Cloud security comprises the technologies, controls, procedures, and policies that protect assets hosted in the cloud, including data, applications, and infrastructure. As businesses and governments rapidly adopt cloud computing to drive innovation and collaboration, robust cloud security becomes crucial to safeguarding these environments.
Why is Cloud Security Important?
The shift to cloud computing offers agility, lower IT costs, and global accessibility. However, this rapid adoption has made cloud security a top priority. According to Gartner, nearly half of IT spending in key markets will shift to the cloud by 2025. Despite this, many organizations need help with cloud security, with over 50% requiring more confidence in their current cloud security posture.
How Does Cloud Security Work?
Cloud security integrates policies, processes, and technologies to safeguard data, ensure regulatory compliance, and manage privacy, access, and authentication across users and devices. Cloud providers follow a shared responsibility model, securing the cloud infrastructure while customers are responsible for ensuring their data, applications, and network controls. Understanding this model is critical for building a resilient cloud security strategy.
Cloud security employs several tools and practices to protect cloud environments from threats.
Infrastructure Security
Cloud Security Posture Management (CSPM)
CSPM ensures that the cloud infrastructure is configured securely by continuously monitoring for misconfigurations, security risks, and compliance violations. These tools automatically scan cloud environments and alert teams to potential issues before they can be exploited.
Cloud Workload Protection Platforms (CWPP)
CWPP secures workloads in cloud environments, including virtual machines, containers, and serverless applications. These tools help identify and mitigate vulnerabilities, detect threats, and maintain the integrity of compute instances.
Cloud Infrastructure Entitlement Management (CIEM)
CIEM solutions manage and optimize access to cloud resources, ensuring that entitlements are correctly assigned. By enforcing the principle of least privilege, CIEM tools ensure that users only have access to the necessary data and systems, helping to reduce the risk of over-privileged access and minimize potential attack surfaces.
Encryption and Key Management
Encryption tools safeguard sensitive data by transforming it into unreadable ciphertext. Key management solutions securely handle and store encryption keys, ensuring only authorized users or systems can decrypt and access critical data.
Public Key Infrastructure (PKI)
PKI provides a robust framework for encrypting communications and verifying identities across cloud infrastructure. This prevents unauthorized access and ensures that data exchanges within the infrastructure remain secure.
Zero Trust Network Access (ZTNA)
ZTNA solutions assume no internal or external actor can be inherently trusted. They continuously validate users’ and devices’ identities, device health, and access permissions,
Application Security
Data Protection and Security Management (DPSM)
DPSM solutions safeguard sensitive data within cloud environments by preventing exposure, leakage, or loss. These tools continuously monitor data movements and ensure that only authorized users or systems can access or transfer critical information, protecting against unauthorized access or accidental breaches.
Cloud Detection and Response (CDR)
CDR platforms provide real-time monitoring and analysis of security events across cloud environments. By detecting anomalies, threats, and suspicious activity, CDR enables organizations to swiftly respond to incidents and minimize the potential impact of cyber threats.
Threat Intelligence and Security Analytics
These platforms aggregate threat data and use advanced analytics to predict, prevent, and respond to potential attacks targeting cloud applications. By integrating threat intelligence into the security lifecycle, organizations can defend their applications against evolving threats.
Together, these components create a comprehensive cloud security strategy that protects against data breaches, unauthorized access, and other cyber threats, ensuring the integrity and availability of cloud-hosted assets.
How is Cloud Security Different from Cybersecurity?
Cloud security protects data, applications, and services within cloud environments, focusing on cloud-based threats and vulnerabilities. Cybersecurity is a broader term that protects all digital systems, networks, and data, including those on-premises, in the cloud, or across hybrid environments. Cloud security is a specialized subset of overall cybersecurity practices.
Benefits of Cloud Security
Cloud security provides several essential benefits for maintaining the integrity and reliability of an organization’s digital infrastructure.
First, it offers protection against data breaches and theft, ensuring that sensitive information, whether it’s customer data, intellectual property, or internal communications, remains secure from unauthorized access and cyber threats. Additionally, cloud security contributes to cloud services’ high availability and reliability, minimizing downtime and ensuring that users have continuous access to applications and data, which is critical for maintaining business operations.
Making GenAI Work for Cybersecurity
Join Nvidia and Balbix as they explore how to apply GenAI to cybersecurity, avoid common pitfalls, ensure data privacy, and uncover the true costs of building and maintaining a GenAI solution.


Another significant benefit is the cost savings associated with reduced downtime and fewer security incidents, as robust cloud security measures can prevent costly breaches and system failures. Furthermore, strong cloud security helps organizations maintain compliance with regulatory standards by protecting data according to industry-specific requirements, which is vital for avoiding legal penalties and reputational damage.
Lastly, by safeguarding digital assets, cloud security enhances customer trust, increases customer loyalty and satisfaction, and ultimately contributes to a company’s long-term success.
Challenges of Cloud Security
As cloud adoption accelerates, organizations face numerous security challenges that can jeopardize their operations and data.
Siloed Visibility of Cybersecurity Posture
The complexity of modern IT environments, especially hybrid and multi-cloud deployments, has led to fragmented security monitoring. Traditional tools often provide isolated views of cloud and on-premises environments, forcing security teams to juggle multiple dashboards. This disjointed visibility increases the risk of oversight, making the management of a unified security posture error-prone and inefficient.
Narrow Attack Vector Coverage
While misconfigurations remain a primary attack vector in cloud environments, over 100 attack vectors can threaten cloud security. These include unpatched software, weak encryption, and poor password practices. Many security tools lack comprehensive monitoring across all these vectors, leaving critical gaps. For instance, an attacker could exploit weak on-prem credentials to access cloud applications if the same passwords are reused and not adequately monitored.
