The Internet of Things (IoT) refers to the vast and interconnected network of physical objects (things) that communicate with each other through the internet. Driven by low-cost computing and cloud advancements, the technology seamlessly combines the digital and physical worlds, enabling everything from smart home devices and medical equipment to industrial systems to exchange data.
Defined by IDC as “a network of uniquely identifiable endpoints that communicate without human interaction,” IoT has become a prevalent and practically ubiquitous mainstay in modern technology for consumers, businesses, and government.
What Is IoT Security?
IoT security covers the strategies, tools, and processes designed to protect the various components of the Internet of Things, including physical devices, applications, data, and network connections. The key issue for IoT security is that IoT devices are often not secure by default. For example, a device may ship with an administrator password of ‘password.’
With frequent vulnerability discoveries in IoT systems, robust security measures are crucial to protect availability, integrity, and confidentiality. These measures include hardening devices, monitoring, updating firmware, managing access, responding to threats, and addressing vulnerabilities. As IoT systems could be an entry point into a broader network, securing these devices is critical to prevent breaches.
The Importance of IoT Security
IoT is widely recognized as one of the most significant security challenges facing consumers, organizations, and governments. With billions of devices connected worldwide, the attack surface has expanded dramatically.
According to GSMA Intelligence, the definitive source of data and analysis for the mobile industry and beyond, covering all operators worldwide, the number of IoT devices is expected to reach 25 billion by 2025, highlighting the critical need for robust security measures. Despite their uber convenience and value, IoT systems also introduce unprecedented risks due to the often-overlooked security aspects during development.
The truth is that manufacturers tend to prioritize functionality over security, leaving these devices particularly vulnerable to exploitation. The password example mentioned above is not uncommon. This oversight underscores the essential role of IoT security, which requires more protection for these devices and the broader networks they connect to.
As the number of IoT devices continues to skyrocket, so does the responsibility of users, IT teams, and organizations to implement and maintain adequate security measures. Otherwise, far too quickly, these ubiquitous devices can become targets for cyberattacks.
12 Common IoT Security Concerns
The proliferation of IoT devices across various sectors has brought significant security challenges that are often overlooked. Unlike traditional IT systems, IoT devices frequently lack rigorous security protocols, making them prime targets for cyberattacks.
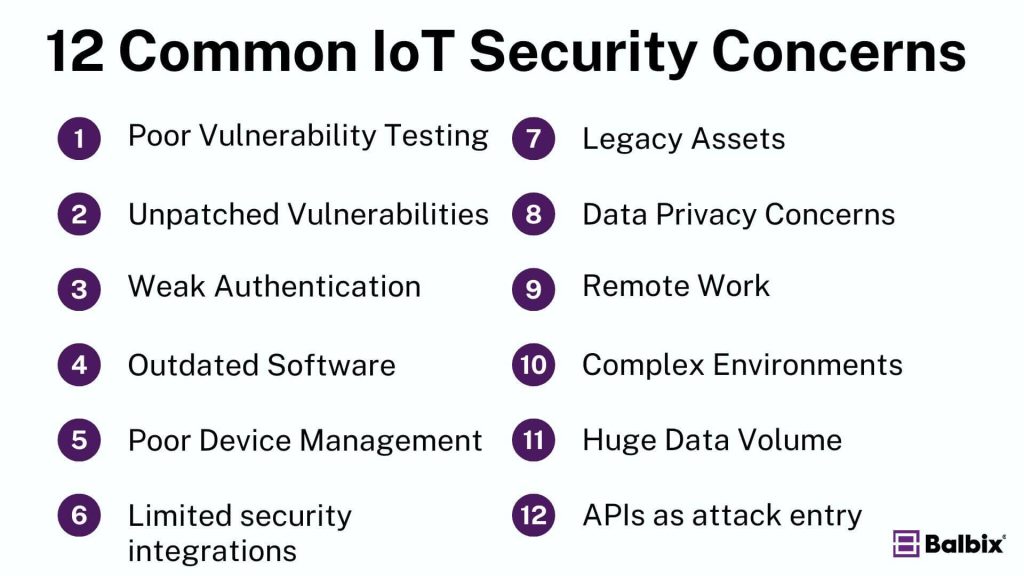
Here are some of the most pressing security concerns associated with IoT devices you need to know about:
Poor vulnerability testing: Many IoT devices are developed with a focus on functionality instead of security. So vulnerability testing—critical for identifying weaknesses before deployment—is often neglected or poorly executed.
