. Effective patch management reduces the likelihood of these incidents, resulting in long-term savings and fewer operational headaches.
The Patch Management Lifecycle
Patch management is a continuous process that involves several steps to ensure patches are identified, prioritized, tested, and applied efficiently across an organization. Below is an overview of the patch management lifecycle:
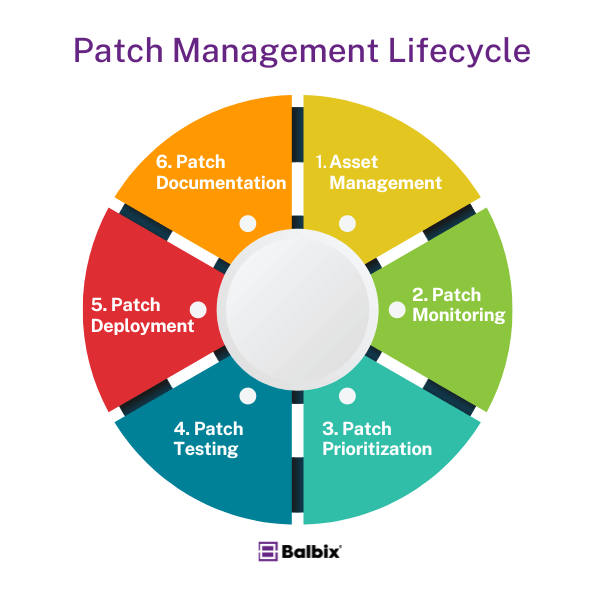
1. Asset Management
The first step in patch management is understanding what needs to be patched. This requires creating a comprehensive inventory of all hardware and software within the organization. Critical systems should be prioritized based on their role in business operations and risk profile.
2. Patch Monitoring
Once assets are identified, the next step is to monitor for available patches. Software vendors frequently release updates, so it’s essential to stay informed by monitoring vendor sites, subscribing to security bulletins, and utilizing automated tools to detect new patches.
3. Patch Prioritization
Not all patches need to be applied immediately. Organizations must prioritize patches based on the severity of the vulnerability, the system’s criticality, and the potential impact of exploitation. This involves analyzing the Common Vulnerability Scoring System (CVSS) scores and the affected system’s business context.

4. Patch Testing
Before applying patches to production systems, they should be tested in a controlled environment to ensure they don’t introduce new problems, such as compatibility issues or performance degradation. This testing phase helps minimize the risk of disrupting operations when deploying patches.
5. Patch Deployment
After successful testing, patches can be deployed to production systems. Rolling out patches in stages minimizes user impact and quickly addresses any issues. Scheduling deployments during off-peak hours can also reduce disruptions to critical business processes.
6. Patch Documentation
To maintain accountability and ensure compliance, all patching activities should be documented. This includes details on which patches were applied when deployed and the testing results. Proper documentation helps streamline audits and provides insight into the effectiveness of the patch management process.
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

Patch Management vs. Vulnerability Management
While patch management focuses on updating software to fix known issues, vulnerability management is a broader process that involves identifying, assessing, and mitigating vulnerabilities across an organization’s systems.
Here’s how the two differ:
- Patch Management primarily involves applying software patches to fix security flaws and bugs. It is a subset of the more extensive vulnerability management process.
- Vulnerability Management involves identifying vulnerabilities through continuous monitoring, assessing their risk to the organization, and taking appropriate actions, such as patching, applying compensating controls, or accepting the risk.
The two processes complement each other, with vulnerability management helping to identify and prioritize patches in the patch management lifecycle.
Patch Management Best Practices
To ensure your patch management process is effective and efficient, follow these best practices:
Inventory of IT Assets: Maintain an up-to-date inventory of all software and hardware assets. Knowing exactly what you need to patch is essential for ensuring comprehensive coverage.