Inability to Prioritize Risk
With the sheer volume of alerts generated by cybersecurity tools, security teams can become overwhelmed, leading to potential risks being overlooked. This is particularly challenging when assets are distributed across cloud and on-premise environments, as many tools need help assessing and prioritizing these risks effectively.
Inadequate Cloud Security Posture Automation
Inadequate cloud security posture automation further compounds these challenges. With thousands of assets and vulnerabilities to manage, manual handling of cyber risk is no longer feasible. However, many cloud security tools lack the advanced analytics and automation needed to manage these risks in real time, exposing organizations to prolonged vulnerability periods.
Subjective Cyber Risk Analysis
Finally, subjective cyber risk analysis hampers effective decision-making. Traditional methods of quantifying cyber risk often rely on subjective estimates, leading to inconsistent assessments. Organizations need a more objective approach as the attack surface grows across on-premises, hybrid, and multi-cloud environments. Effective cyber risk quantification (CRQ) models can provide real-time insights, enabling security teams to prioritize key risk issues and recommend targeted mitigation actions.
Implementing Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) helps organizations maintain a secure cloud environment and involves continuously monitoring and managing cloud configurations to ensure they align with best practices and compliance standards.
CSPM tools like Balbix automatically detect misconfigurations, potential risks, and compliance violations, enabling organizations to address vulnerabilities and reduce their cloud attack surface proactively. Integrating CSPM into a cloud security strategy strengthens overall security by providing real-time visibility and automated remediation.
How Does Balbix Help?
Balbix enhances cloud security by providing comprehensive visibility across cloud and on-premise environments. Our solution combines Cyber Asset Attack Surface Management (CAASM) with Risk-Based Exposure Management and Cyber Risk Quantification (CRQ). This allows organizations to prioritize and mitigate risks, such as misconfigurations and vulnerabilities while quantifying breach risks in monetary terms.
Frequently Asked Questions
- Why is cloud security important?
-
Cloud security is important because it protects sensitive data, ensures compliance with regulatory requirements, and safeguards cloud infrastructure from threats such as data breaches, unauthorized access, and cyberattacks. With the growing adoption of cloud services, robust security measures are critical for maintaining trust and preventing costly incidents.
- What are the key components of cloud security?
-
Key components of cloud security include data encryption, identity and access management (IAM), firewalls, intrusion detection and prevention systems, and security monitoring. These elements work together to protect cloud environments from vulnerabilities and threats.
- How is cloud security different from traditional IT security?
-
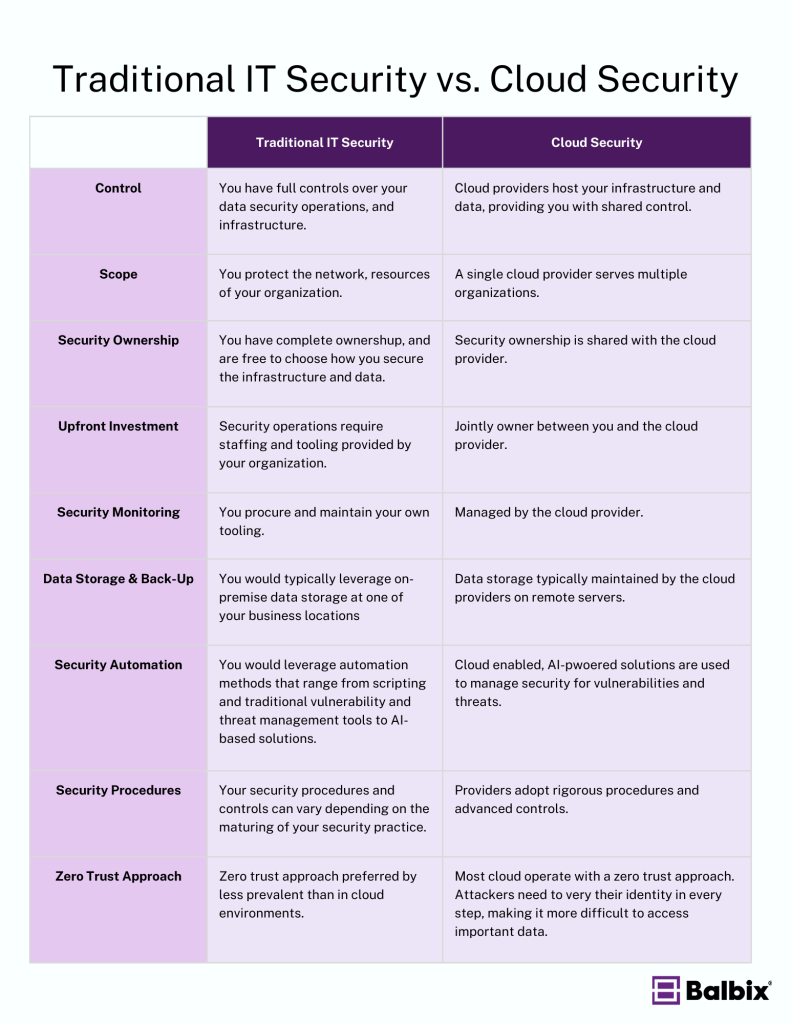
Cloud security differs from traditional IT security by focusing on securing cloud-based environments, which are often distributed and rely on shared responsibility between cloud providers and customers. While traditional IT security focuses on securing on-premise infrastructure, cloud security requires managing data, applications, and resources in a dynamic and flexible cloud environment.
- Who is responsible for cloud security?
-
Cloud security is a shared responsibility between cloud service providers (CSPs) and their customers. CSPs typically secure the infrastructure, while customers secure the data, applications, and configurations within the cloud.