The NIST Cybersecurity Framework (CSF) 2.0 is an updated version of the original framework introduced by the National Institute of Standards and Technology (NIST). It is designed to help organizations manage and reduce cybersecurity risks. The NIST Cybersecurity Framework (NIST CSF) is a flexible set of guidelines and best practices designed to help organizations enhance their information security and manage cybersecurity risks.
NIST CSF v2.0 introduces updates that enhance its focus on governance (adding a sixth core function called “Govern.”), supply chain risk management, and measurement of cybersecurity outcomes while aligning more closely with international standards and improving flexibility for diverse organizations.
History of the NIST Framework
The NIST Cybersecurity Framework was introduced in 2014 as a voluntary guideline for organizations to improve cybersecurity practices. NIST CSF 1.0 quickly became a widely adopted tool across various industries, offering a structured approach to managing and mitigating cybersecurity risks. In 2018, NIST released CSF 1.1, which included updates to address the growing importance of supply chain risk management and to provide more guidance on authentication, authorization, and identity proofing.
NIST CSF 2.0 represents the most significant update to the framework. Released as a public draft in 2023 and the final version in February 2024, this version introduces the “Govern” function, expands the existing core functions, and aligns the framework with modern cybersecurity challenges. Feedback from a wide range of stakeholders, including Fortune 500 companies, has informed the development of NIST CSF 2.0, ensuring it meets the needs of contemporary organizations.
What are the Core Functions of the NIST CSF 2.0 Framework?
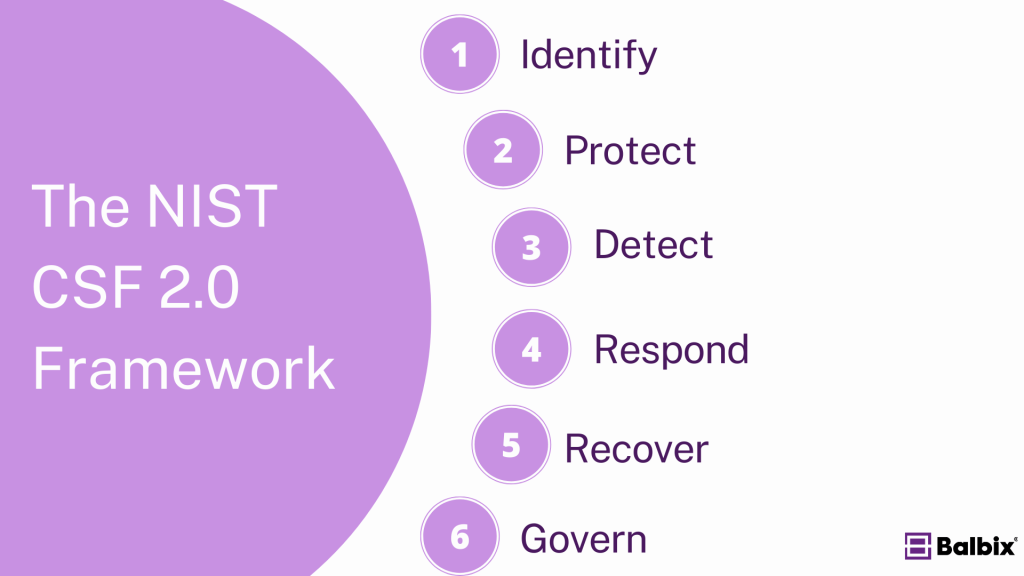
NIST CSF 2.0 is structured around six core functions, each representing a critical aspect of an effective cybersecurity program. This includes the original five pillars from NIST 1.1—Identify, Protect, Detect, Respond, and Recover—and introduces a newly added “Govern” function.
The framework provides a comprehensive approach to managing cybersecurity risk. These pillars represent the key stages of a robust cybersecurity program, guiding organizations in understanding, managing, and reducing cybersecurity risks. Each pillar has essential activities that are critical to an effective cybersecurity strategy.