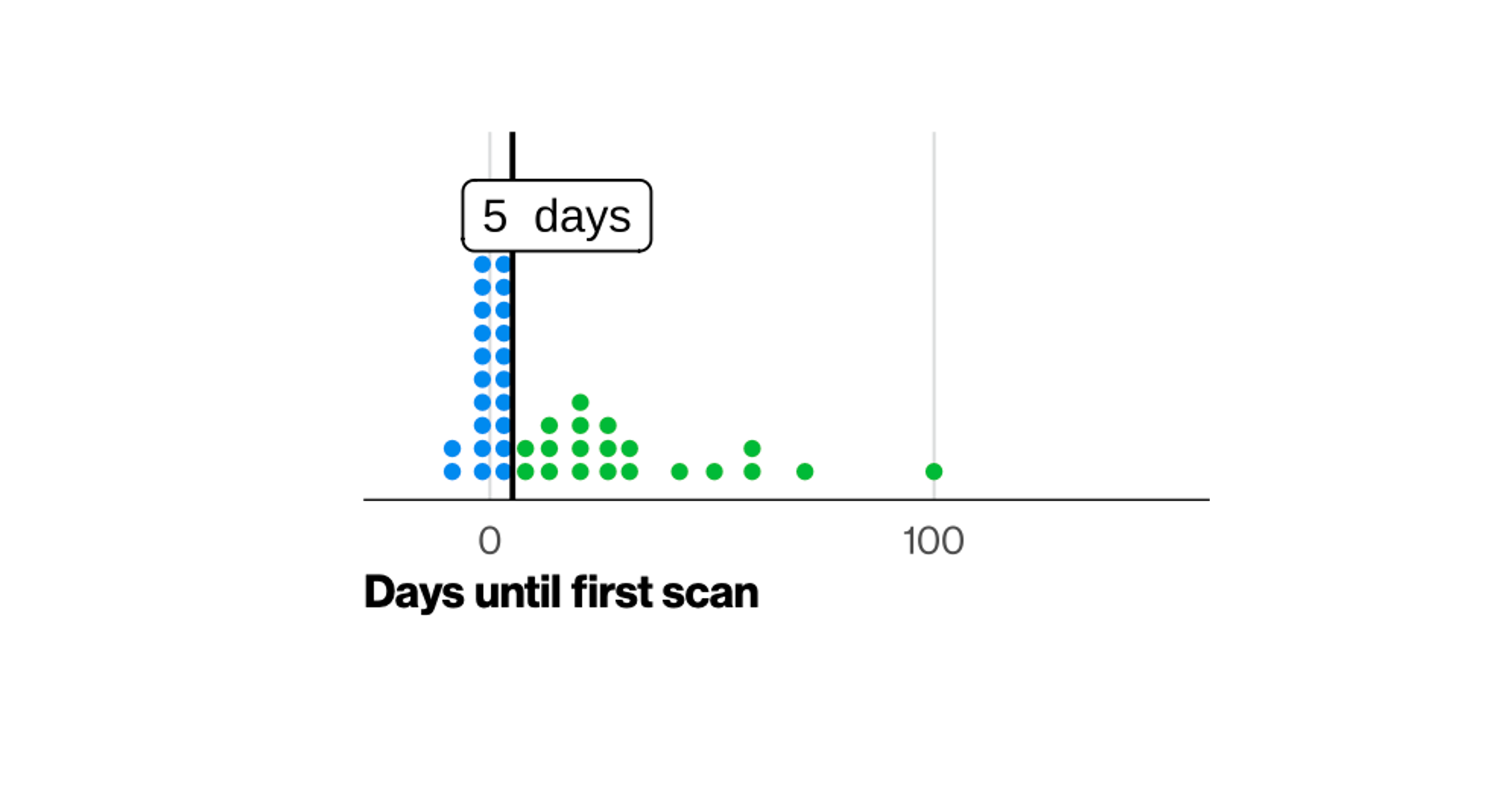
Regular Vulnerability Scanning: Use automated vulnerability scanning tools to identify missing patches and monitor your systems’ security posture. Regular scans help ensure that no critical vulnerabilities slip through the cracks.
Prioritize Patches by Risk Level: Not all patches are equal. Use risk-based prioritization to ensure that critical vulnerabilities are addressed first. Consider factors like CVSS scores, the potential business impact of exploitation, and the importance of the affected system.
Test Patches in Controlled Environments: Always test patches before deploying them to production environments. This helps prevent issues like software conflicts, performance degradation, or unintended consequences.
Collaborative Patch Deployment: Ensure that IT and security teams collaborate during the patch deployment. Open communication can address any issues quickly and ensure the patching process runs smoothly.
Create a Recovery & Rollback Plan: Have a contingency plan in place in case patches cause problems. A rollback plan allows you to quickly revert to the previous state, minimizing downtime and disruption.
Challenges of Patch Management
Despite its importance, patch management comes with challenges:
- Patch Delays & Missed Deadlines
Maintaining patch schedules can be challenging due to the sheer volume of patches, limited resources, or conflicting priorities. - System Compatibility Issues
Patches can sometimes cause compatibility or performance problems, especially with legacy systems. - Resource Constraints
Smaller organizations may need more personnel or budget to manage patching efficiently, leading to delays or incomplete coverage. - Inconsistent Patch Deployment
Ensuring consistent patching across all systems can be a logistical challenge in large organizations, especially when different departments manage their infrastructure.
The Future of Patch Management
As cybersecurity threats evolve, patch management will become even more critical. With the rise of artificial intelligence (AI) and automation, organizations can look forward to more streamlined and efficient patch management processes. AI-driven tools can help prioritize patches, automate testing, and monitor systems for vulnerabilities in real-time, allowing teams to focus on more strategic security initiatives.
