Vulnerability management is essential for protecting organizations from cyber threats, but many companies fall short in critical areas, exposing them to unnecessary risks.
This article explores six common vulnerability management pitfalls—from outdated scanning methods to incomplete asset visibility—and offers practical solutions. Organizations can strengthen their cybersecurity posture by addressing these challenges and effectively reducing risk.
Pitfall #1: Relying on Outdated Scanning Methods
Many organizations are stuck using traditional vulnerability scanners that only detect known vulnerabilities. This outdated approach is like locking the front door while leaving the windows wide open—because new threats constantly emerge, relying solely on static scans is a recipe for disaster.
Solve It: Upgrade to Continuous, AI-Powered Scanning
Organizations must adopt continuous vulnerability detection powered by AI and machine learning to move beyond outdated scanning methods. Using data sources such as SBoM (Software Bill of Materials) can reduce the wait cycle on inferencing vulnerability by completing a software vulnerability lookup. This is completed outside of a scan or agent.
Balbix’s platform continuously scans the entire attack surface, using AI to predict and identify emerging and unknown vulnerabilities. By moving to continuous, real-time monitoring, organizations can close the gap and stay ahead of evolving threats.
Pitfall #2 Treating Vulnerability Management as a One-Time Project
Some organizations approach vulnerability management like a checkbox activity. They run scans, patch a few holes, and call it a day. But cyber risks don’t take time off. Effective vulnerability management is a continuous process, not a one-time task. Neglecting ongoing monitoring and updates will leave you exposed.
Solve It: Make Vulnerability Management a Continuous Cycle
Vulnerability management isn’t a one-and-done task. Organizations should implement a continuous lifecycle approach with ongoing discovery, prioritization, remediation, and validation.
Balbix automates these processes, ensuring that vulnerabilities are constantly identified and addressed, with results fed back into the system for continuous improvement. It turns vulnerability management into a seamless, automated cycle rather than a periodic project. In its operating capacity, it should be referred to as a “Program of works.”
Pitfall #3: Failing to Prioritize Risk
Not all vulnerabilities are created equal, yet too many teams waste time fixing low-risk issues while ignoring critical vulnerabilities with real-world exploitability. A risk-based approach that considers the business impact is the only way to prevent drowning in low-priority fixes.
Stop Sabotaging Your Cybersecurity
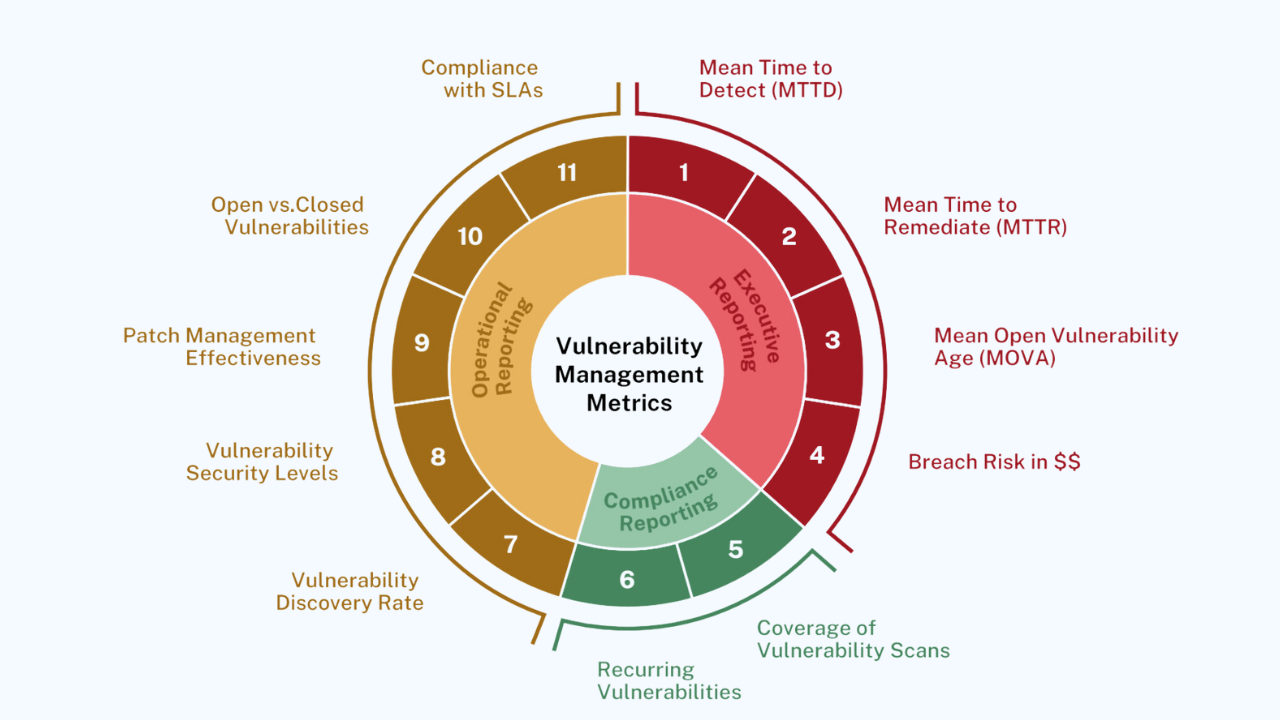
Avoid the 11 common vulnerability management pitfalls

Solve It: Adopt Risk-Based Vulnerability Prioritization (RBVM)
Stop wasting time on low-risk vulnerabilities by adopting a risk-based approach. Balbix integrates business context—such as the criticality of assets, exposure, threat intelligence, and the effectiveness of existing security controls—into its risk calculations. Then, it prioritizes vulnerabilities based on potential impact, allowing security teams to focus on what truly matters: critical vulnerabilities that pose the highest risk to the business operations and assets.