Unpatched vulnerabilities: Too many IoT devices run unpatched vulnerabilities due to a lack of available updates or the complexity of applying patches. IoT devices often remain used for extended periods, with no updates being applied or available.
Default passwords and weak authentication: Like the example above, a standard (yet dangerous) practice is for IoT devices to ship with default passwords, which users frequently neglect to change. Even if passwords are updated, they are often weak and easily compromised.
Outdated firmware and software: Once deployed, IoT devices are often left running on outdated firmware or software, which makes them vulnerable to newly discovered exploits.
Making GenAI Work for Cybersecurity
Join Nvidia and Balbix as they explore how to apply GenAI to cybersecurity, avoid common pitfalls, ensure data privacy, and uncover the true costs of building and maintaining a GenAI solution.


Poor device management and visibility: IoT devices are frequently deployed outside the purview of IT departments, leading to a lack of visibility and control over them. This is another example of Shadow IoT, which complicates efforts to secure networks as IT teams struggle to manage and protect assets they’re unaware of.
Limited security integration: The diversity and sheer number of IoT devices present significant challenges for integration into existing security frameworks. Many devices simply aren’t designed to be compatible with traditional security systems.
Legacy assets: Many industries rely on legacy IoT devices designed and deployed years ago. These older devices often lack the security features of more modern technology, and organizations are reluctant to move on from them due to the cost and complexity of upgrading or replacing them.
Data privacy concerns: The sheer volume of data generated by IoT devices raises significant privacy issues: without proper safeguards, sensitive data can be exposed, leading to breaches and misuse.
Remote work: The rise of remote and hybrid work has expanded the attack surface, as IoT devices often connect to home networks with weaker security protocols.
Complex Environments: IoT ecosystems often operate within complex environments where multiple devices, platforms, and protocols interact, creating complexity that can open security gaps if not adequately managed.
Overwhelming data volume: The massive amount of data generated by IoT devices can overwhelm traditional data management systems, making it difficult to ensure data integrity and security.
APIs as entry points for attacks: APIs used in IoT environments are often targeted for attacks such as SQL injection, distributed denial of service (DDoS), and MITM attacks.
Examples of IoT Security Incidents
When IoT devices are compromised, bad things can happen. Here are three recent breaches and the mother of all IoT cyberattacks.
Ring Home Security Camera Breach: Amazon-owned Ring faced a significant security breach when cybercriminals accessed numerous home security cameras by exploiting weak, recycled, and default credentials. The attackers could view live feeds and even communicate through the devices.
Mirai Botnet Attack (2016): The Mirai botnet is one of the most infamous examples of IoT-related cyberattacks. In 2016, the botnet was responsible for one of the largest distributed denial-of-service (DDoS) attacks recorded. It compromised hundreds of thousands of IoT devices, such as cameras and routers, by exploiting default login credentials. The infected devices were then used to overwhelm targeted websites and services, including major companies like Twitter and Netflix, causing widespread disruptions.
Implementing IoT Security in 3 Steps
By following these three steps, organizations can build a comprehensive IoT security strategy that addresses the unique challenges of managing these devices and mitigates the risks associated with using them.
