Earlier today Tech Mahindra (TechM), a leading global provider of consulting services and solutions announced a strategic partnership with Balbix. This is a great thing for TechM’s customers, and for businesses of all sizes generally. Here’s why…
With Balbix’s help, TechM is launching a new managed service offering called an intelligent security operations center (iSOC). While a traditional SOC is focused primarily on the reactive handling of security events, an iSOC tries to predict and proactively avoid cyber-breaches.
This is the world’s first offering from a large managed service provider that aims to re-orient security decision making from reactive to proactive.
The Reactive Nature of a Traditional SOC
When a security alarm goes off in a traditional SOC, security operations personnel aim to handle the incident as quickly as possible so that a breach is avoided. In recent years, the rate and variety of daily security events faced by most SOCs has increased rapidly to the point that defenders can’t keep up. While adoption of managed services and automated response in security incident handling helps the situation somewhat, the fundamentally reactive nature of traditional security operations has led to an increase in the rate of major breaches.
An iSOC is Self-Learning and Proactive
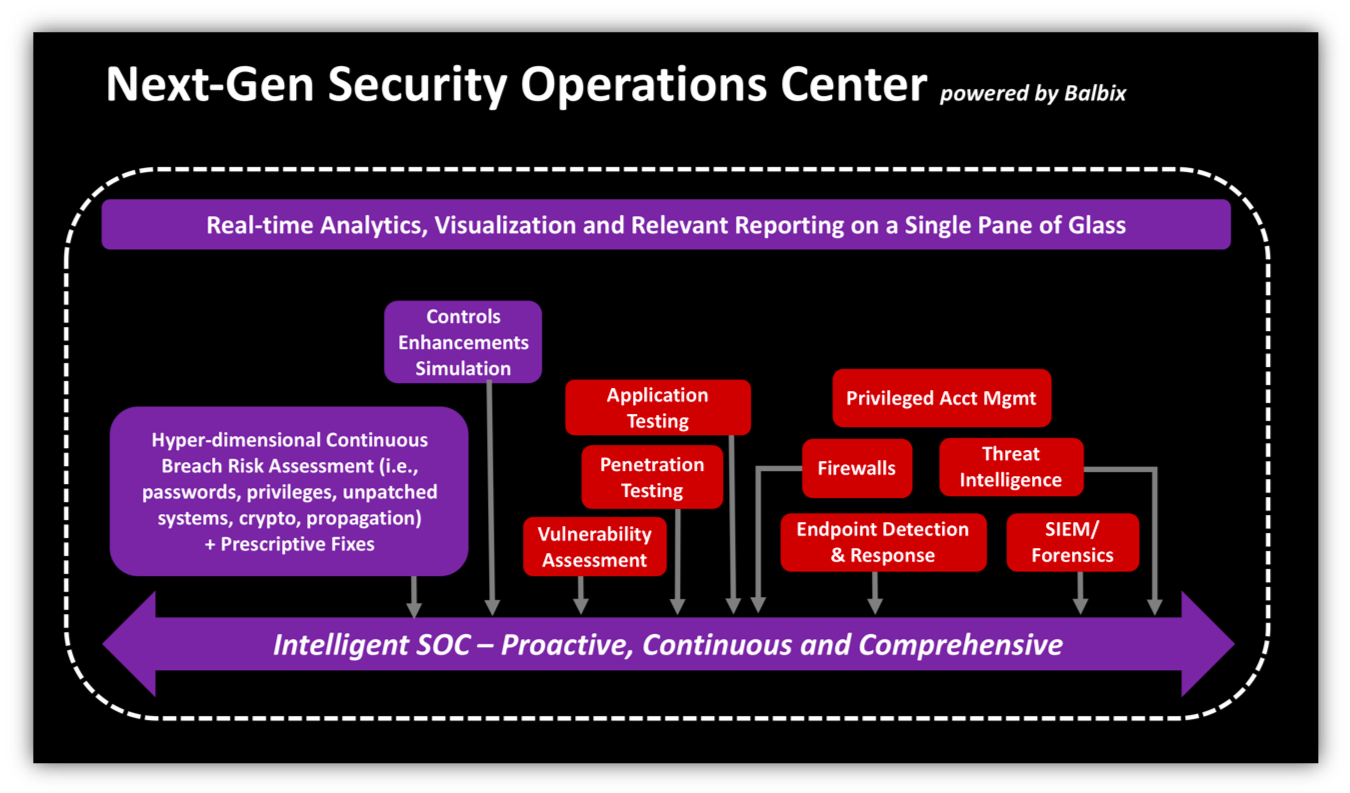
A TechM iSOC has all of the capabilities of a traditional SOC, but very different dynamics and goals, and as a result is much more effective in avoiding breaches. An iSOC continuously and automatically discovers and monitors customer IT assets and users for hundreds of breach risk factors. A primary differentiating feature of an iSOC is continuous and comprehensive risk assessment. Line-speed network traffic, security events and changing endpoint state is continuously analyzed by Balbix’s pipeline of Deep Learning and other advanced AI algorithms to reveal relevant breach risk insights, which enable TechM’s expert security personnel to take appropriate proactive mitigating steps.
