There’s little doubt that cost cutting and consolidation will be hot topics for the foreseeable future. For the past decade, IT and infosec teams have focused on supporting the strategy of the business, with less regard for cost cutting. With shift in the macroeconomy will come a shift in focus towards eliminating overlap and waste.
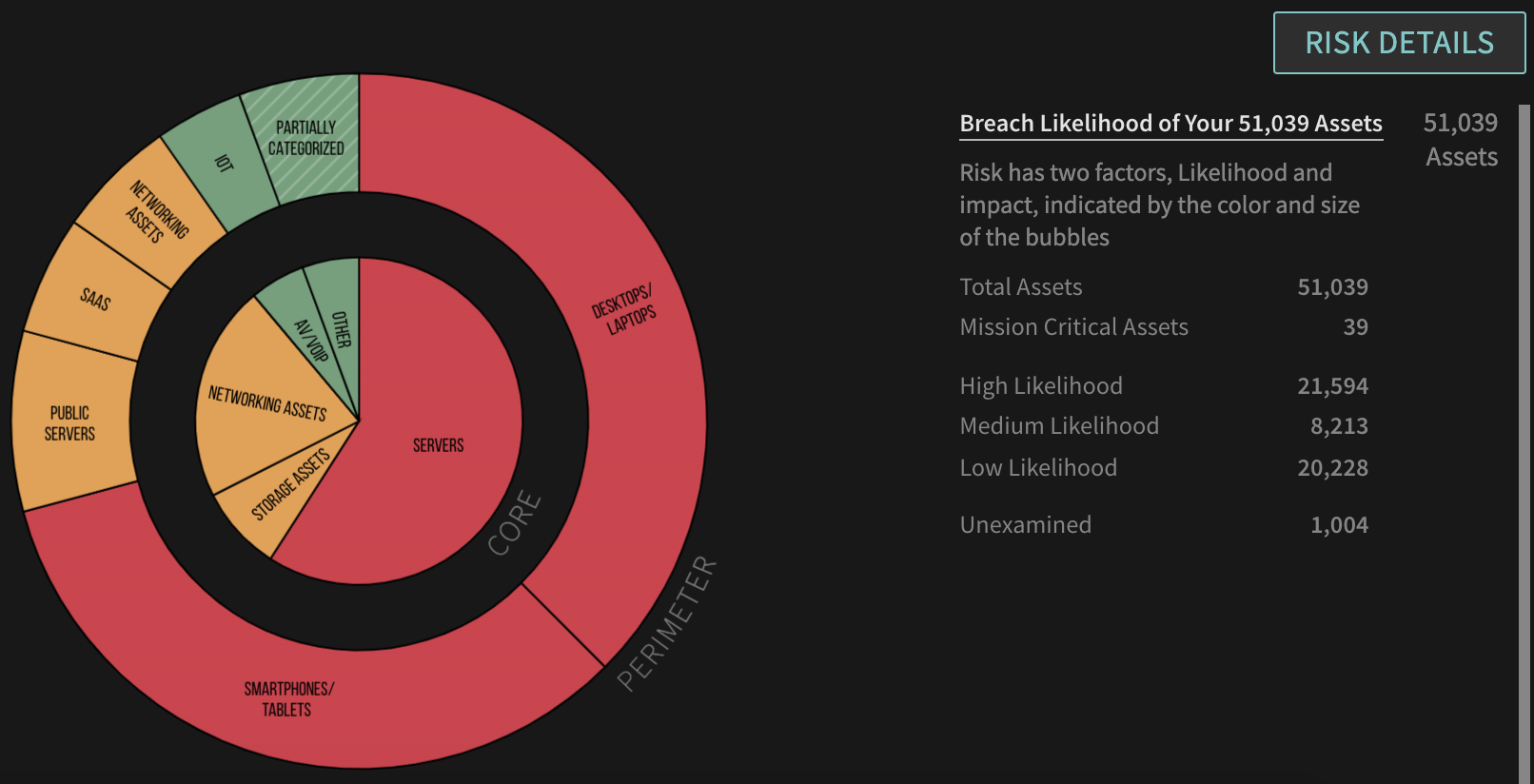
For those that were fortunate enough to rise to leadership positions over the past 10 years, this exercise will be a first, making it difficult to know where to begin. Since you can’t improve what you can’t measure, the right place to start is with a complete, accurate, up-to-date IT asset inventory.
Getting a comprehensive inventory can be a challenge, but hopefully this isn’t a start from scratch, manual mission. You probably have a not too horribly outdated CMDB – this can form the basis for an effort to bring it up to date. Or, you could look at something like your Vulnerability Management system, which should provide an inventory of managed assets, which is a starting point and can appended with other assets not covered by that system. If you’re a Balbix customer, a comprehensive, accurate, real-time inventory is always available directly through the system:
 Low Hanging Fruit
Low Hanging Fruit
Once you have a complete inventory, you can begin the cost savings and consolidation process. One piece of low hanging fruit is unused software. The typical organization wastes about 37% of their budget on unused software. Many Balbix customers report savings of up to tens of millions of dollars once they’ve used the platform to identify software that is not in use.
Infosec Bonus
Beyond cost savings, another benefit of removing unused software is that you shrink your overall attack surface. If you’ve already removed all instances of Internet Explorer, for example, you wouldn’t need to jump on trying to patch that software when the next ransomware outbreak hits. The organization featured in this post is a great example. They were able to reduce their installed base of (unused) Firefox browsers by over 97%, eliminating the vast majority of effort necessary to respond whenever a new Firefox CVE is issued.
