A SOC is a group of security professionals working together at a facility or as a remote team. They are responsible for monitoring and analyzing an organization’s security posture by focusing on threat detection, incident response, and analysis. The SOC team combines a variety of technology solutions, such as Security Information and Event Management (SIEM) for real-time event monitoring, analysis and alerts.
Security operations center teams consist of security analysts, engineers, and managers who oversee security operations. SOC teams often work in shifts around the clock and continuously monitor threat intelligence.
The SOC team’s monitoring includes data inputs from telemetry across an organization’s IT infrastructure (e.g., networks, computers, appliances, IoT devices, and data storage systems). With all this information, the SOC is the correlation point for system event logs. This allows the SOC team to supplement its threat intelligence data set, gain better visibility into potential security threats, and respond if required.
Four Common Types of SOCs
There are several common types of Security Operations Centers (SOCs), each suited to different organizational needs:
- Internal SOC: A company’s security team operates in-house, providing complete control over security operations. Internal SOCs are ideal for large organizations with extensive resources and security expertise.
- Managed SOC: Outsourced to a third-party Managed Security Service Provider (MSSP). This option allows companies to access specialized security expertise without managing the SOC internally, making it popular with smaller or resource-constrained organizations.
- Hybrid SOC: Combines internal and outsourced capabilities. An internal team handles critical security tasks, while external MSSPs support monitoring or incident response. This setup provides flexibility and scalability.
- Virtual SOC: A decentralized approach where security personnel operate remotely, using cloud-based tools and collaboration platforms. This is often more cost-effective and allows for a geographically distributed team.
Each SOC type offers distinct benefits, depending on an organization’s size, expertise, and security needs.
Roles and Responsibilities of SOC Team Members
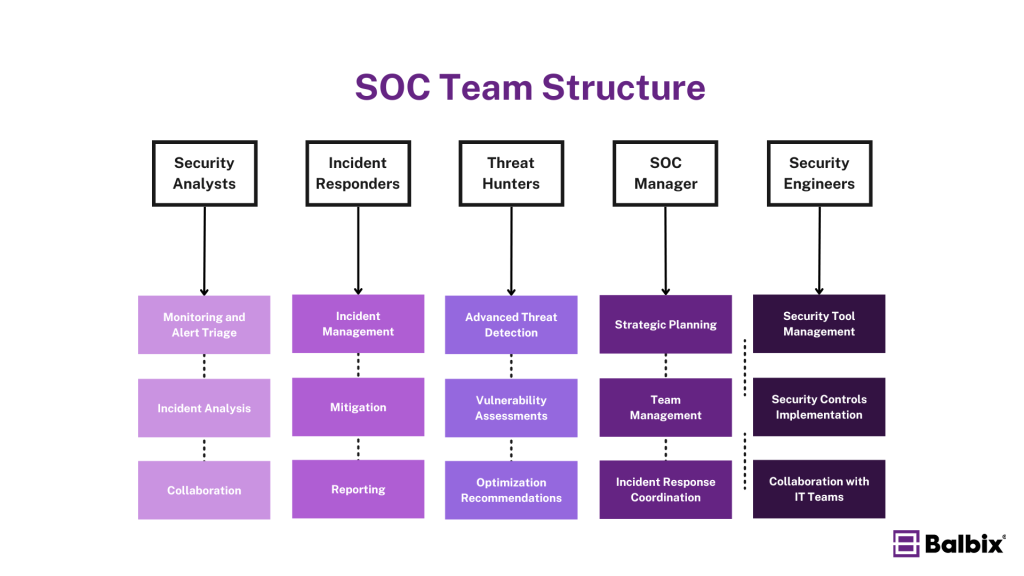
A Security Operations Center (SOC) is staffed by various cybersecurity professionals who work together to protect an organization’s information assets. Key roles within a SOC include:
Security Analysts
Security Analysts are the frontline defense in a SOC, responsible for monitoring networks and systems for potential security breaches or intrusions. Their key responsibilities include:
- Monitoring and Alert Triage: They monitor security alerts and logs using tools such as Security Information and Event Management (SIEM) systems and threat intelligence feeds. They categorize and prioritize alerts, identifying false positives and high-risk events.
- Incident Analysis: Analysts analyze security incidents, determine their validity, and escalate incidents that require further attention.
- Collaboration: They work closely with other teams, such as incident response teams, to resolve threats.
Incident Responders
Incident Responders are crucial in managing and responding to security incidents. Their key roles include:
- Incident Management: They conduct forensic analysis, manage incidents as they occur, and communicate security requirements to the organization in the case of a significant data breach.
- Mitigation: Incident Responders work to mitigate threats quickly, containing the incident and limiting its impact.
- Reporting: They document and report incident findings, ensuring lessons learned are applied to improve future responses.
Threat Hunters
Threat Hunters proactively search for cyber threats that may be undetected within the network. Their key responsibilities include:
- Advanced Threat Detection: They use various threat detection technologies and tools to identify potential risks before they mature into security incidents.
- Vulnerability Assessments: Threat Hunters perform or supervise vulnerability assessments and penetration tests to identify security gaps and vulnerabilities.
- Optimization Recommendations: They recommend optimizations for security monitoring tools to improve the organization’s overall security posture.
SOC Manager
The SOC Manager oversees SOC operations and ensures effective communication across departments. Their key responsibilities include:
- Strategic Planning: SOC Managers are responsible for strategic planning, coordination, and ensuring the team is aligned with the organization’s security objectives.
- Team Management: They manage the SOC team, including hiring, training, and evaluating team members. They also ensure necessary training is received to develop the team’s personnel.
- Incident Response Coordination: SOC Managers coordinate incident response efforts and ensure compliance with regulatory requirements.
