Cyber threat intelligence is data collected from various sources that provide insights into threat actors, their techniques, and vulnerabilities that can be exploited. This intelligence can come from sources like open-source data, dark web activity, or proprietary feeds, and it provides context around potential risks.
Security teams use threat intelligence to understand adversarial tactics, techniques, and procedures (TTPs), which helps them develop stronger security postures.
Why is Threat Intelligence Important?
Threat intelligence is critical because it gives organizations deeper visibility into cyber threats. With accurate and timely intelligence, organizations can:
- Improve decision-making: Armed with valuable intelligence, security teams can make more informed decisions about protecting their systems.
- Enhance detection and response: Organizations can proactively identify and respond to threats.
- Mitigate risks: Threat intelligence reveals potential vulnerabilities that can be hardened before exploitation.
- Reduce investigation time: It speeds up incident investigations and decreases the mean time to respond (MTTR) to threats.
What are the Benefits of Threat Intelligence?
Cyber threat intelligence offers numerous advantages to organizations, especially in an era where cyber threats are increasingly complex and frequent.
- Enhances alert quality: Filters out noise to deliver actionable alerts.
- Improves detection and response: Offers timely insights that improve an organization’s ability to detect and respond to security incidents.
- Increases incident coverage: Provides a broader view of potential and existing threats.
- Reduces investigation time: Accelerates the investigative process, making understanding the root causes of threats easier.
- Minimizes response time: Decreases the MTTR, allowing organizations to respond more swiftly to incidents.
- Reveals critical threats: Identifies the most pressing and impactful threats so security teams can prioritize their efforts.
The Threat Intelligence Lifecycle
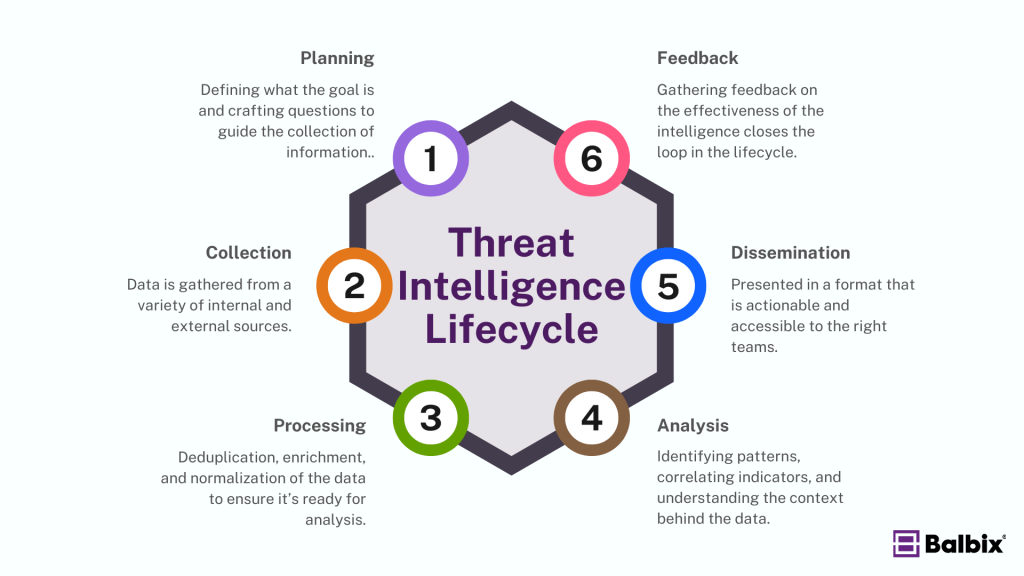
The cyber threat intelligence lifecycle systematically gathers processes, analyzes, and distributes intelligence to inform security decisions. The six key steps in this lifecycle are:
- Planning: This initial phase involves defining the intelligence goals. Questions are crafted to guide the collection of specific, actionable information. These questions often focus on threat actors, vulnerabilities, or other pertinent risks.
- Collection: Data is gathered from a variety of internal and external sources, including:
- OSINT (Open Source Intelligence)
- Internal system alerts
- Threat intelligence feeds
- Dark web sources
- Network logs and historical incident responses
- Processing: Once collected, raw data must be sorted, cleaned, and formatted. This process includes deduplication, enrichment, and normalization to ensure the data is ready for analysis.
- Analysis: At the heart of the threat intelligence lifecycle, the analysis phase converts raw data into actionable insights. This involves identifying patterns, correlating indicators, and understanding the context behind the data. Analysts may use a combination of structured techniques and peer-reviewed reports to ensure accuracy.
- Dissemination: The insights generated during analysis are shared with relevant stakeholders. This information must be presented in a format that is actionable and accessible to the right teams, including IT, security leadership, and executives.