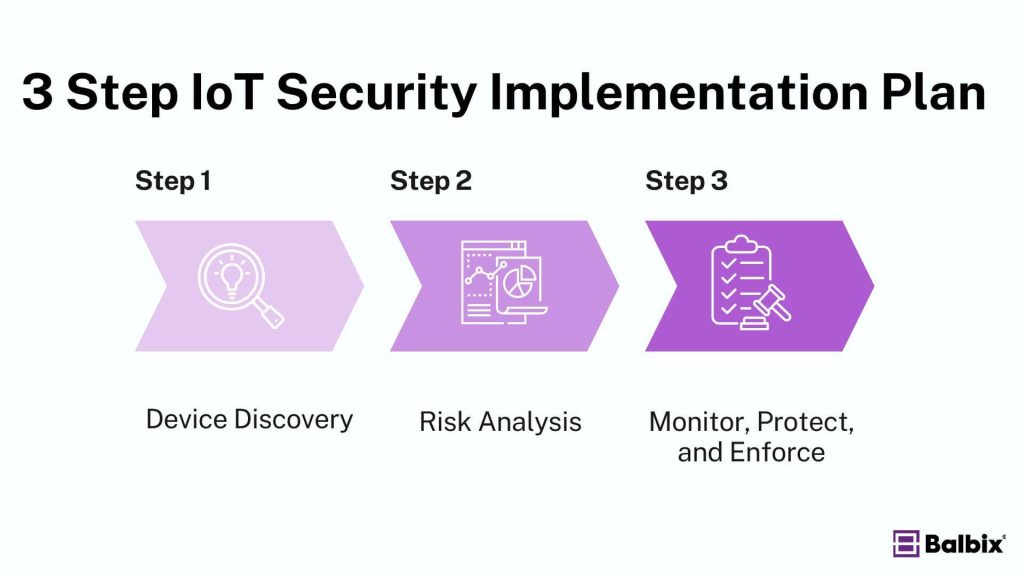
Step 1: Device Discovery
The first step in securing IoT is identifying the devices connected to your network, which typically uses a device identification and discovery tool to automate three critical IoT security functions:
- Autonomously and continually detect, profile, and classify IoT devices on the network
- Maintain a real-time inventory of devices
- Provide risk intelligence and insights for each asset class by continuously monitoring across attack vectors.
Step 2: Risk Analysis
Once all IoT devices are identified, the next step is to conduct a thorough risk analysis, which assesses the vulnerabilities and potential threats associated with each device and its communication channels.
Key components of this step include:
- Vulnerability assessment: Regularly scan IoT devices for known vulnerabilities and apply patches or updates where necessary to help identify weak points in the system that attackers could exploit.
- Threat modeling: Evaluate how threats could impact the IoT ecosystem, including determining how attackers might use compromised devices to infiltrate networks or launch larger-scale attacks.
- Risk prioritization: Not all devices pose the same level of risk: prioritizing devices based on their criticality to operations and their exposure to threats allows for more focused security efforts.
Step 3: Monitor, Protect, and Enforce
The final step involves actively monitoring the IoT environment, applying protective measures, and enforcing security policies to maintain a secure posture over time, which include:
- Continuous monitoring: Implement continuous monitoring to detect anomalies, unauthorized access, and deviations from normal device behavior.
- Network segmentation: Segmenting IoT devices is equally important as any other sensitive network area that shouldn’t be connected to the main network.
- Security enforcement: Enforce security policies such as mandatory updates, strong authentication, and encryption, and take corrective actions when deviations occur.
- Incident response: Prepare a robust incident response plan specifically for IoT-related incidents.
Conclusion
As IoT makes its way into every aspect of our lives and work — from smart homes to industrial systems — the potential risks associated with these devices cannot be overlooked.
Implementing a robust IoT security strategy involves comprehensive steps, including device discovery, risk analysis, and continuous monitoring and protection. Each of these strategies is crucial in defending against the unique challenges posed by IoT devices.
Leveraging advanced tools and platforms can make a huge difference for organizations looking to boost their IoT security. Balbix offers solutions such as, Continuous Automated Asset and Security Management (CAASM) and Cyber Risk Quantification (CRQ), helping organizations automatically discover and profile devices, assess real-time risks, and enforce security measures effectively.
Making Balbix part of your security strategy empowers you to stay ahead of potential threats and ensure the security and resilience of your IoT environment.
Frequently Asked Questions
- What are the main security challenges in IoT?
-
IoT security challenges include device vulnerabilities, weak encryption, insufficient updates, and data privacy risks.
- How do IoT devices pose a risk to cybersecurity?
-
IoT devices can be exploited due to weak security configurations, making them vulnerable entry points for hackers.
- What are the biggest privacy concerns with IoT devices?
-
Collecting and storing sensitive data by IoT devices can lead to privacy breaches if not properly secured.
- How can businesses improve IoT security?
-
Businesses can enhance IoT security by implementing strong encryption, regular firmware updates, and network segmentation.
- What role does encryption play in securing IoT devices?
-
Encryption helps protect data transmitted by IoT devices, preventing unauthorized access and safeguarding sensitive information.