- Reporting: They report on SOC activities and performance to senior management.
Security Engineers
Security Engineers are responsible for designing and implementing security architectures, tools, and protocols. Their key responsibilities include:
- Security Tool Management: They maintain and optimize security tools and infrastructure, ensuring they are correctly configured and up to date.
- Security Controls Implementation: Security Engineers implement security controls and technologies, conduct security assessments and vulnerability scans, and develop and maintain security documentation.
- Collaboration with IT Teams: They work with other IT teams to ensure security best practices are implemented across the organization.
How a Traditional Security Operations Center Works
Security operations centers implement security strategies, work on systems built according to specific security architectures, and use telemetry from protective tools (e.g., network devices, firewall).
The responsibility of the SOC team is to operationalize security systems and tools so the organization can quickly resolve alerts and mitigate threats. While the SOC team does not install many security tools (e.g., firewalls, intrusion detection systems, intrusion prevention systems, breach detection solutions, probes, security information, and event management systems), they are the primary users of these tools.
Making GenAI Work for Cybersecurity
Join Nvidia and Balbix as they explore how to apply GenAI to cybersecurity, avoid common pitfalls, ensure data privacy, and uncover the true costs of building and maintaining a GenAI solution.


The SOC team correlates and analyzes the information collected from data flows, telemetry, packet capture, Syslog, and other methods to bolster its threat intelligence and expedite incident response.
Security Operations Center Challenges
Given the blinding speed at which alerts pile up in security information and event management (SIEM) logs, the SOC team’s job can be overwhelming, with many more alerts than nearly any team can review and no end in sight.
- Twenty-seven percent of SOCs receive more than 1 million alerts each day.
- The average security analyst investigates 20–25 incidents on any given day.
- It takes 13–18 minutes to compare indicators of compromise (IoC) to logs, threat intelligence feeds, and external intelligence.
- Manual research can yield false-positive rates of 70 percent or higher.
- To make matters worse, as security analysts struggle against an ever-increasing volume of complex alerts, the SOC team is facing a talent crisis. Sixty-six percent of cybersecurity professionals believe there are too few qualified analysts to handle the alert volume in the SOC.
In addition to managing a mountain of alerts, the other challenge is the reactive nature of a SOC. When a security alarm goes off in a traditional SOC, security operations personnel aim to handle the incident as quickly as possible to avoid a breach.
In recent years, the rate and variety of daily security events faced by most SOCs have increased rapidly to the point that defenders can’t keep up.
While adopting managed services and automated response in security incident handling helps somewhat, the fundamentally reactive nature of traditional security operations makes it difficult to reduce the likelihood of breaches proactively.
What is an Intelligent SOC (iSOC)?
An Intelligent SOC (iSOC) is a modernized Security Operations Center that uses advanced technologies like AI and machine learning to detect, analyze, and respond to cyber threats in real-time. iSOCs integrate automation and predictive analytics to enhance threat detection and incident response, improving efficiency and accuracy.
Key tools include:
- Automatic Discovery of IT Assets: This involves systematically tracking and monitoring physical and digital assets throughout their lifecycle to maintain an accurate and up-to-date inventory.
- Risk-Based Vulnerability Management: This approach prioritizes and remediates vulnerabilities based on their potential impact on the organization, considering factors such as vulnerability severity, threat level, asset exposure, and security controls.
- Cyber Risk Quantification: This process assesses the potential monetary impact of cyber threats on an organization’s assets, helping in making informed decisions by quantifying the risk in financial terms.
- Artificial Intelligence and Machine Learning for Predictive Analytics: AI and Machine Learning enable proactive cyber-defense strategies by analyzing vast amounts of data to identify patterns and anomalies that may indicate potential threats. Tools like those from Balbix leverage AI to enhance threat intelligence and risk assessments.
- Security Orchestration, Automation, and Response (SOAR) Tools: These tools automate and streamline security incident response processes, integrating various security tools to provide a centralized platform for managing and responding to security incidents.
- Threat Intelligence Platforms (TIPs_: TIPs collect, aggregate, and analyze threat data from multiple sources, providing real-time alerts and notifications for suspicious activities, assisting in compliance management, and offering user and entity behavior analytics to detect anomalies.
By incorporating these advanced tools and technologies, iSOCs can enhance their threat detection, incident response, and overall security posture, aligning with the latest trends and best practices in cybersecurity.
As traditional SOCs evolve into intelligent SOCs (iSOCs), they provide real-time insights based on continuous risk assessments. iSOCs translate cyber risks into financial terms, helping leadership make informed decisions. They use automation to handle routine tasks like neutralizing low-level threats and integrating data from various systems, freeing security analysts to focus on more significant threats. With constant monitoring and real-time data, iSOCs stay updated to protect against evolving threats.
Tools like Balbix help the SOC/iSOC understand the business impact of events on the company and determine where to focus remediation efforts.
Frequently Asked Questions
- Why is a SOC important?
-
A SOC is important because it improves security incident detection by continuously monitoring and analyzing data activity across an organization’s networks, endpoints, servers, and databases—around the clock. This enables the timely detection and response of security incidents.
- Who works in a SOC?
-
The security operations center team consists of security analysts and engineers who oversee all activity on servers, databases, networks, applications, endpoint devices, websites, and other systems. The focus of SOC teams is on identifying potential security threats and stopping them.
- What are the responsibilities of SOC?
-
The SOC team operates, manages, and maintains the security center as an organizational resource. This includes developing an overarching strategy and plan and creating processes to support the center’s operation. It also includes evaluating, implementing, and operating tools, devices, and applications and overseeing the integration, maintenance, and updating.


