What is exposure management?
Exposure management in cybersecurity focuses on pinpointing, evaluating, and addressing potential vulnerabilities and threats to reduce the risk of cyberattacks on an organization’s assets. This process encompasses handling common vulnerabilities and exposures (CVEs) and other non-CVE exposures, such as cloud misconfigurations, outdated systems, application security issues, weak or stolen credentials, control deficiencies, and user-related risks.
Exposure Management has four core pillars: Assessment, Prioritization, Validation, and Mobilization.
What are the Differences Between Exposure and Vulnerability Management?
While both approaches aim to remediate risk, they have several key differences. Exposure management (EM) is an evolution of vulnerability management (VM), and organizations should build upon their VM foundations to transition successfully to exposure management.
Let’s dive into the seven core areas where vulnerability and exposure management differ.
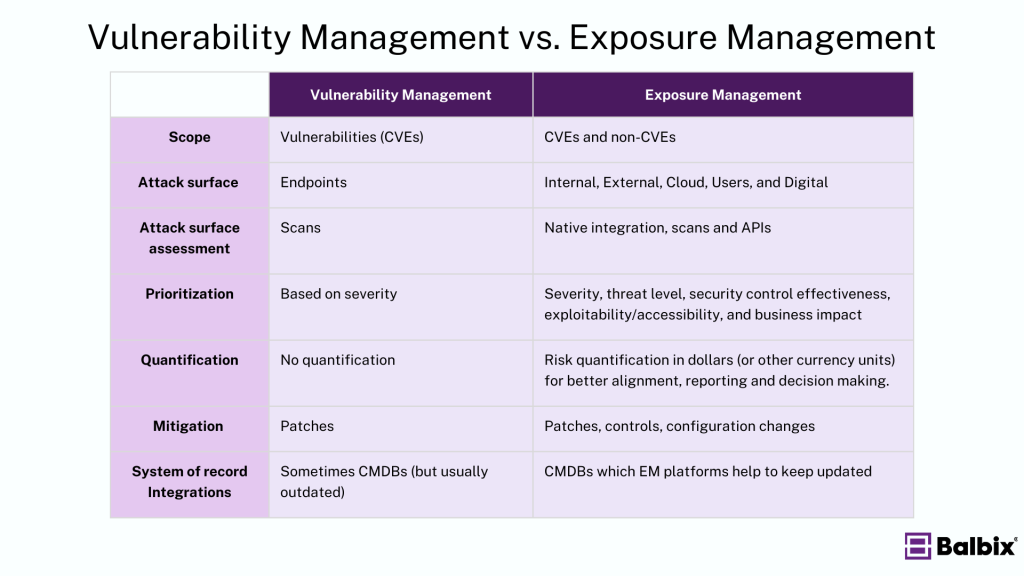
Scope
Traditional VM tools focus exclusively on vulnerabilities (CVEs). On the other hand, EM tools focus on exposure which are CVEs as well as non-CVEs. Exposures include software and open-source vulnerabilities, cloud misconfigurations, end-of-life systems, application risk findings, weak and stolen credentials, user risk and more. EM tools assess all exposures and prioritize remediation based on risk – i.e, the expected loss of a potential compromise.
Attack Surface
EM tools provide visibility into an organization’s entire attack surface, which includes internal, external, cloud, user, and digital assets. VM tools primarily focus on endpoints. They traditionally do not consider other attack surfaces, such as cloud infrastructure, IoT devices, and network devices, applications, and users—all of which are targeted by attackers.
Attack Surface Assessment
The methods for attack surface assessment differ between exposure and vulnerability management. Vulnerability management relies primarily on agent-based scans, which are hard to deploy and maintain. Additionally, scans run once or twice a week (or even less frequently), leading to out-of-date vulnerability data. Exposure management leverages various techniques, including native integrations with tools and APIs that leverage a broad set of telemetry and provide near real-time visibility into exposures.
Prioritization Method
Traditional vulnerability management tools primarily rely on severity ratings or Common Vulnerability Scoring System (CVSS) scores. Vulnerability assessment results in a much larger number of vulnerabilities being classified as critical, leading to an overload of issues marked for immediate remediation. Consequently, IT resources may be stretched thin, focusing on patching and testing systems indiscriminately, while truly high-impact vulnerabilities might not receive the prompt attention they require. In contrast, exposure management utilizes a variety of data points for each exposure, including severity, threat levels, exploitability, security controls effectiveness, and business impact. This greatly reduces IT workloads.
Cyber Risk Quantification
Some EM platforms leverage Cyber Risk Quantification (CRQ) to enable non-business stakeholders to understand the risk of exposure associated with an organization’s attack surface. With CRQ, technical leaders measure risk and risk reduction in monetary terms, such as dollars or euros and articulate the ROI of security tools and resources.
On the other hand, VM tools offer rudimentary risk quantification that fails to influence business decisions.
Mitigation
While traditional cyber vulnerability management focuses on applying patches to known vulnerabilities, exposure management offers a more comprehensive strategy. First, exposure management tools evaluate the effectiveness of existing security controls, which helps prioritize remediation efforts based on actual risk. Additionally, these tools provide detailed insights into potential attack paths, enabling organizations to identify and address the exposures most likely to be exploited and provide remediation and mitigation options.
This holistic approach ensures that resources are allocated more efficiently, focusing on the areas of greatest impact.
System of Record
VM tools do not play well with inaccurate and incomplete Configuration Management Databases (CMDBs) systems, which affects the prioritization of CVEs by missing crucial context about asset dependencies and their criticality within the IT infrastructure. Exposure management provides native two-way integration with CMDBs from ongoing assessments and the current attack surface, which helps in maintaining accurate and up-to-date records in the CMDB.
3 Ways to Transition Vulnerability Management to Exposure Management
Expand your asset inventory
Maintaining an up-to-date asset inventory is crucial for any cybersecurity program. However, instead of taking a limited approach, organizations need to aim to unify all digital assets, users, and their associated exposures and vulnerabilities into a single platform. By doing so, the data can be deduplicated, normalized, and correlated, creating a comprehensive and accurate inventory. With this unified view, organizations gain full visibility into their entire attack surface, allowing them to prioritize risk mitigation efforts more effectively and make informed security decisions.
Establish a risk-based approach to prioritization
Not all exposures and vulnerabilities pose the same level of risk. Adopting a risk-based prioritization approach allows organizations to focus on the exposures with the highest potential impact. This prioritization helps allocate resources effectively, ensuring that the most critical vulnerabilities are addressed first, thereby minimizing overall risk.
Mobilize to remediate the riskiest exposures
Mobilization involves a coordinated effort to remediate exposure. For faster remediation, it is important to route the ‘fix’ to the right team and with appropriate context. The goal is to efficiently address the exposures without having IT or the risk owner chase down the information and context required to implement and test the fix.