- Feedback: Gathering feedback on the effectiveness of the intelligence closes the loop in the lifecycle. This step ensures continuous improvement by identifying gaps in intelligence and refining future collection efforts.
Types of Threat Intelligence
Threat intelligence can be classified into three main categories based on the level of detail and the type of information provided: Strategic, Tactical, and Operational (Technical).
Strategic Threat Intelligence
Strategic threat intelligence offers a high-level view of the cyber threat landscape. It focuses on understanding the motives and goals behind attacks, such as who the attackers are, why they target specific organizations, and what trends drive the attacks. This type of intelligence is crucial for long-term planning and decision-making.
Examples of strategic threat intelligence include:
- Attack trends
- Known cybercriminal groups and nation-state actors
- Financial impacts of cyberattacks
- Industry-specific threat analysis
CISOs and senior executives typically consume this intelligence to guide resource allocation and security strategy.
Tactical Threat Intelligence
Tactical intelligence focuses on the TTPs used by attackers. This type of intelligence is vital for real-time defenses and operational planning. Organizations can better prepare and implement defenses to stop or mitigate ongoing threats by understanding how attackers operate.
Making GenAI Work for Cybersecurity
Join Nvidia and Balbix as they explore how to apply GenAI to cybersecurity, avoid common pitfalls, ensure data privacy, and uncover the true costs of building and maintaining a GenAI solution.


Tactical threat intelligence includes:
- Information on attack vectors and vulnerabilities
- Malware reports
- Indicators of compromise (IoCs)
Security operations teams often use tactical threat intelligence to improve defenses such as intrusion detection systems (IDS) and firewalls.
Operational (Technical) Threat Intelligence
Operational or technical threat intelligence provides a granular, technical view of current and past attacks. It focuses on specific IoCs and technical details that help security teams quickly address vulnerabilities or mitigate active threats.
Examples of operational threat intelligence include:
- Malicious IP addresses
- Command-and-control (C2) channels
- Malware signatures
- Attack infrastructure (e.g., URLs, file hashes)
Operational threat intelligence typically has a shorter lifespan and is used by network administrators and security analysts to fine-tune security systems like SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response).
Use Cases of Threat Intelligence
Cyber threat intelligence can be applied across various areas of cybersecurity, including:
- Vulnerability Management: Identifying and prioritizing vulnerabilities to address the most critical threats first.
- Incident Response: Speeding up the investigation and response process during security incidents.
- Alert Management: Improving alert quality by filtering out non-actionable information.
- Security Posture Improvement: Strengthening security posture by incorporating lessons from past attacks.
- Fraud Prevention: Detecting and mitigating fraud-related activities.
How Balbix Enhances Cyber Threat Intelligence
Balbix’s AI-powered platform offers a unique approach to integrating threat intelligence into an organization’s security strategy. The platform combines cyber threat intelligence with advanced vulnerability management, exposure analysis, and real-time risk prioritization. With BIX, an AI-powered cyber risk assistant, Balbix automates the threat detection process, correlating threat data with an organization’s specific attack surface to provide targeted recommendations for reducing risk.
Balbix further streamlines cybersecurity operations by:
- Aggregating intelligence from multiple sources to deliver real-time risk assessments.
- Prioritizing vulnerabilities based on the severity and potential business impact.
- Mapping threats to the MITRE ATT&CK framework, enabling organizations to defend against known adversarial tactics effectively.
Incorporating Balbix into your cyber threat intelligence strategy helps your organization stay ahead of emerging threats, reduce risk, and optimize cybersecurity resources.
Frequently Asked Questions
- What are the most common challenges or pitfalls in effectively managing and operationalizing cyber threat intelligence?
-
Managing and operationalizing cyber threat intelligence often involves several hurdles, such as keeping up with the vast amount of threats, ensuring the relevance and accuracy of intelligence, integrating this intelligence effectively into security systems, and making sure the information is actionable for security teams.
Additionally, there’s the challenge of training staff to recognize and respond to threats appropriately and the need for coordination across different departments within an organization.
- How do organizations prioritize and integrate cyber threat intelligence with their existing security tools and practices?
-
Organizations integrate cyber threat intelligence by first identifying their biggest security risks. Then, they collect information about potential cyber threats and analyze this data to understand how it could impact them. Next, they use this intelligence to improve security measures, like updating firewalls or training staff on new threats.
- How can small to medium-sized enterprises (SMEs) with limited resources effectively leverage cyber threat intelligence?
-
Small to medium businesses can use cyber threat intelligence by focusing on the most relevant threats. They can do this by subscribing to affordable threat intelligence services, joining industry-specific cybersecurity forums, and regularly training employees on security awareness to recognize and respond to cyber threats.