Ultimately, effective patch management is a cornerstone of any robust cybersecurity strategy. Organizations can minimize risk, ensure compliance, and secure their systems by following best practices and leveraging the latest tools.
Keeping Systems Patched with Balbix
Balbix continuously assesses an enterprise’s cybersecurity posture and prioritizes open vulnerabilities based on business risk so that organizations like yours can maximize the impact of your patching efforts. The Balbix platform understands and learns your business context, considers the value of each asset to your business, and considers vulnerabilities, active threats, exposure due to software usage, and any mitigating controls already implemented in your enterprise.
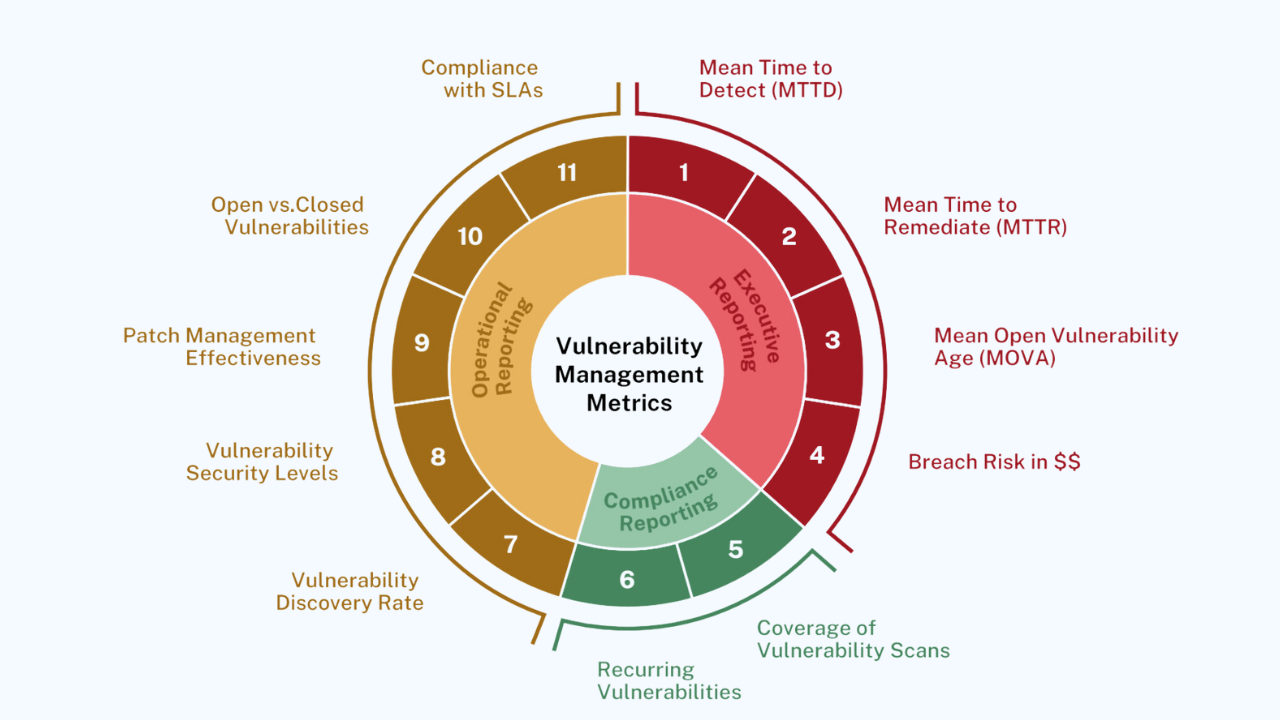
Balbix also prioritizes vulnerabilities and enables you to act on mitigation steps appropriate to the unpatched system, such as patching, accepting risk or using compensating controls. Balbix also recommends the patches that most efficiently address the maximum number of open CVEs for an application for security teams to reduce risk more effectively. Plus, you can report on your patching posture using customized dashboards to track and show critical metrics like MTTP and MOVA.
Frequently Asked Questions
- Why is patch management important?
-
Patch management is crucial for closing security gaps, fixing software bugs, and preventing attackers from exploiting vulnerabilities. Timely patching ensures systems remain secure, comply with regulations, and operate efficiently without unpatched weaknesses.
- What are the steps in patch management?
-
The patch management process typically involves identifying needed patches, testing them in a controlled environment, deploying them across systems, and monitoring for issues. Regular audits and automated tools can streamline this process to ensure security gaps are closed promptly.
- How often should patches be applied?
-
Patches should be applied as soon as possible after release, especially for critical vulnerabilities. Many organizations implement regular patch schedules, such as monthly updates, while urgent patches for severe vulnerabilities may require immediate deployment.