Pitfall #4: Ignoring Asset Visibility and Inventory
How can you protect what you don’t even know exists? Organizations often fail at vulnerability management because they lack complete visibility of their IT environment. Without an up-to-date asset inventory, unmanaged devices, shadow IT, and cloud misconfigurations slip through the cracks, leaving huge blind spots in your defenses.
Solve It: Ensure Full Asset Visibility
Complete visibility is crucial for effective vulnerability management. Balbix provides automated asset discovery and inventory, leveraging AI to track every device, application, and cloud asset across the organization. With Balbix’s comprehensive visibility, organizations can eliminate shadow IT and unmanaged assets, gaining a full understanding of their attack surface to protect all assets, not just a few. By cross-referencing a number of data sources, a clearer, more precise view of the asset is achieved.
Pitfall #5: Overwhelming Teams with Volume, Not Intelligence
It’s easy to flood security teams with vulnerability data—every scan generates a mountain of issues. But sheer volume without actionable intelligence is useless. Organizations that don’t focus on distilling meaningful insights from this noise leave their teams paralyzed and patching aimlessly.
Solve It: Leverage AI to Deliver Actionable Intelligence, Not Noise
Instead of overwhelming teams with raw data, Balbix’s AI-powered platform correlates and analyzes vulnerabilities to provide clear, actionable insights. It prioritizes the most critical vulnerabilities based on risk and business impact, delivering specific remediation steps and projects. This drastically reduces noise, allowing teams to focus on addressing the highest risks rather than drowning in irrelevant data. When everything becomes critical, then nothing is. Establishing a measurable metric becomes a key objective.
Pitfall #6: Lack of Accountability and Ownership
An organization’s biggest mistake is not defining clear accountability for vulnerability management. When no one owns the risk, vulnerabilities languish unfixed. Security teams, IT operations, and business leaders must align on who addresses which vulnerabilities or nothing meaningful gets done.
Solve It: Establish Clear Ownership and Accountability
Balbix’s platform assigns specific ownership of remediation tasks to ensure vulnerabilities don’t slip through the cracks. It integrates with ticketing systems to create actionable projects and assign them to the correct stakeholders, such as IT or business leaders.
Built-in tracking and reporting ensure the right people are held accountable, driving vulnerabilities toward resolution. Outside of establishing an owner for an asset, creating a temporary non-production hold will bring out the actual owners in the case where none are found. Allowing an asset to continue without an owner is a dangerous practice.
Frequently Asked Questions
- How does continuous, AI-powered scanning differ from traditional vulnerability scanning methods in effectiveness and efficiency?
-
Continuous, AI-powered scanning is like having a smart security guard on duty, constantly watching for dangers and quickly learning about new ones. Traditional methods are more like a security check that happens occasionally.
- What features does Balbix offer to help organizations prioritize vulnerabilities based on risk, and how does it integrate business context into its calculations?
-
Balbix provides tools that assess and rank vulnerabilities in an organization’s network by risk level. It does this by considering the potential impact of each vulnerability on the business. This means it looks at how critical the systems affected by the vulnerabilities are to the organization’s operations. By integrating this business context, Balbix helps companies focus on fixing the most dangerous vulnerabilities first, ensuring better protection with more efficient resource use.
- Can Balbix's platform be integrated with existing cybersecurity tools and infrastructures within an organization, and if so, how?
-
Yes, Balbix’s platform is designed to work alongside an organization’s existing cybersecurity tools and infrastructure. It seamlessly integrates through various methods, such as APIs, to enhance the organization’s security posture.
Doing so provides a more comprehensive view of the security landscape, identifying vulnerabilities and recommending actionable insights without replacing current systems. This makes it easier to strengthen defenses without overhauling existing security setups.