1. Govern (New in NIST CSF 2.0)
The Govern function is an overarching addition introduced to emphasize governance’s importance in effectively managing cybersecurity risks. It focuses on establishing and maintaining the governance structures necessary for an organization to manage its cybersecurity risks in alignment with its business objectives and regulatory requirements.
The 6 Govern categories:
- Organizational Context (GV.OC)
- Risk Management Strategy (GV.RM)
- Roles, Responsibilities, and Authorities (GV.RR)
- Policy (GV.PO)
- Oversight (GV.OV)
- Cybersecurity Supply Chain Risk Management (GV.SC)
Key Activities Include:
- Establishing risk management objectives with agreement from organizational stakeholders
- Establishing a standardized method for calculating, documenting, categorizing, and prioritizing cybersecurity risks
- Establishing and maintaining risk appetite and risk tolerance statements
- Including cybersecurity risk management activities and outcomes in enterprise risk management
- Establishing and communicating cybersecurity roles, responsibilities, and authorities
- Reviewing and adjusting the cybersecurity risk management strategy to ensure coverage of organizational risks and requirements
- Evaluating organizational cybersecurity risk management performance and making necessary adjustments
- Establishing lines of communication for cybersecurity risks across the organization, including suppliers and third parties
These activities help ensure that cybersecurity efforts are well-coordinated, aligned with business goals, and effectively managed at the highest levels of the organization. Governance is critical for ensuring that cybersecurity is integrated into the organization’s overall strategy and that risks are managed consistently and effectively across all levels of the organization.
2. Identify
The Identify function is foundational to a successful cybersecurity program. It helps organizations deeply understand their environment and its associated risks. Organizations can prioritize cybersecurity by identifying critical assets, vulnerabilities, and the broader business context.
The 3 Identify categories:
- Asset Management (ID.AM)
- Risk Assessment (ID.RA)
- Improvement (ID.IM)
Key activities Include:
- Identifying physical and software assets to establish the basis of an asset management program
- Identifying the organization’s business environment, including its role in the supply chain
- Identifying established cybersecurity policies to define the governance program as well as identifying legal and regulatory requirements regarding the cybersecurity capabilities of the organization
- Identifying asset vulnerabilities, threats to internal and external organizational resources, and risk response activities to assess risk
- Establishing a risk management strategy, including identifying risk tolerance
- Identifying a supply chain risk management strategy, including priorities, constraints, risk tolerances, and assumptions used to support risk decisions associated with managing supply chain risks
These activities help organizations comprehensively understand their cybersecurity posture and ensure they are prepared to manage and mitigate risks effectively. The Identify function is the foundation for all subsequent functions (Protect, Detect, Respond, and Recover) within the NIST CSF.
3. Protect
The Protect function focuses on implementing appropriate safeguards to ensure the delivery of critical infrastructure services and to limit or contain the impact of a potential cybersecurity event.
The 5 Protect categories:
- Identity Management, Authentication, and Access Control (PR.AA)
- Awareness and Training (PR.AT)
- Data Security (PR.DS)
- Platform Security (PR.PS)
- Technology Infrastructure Resilience (PR.IR)
Key Activities Include:
- Implementing protections for Identity Management and Access Control within the organization, including physical and remote access
- Empowering staff through security awareness training, including role-based and privileged user training
- Establishing data security protection consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information
- Implementing processes and procedures to maintain and manage the protection of information systems and assets
- Protecting organizational resources through maintenance, including remote maintenance activities
- Managing technology to ensure the security and resilience of systems, consistent with organizational policies, procedures, and agreements
By implementing appropriate safeguards, these activities help organizations protect their information systems and assets from cyber threats. The Protect function is crucial for ensuring an organization’s critical services operate securely and efficiently even when facing potential cybersecurity challenges.
