Continuous Threat Exposure Management (CTEM) is a proactive approach that continuously identifies, assesses, and mitigates cyber threats. It’s not just about reacting to breaches; it’s about staying one step ahead. Unlike traditional cybersecurity methods that might wait for an attack to occur, CTEM emphasizes ongoing exposure management.
CTEM doesn’t rely on periodic assessments. Instead, it ensures that your organization constantly monitors threats, ensuring you catch them before they cause damage. This continuous cycle makes CTEM a powerful ally in cybersecurity.
The 5 Stages of CTEM
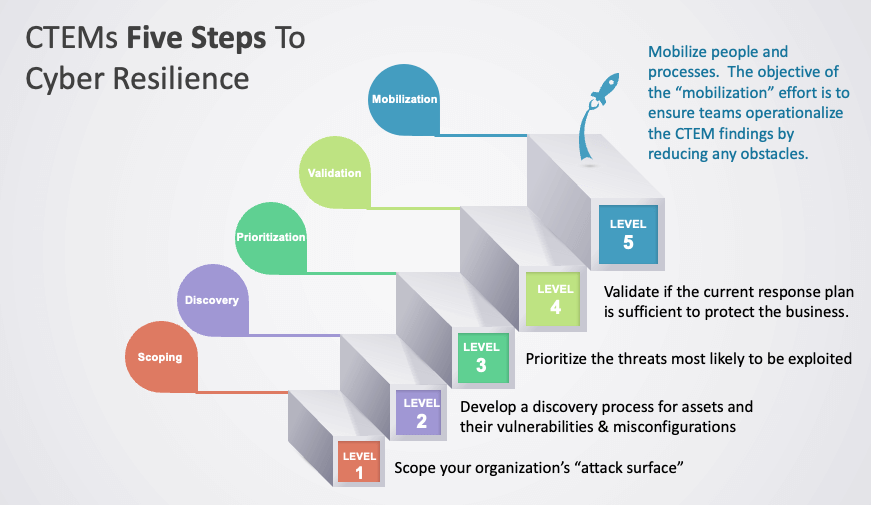
Scoping Stage
The first step in CTEM is defining the purpose and scope of your exposure assessment. What’s the goal? Which assets need protection? By aligning this stage with your business goals and risk management strategies, you’ll ensure that your efforts are focused where they matter most. This foundational step is crucial for setting a clear direction for your CTEM efforts.
Discovery Stage
Next comes the discovery stage, where the real detective work begins. Here, you’re identifying and classifying vulnerabilities. This could be through automated tools, manual assessments, or both. Tools like vulnerability scanners play a vital role in uncovering potential vulnerabilities that cyber attackers might exploit. Knowing where your vulnerabilities and misconfigurations lie is half the battle won.
Prioritization Stage
Now that you’ve identified vulnerabilities, it’s time to prioritize them. Not all threats are equally severe across all organizations; some exposures pose a greater risk than others. This stage involves ranking vulnerabilities based on impact and likelihood. It’s about smart resource allocation—focusing your efforts on the highest priority threats to ensure efficient use of your resources.
Validation Stage
During the validation stage, you’ll take a close look at real risks and try out ways to handle them. This phase identifies which vulnerabilities are real threats to your system or process. You’ll use both manual and automated methods to make your defenses strong and reliable. Manual checks give a better grasp of tricky vulnerabilities, while automated tools help with quick and wide-ranging threat detection. These methods help build a solid cybersecurity setup to handle new challenges and stop possible breaches.
Mobilization Stage
Finally, there’s the mobilization stage. This is where you implement security controls and focus on continuous improvement. Cyber threats are always changing, so your CTEM processes should account for that.. Regularly updating and improving them is key to staying ahead and ensuring long-term consistency of security levels.
Benefits of CTEM
Adopting CTEM comes with a host of benefits. First and foremost, it allows for proactive risk management and early threat detection. By identifying threats before they can wreak havoc, you minimize potential damage. This approach also leads to efficient resource allocation, as you focus your efforts where they’re most needed.
Furthermore, CTEM enhances your organization’s overall security posture. CTEM revolves around continuously monitoring for any exposures, and you significantly reduce your risk exposure. This ongoing methodology also fosters a culture of continuous improvement, ensuring that your security strategies evolve alongside emerging vulnerabilities and threats.
CTEM & Exposure Management
CTEM isn’t a one-size-fits-all fix; it works nicely with your exposure management plans. You reduce attack risks by mixing CTEM with your security setups and tools. This teamwork between CTEM and exposure management boosts your team’s ability to spot and handle possible threats well.
How does CTEM differ from Traditional Vulnerability Management?
CTEM is changing the game in vulnerability management. Instead of sticking to those traditional periodic scans, it monitors threats as they happen and focuses on what matters to your business.
Due to limited asset visibility, traditional vulnerability management struggles with missing mobile, IoT, and cloud systems vulnerabilities. It also often takes too long to spot new vulnerabilities, and there’s no smart way to determine which threats are most important. Plus, the process lacks links between vulnerabilities and what matters to a business.
But with Continuous Threat Exposure Management (CTEM), you cover the bases of your entire attack surface regardless of where it sits—mobile, IoT, Cloud, or on-Premise. It continuously scans for vulnerabilities as they arise and uses threat intelligence to spot active exploits across other organizations.
CTEM simplifies cybersecurity by combining all your existing controls into one priority list. It connects vulnerabilities to their business impact and financial risk, so you know what to focus on. It uses this info to rank risks, helping you direct attention where it matters most. Plus, it works seamlessly with your IT and security tools to cover every angle.
It even automates finding, ranking, and fixing issues and offers clear reports and visualizations. You’ll get metrics like Mean Time to Detect (MTTD), Mean Time to Resolve (MOVA), Mean Time to Patch (MTTP), and predictions on breach impacts. These allow for fine-tuning and improving internal processes where they matter.
What Does Gartner Say About CTEM?
Gartner, a leading research and advisory company, offers valuable insights into the world of CTEM. According to Gartner, CTEM is essential for reducing breaches and enhancing cybersecurity. Their research highlights future trends in CTEM, emphasizing its growing importance in the digital landscape.
Gartner’s statistics and predictions underscore the significant impact CTEM can have on reducing breaches and improving overall security. Their recommendations encourage organizations to adopt CTEM for enhanced protection and resilience.
Conclusion
Continuous Threat Exposure Management (CTEM) is a key tool in fighting cyber threats. It’s about staying proactive with constant monitoring and improvements, which makes CTEM a huge help for any organization. It boosts security, reduces risk, and keeps you one step ahead of your next cyber threat.
Balbix empowers organizations adopting CTEM by providing an AI-powered platform for continuous risk assessment and real-time vulnerability prioritization. With Balbix, security teams can streamline exposure management, focusing resources on the highest-impact risks to strengthen overall cybersecurity posture.
Frequently Asked Questions
- Is CTEM required for exposure management?
-
CTEM, or Continuous Threat Exposure Management, is a strategic framework for developing an effective exposure management strategy. This action plan outlines the steps and protocols to identify, assess, and mitigate potential threats, ensuring a structured approach to safeguarding resources and minimizing risks. By implementing CTEM, organizations can enhance their resilience against diverse threats while optimizing their security posture.
- What are the 5 Stages of CTEM?
-
The five stages of CTEM are: Scoping, Discovery, Prioritization, Validation and Mobilization.