4. Detect
The Detect function focuses on identifying the occurrence of cybersecurity events in a timely manner. This function is crucial for quickly recognizing and responding to potential threats.
The 2 detect categories:
- Continuous Monitoring (DE.CM)
- Adverse Event Analysis (DE.AE)
Key Activities Include:
- Ensuring anomalies and events are detected and their potential impact is understood
- Implementing continuous monitoring capabilities to monitor cybersecurity events and verify the effectiveness of protective measures, including network and physical activities
These activities are critical for enabling organizations to quickly detect and respond to cybersecurity incidents, minimizing the potential impact on their operations. The Detect function is a key component of a proactive cybersecurity strategy, allowing organizations to identify and mitigate threats early before they cause significant damage.
5. Respond
The Respond function focuses on developing and implementing appropriate actions to contain the impact of a detected cybersecurity event. This function is critical for effectively managing and mitigating the effects of cybersecurity incidents.
The 4 Respond categories:
- Incident Management (RS.MA)
- Incident Analysis (RS.AN)
- Incident Response Reporting and Communication (RS.CO)
- Incident Mitigation (RS.MI)
Key Activities Include:
- Ensuring response planning processes are executed during and after an incident
- Managing communications with internal and external stakeholders during and after an event
- Analyzing the incident to ensure effective response and supporting recovery activities, including forensic analysis and determining the impact of incidents
- Performing mitigation activities to prevent the expansion of an event and to resolve the incident
- Implementing improvements by incorporating lessons learned from current and previous detection/response activities
These activities enable organizations to respond quickly and effectively to cybersecurity incidents, minimizing damage and facilitating a rapid recovery. The Respond function ensures an organization can manage and recover from incidents while maintaining business continuity.
6. Recover
The Recover function focuses on developing and implementing plans and activities to restore any capabilities or services impaired due to a cybersecurity incident. The goal is to ensure the timely recovery to normal operations and to improve resilience against future incidents.
The 2 Recover categories:
- Incident Recovery Plan Execution (RC.RP)
- Incident Recovery Communication (RC.CO)
Key Activities Include:
- Ensuring the organization implements recovery planning processes and procedures to restore systems and/or assets affected by cybersecurity incidents
- Implementing improvements based on lessons learned and reviews of existing strategies
- Internal and external communications are coordinated during and following the recovery from a cybersecurity incident
These activities help organizations restore operations efficiently after a cybersecurity incident, reduce the time to recovery, and enhance resilience by learning from each incident. The Recover function is crucial for maintaining business continuity and ensuring that the organization can quickly return to normal operations with minimal disruption.
Making GenAI Work for Cybersecurity
Join Nvidia and Balbix as they explore how to apply GenAI to cybersecurity, avoid common pitfalls, ensure data privacy, and uncover the true costs of building and maintaining a GenAI solution.


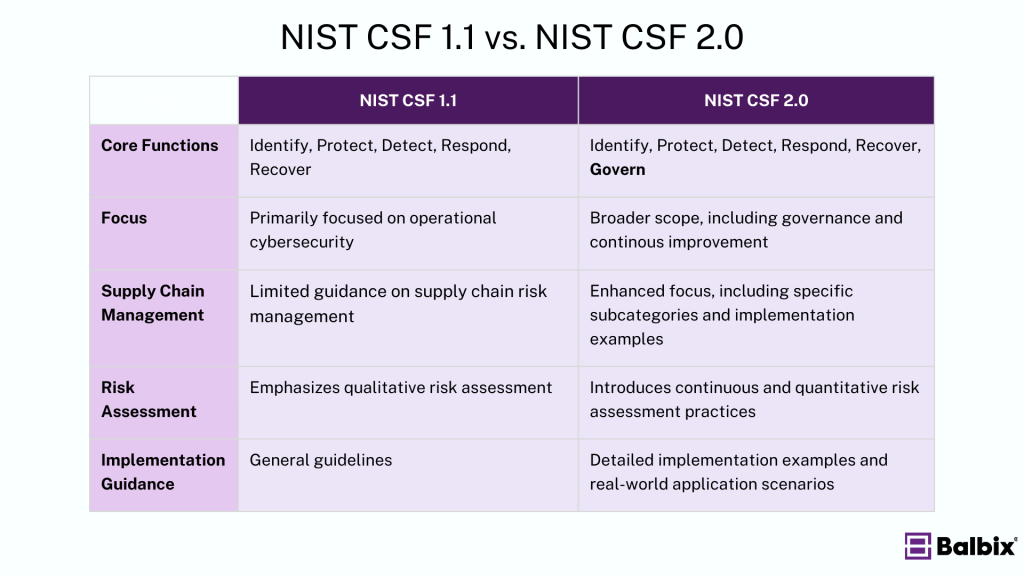
How Does NIST CSF 2.0 Differ from NIST CSF 1.1?
NIST CSF 2.0 introduces several key updates over its predecessor, NIST CSF 1.1:
Benefits of the NIST CSF 2.0 Framework
The NIST Cybersecurity Framework (CSF) provides a structured approach to managing cybersecurity risks through its core functions: Identify, Protect, Detect, Respond, and Recover. NIST CSF 2.0 adds a sixth function, Govern, which focuses on cybersecurity governance and aligning with business objectives.
Key Benefits:
- Comprehensive Risk Management: Offers a clear method for identifying, assessing, and managing cybersecurity risks, aligning these efforts with overall business strategies.
- Flexibility and Scalability: Adapts to organizations of any size or industry, with enhanced guidance in CSF 2.0 for tailoring the framework to specific needs and evolving threats.
- Regulatory Compliance: Helps meet regulatory requirements, reducing risks of fines and legal issues, and the Govern function reinforces compliance alignment.
- Enhanced Cyber Resilience: Improves detection, response, and recovery from incidents, supporting business continuity and adapting to new threats.
- Industry Recognition: NIST CSF is one of the most widely adopted security frameworks across all industries, and the addition of the Govern function reflects the growing importance of cybersecurity in corporate governance.
- Better Board Reporting: The NIST framework works very well for board-level reporting. If you are a new CISO, here is a board presentation template that allows you to introduce your InfoSec strategy and plan by aligning with the framework.
Who Uses the NIST 2.0 Framework?
NIST CSF 2.0 is widely adopted across various industries and is designed to align with and complement multiple government, industry, and regional cybersecurity frameworks. It applies to a broad range of organizations. NIST CSF 2.0 pre-maps to frameworks like CRI Profile, NIST SP 800-221A, NIST SP 800-53, the Cloud Control Matrix (CCM), and CIS Controls, helping organizations streamline compliance and manage cybersecurity risks effectively. It is particularly beneficial in industries such as:
- Financial Services: To safeguard financial data and meet regulatory standards.
- Healthcare: To protect patient information and ensure HIPAA compliance.
- Manufacturing: To secure industrial systems and safeguard intellectual property.
- Government Agencies: To protect national security and critical infrastructure.
How Does NIST CSF 2.0 Integrate With Other Cybersecurity Frameworks?
Implementing NIST CSF 2.0 involves a structured approach to ensure comprehensive cybersecurity coverage. Here is a step-by-step guide:
| Implementation Step | NIST CSF 1.1 | NIST 2.0 Enhancement |
| 1. Prioritize and Scope | Identify organizational objectives and determine the scope of the cybersecurity program. This helps set priorities and allocate resources effectively. | Integrate governance considerations early in the process, ensuring that the scope includes alignment with overall business objectives and compliance requirements. |
| 2. Orient and Map | Understand the context of the cybersecurity environment, including the organization’s mission, regulatory requirements, threat landscape, components, dependencies, and compliance obligations. | Consider continuous and quantitative risk assessments as part of the orientation to ensure an up-to-date understanding of threats and vulnerabilities. This stage should also involve engaging stakeholders to align cybersecurity goals with the organization’s strategic direction. |
| 3. Create a Current Profile | Assess your current cybersecurity posture. Evaluate existing policies, controls, and procedures to identify strengths and weaknesses and establish a baseline for improvement. | Include continuous monitoring and real-time data collection to ensure the current profile is dynamic and reflects ongoing changes in the threat landscape and IT environment. |
| 4. Conduct a Risk Assessment | Identify and evaluate potential threats and vulnerabilities. Engage third-party experts for an objective risk analysis. Prioritize areas of concern for mitigation. | Emphasize using quantitative risk assessment methods to provide a more precise evaluation of risks, enabling better prioritization and resource allocation. |
| 5. Create a Target Profile | Develop a desired cybersecurity posture using the NIST Framework as a guide. Set achievable goals aligned with risk tolerance and long-term security objectives. | Incorporate governance and continuous improvement into the target profile. This ensures the target state is aligned with current best practices and adaptable to future changes and threats. |
| 6. Determine, Analyze and Prioritize Gaps | Compare the current profile with the target profile to identify gaps. Prioritize these gaps based on their potential impact on the organization. Allocate resources to address critical vulnerabilities first. | Use a risk-based prioritization approach that considers both vulnerabilities’ severity and existing controls’ effectiveness. This step should also involve continuous evaluation of gaps to adjust priorities as new risks emerge. |
| 7. Implement an Action Plan | Develop and execute a plan based on prioritized gaps. Focus on high-risk areas first. Review and update regularly to align with evolving business goals. | Ensure that the action plan includes governance oversight and continuous monitoring mechanisms to track progress and effectiveness. Additionally, the plan should be reviewed regularly and updated as necessary to respond to changes in the threat environment or organizational priorities. |
| 8. Govern (New in NIST CSF 2.0 | Not Applicable | Establish a governance framework that defines roles, responsibilities, and accountability mechanisms. This step ensures that the cybersecurity program is aligned with business objectives and regulatory requirements. Continuous oversight and reporting are essential to maintain the program’s effectiveness and relevance. |
Frequently Asked Questions
- What are the key changes in NIST Cybersecurity Framework (CSF) 2.0 compared to previous versions?
-
NIST CSF 2.0 introduces updated guidance on emerging threats, such as supply chain risks and cloud security. It emphasizes governance, planning, and the inclusion of specific control families, making the framework more comprehensive. The new version also aligns more closely with international standards, providing a more global approach to cybersecurity management.
- How does NIST CSF 2.0 help improve an organization's cybersecurity posture?
-
CSF 2.0 offers a structured approach for identifying, protecting, detecting, responding to, and recovering from cyber threats. By integrating risk management into everyday operations and aligning cybersecurity with business goals, organizations can improve situational awareness, prioritize risks, and allocate resources effectively, thus enhancing overall resilience.
- Who should implement the NIST CSF 2.0 Framework?
-
NIST CSF 2.0 is designed for any organization, regardless of size or industry. It is especially useful for entities looking to enhance cybersecurity practices or comply with regulatory requirements. The framework provides flexibility, allowing organizations to adopt its principles according to their needs and risk profiles.
- How can NIST CSF 2.0 be tailored to fit different organizational needs?
-
The flexible framework allows organizations to implement its guidelines based on their specific risks, regulatory requirements, and operational complexities. Organizations can choose relevant controls, scale processes to fit their size, and adopt the framework incrementally, aligning it with existing cybersecurity and risk management practices.
- Does NIST CSF 2.0 ensure compliance with other regulations?
-
While NIST CSF 2.0 is not a regulatory requirement, it provides a comprehensive foundation that aligns with many existing laws and standards, such as GDPR, HIPAA, and ISO 27001. Implementing the framework can demonstrate a proactive cybersecurity posture, potentially simplifying compliance with industry-specific regulations.