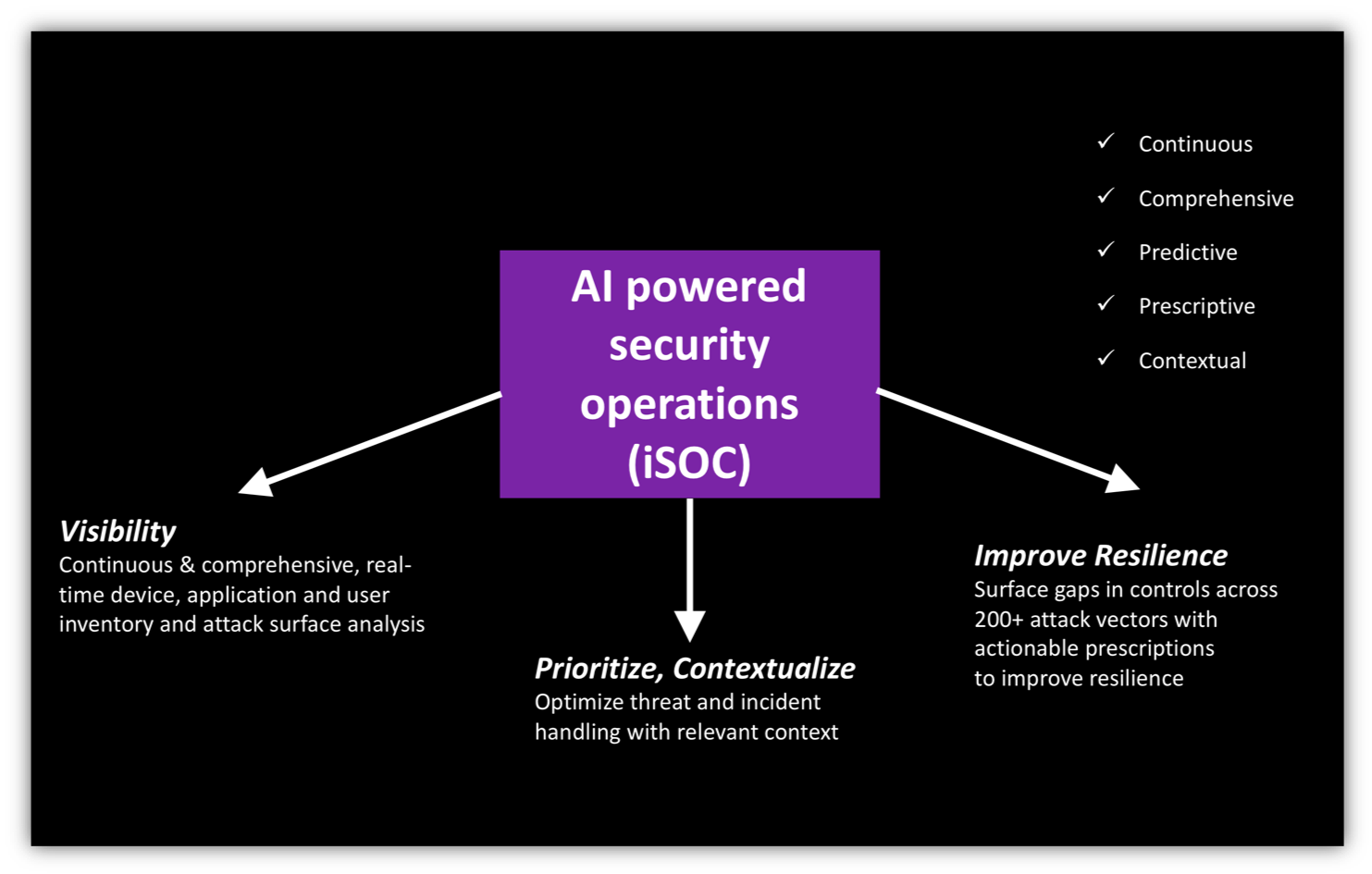
Any identified vulnerabilities are prioritized based on business criticality and the external threat model, and TechM’s SOC personnel receive actionable prescriptions which can be acted upon by a combination of automation and human efforts; thereby preventing many security incidents from happening.
As an example, consider the problem of managing security updates. A TechM iSOC is able to automatically discover all software components that are missing security updates and rank them based on business criticality. The system generates directions for update testing and patching workflows prioritized by actual risk to the business. The goal is to achieve a security patching frequency that is aligned with the desired SLAs for mean-time-to-patch based on asset criticality and breach risk. Contrast this with a traditional SOC which typically has no-real time notion of an asset’s unresolved vulnerability state, business criticality or relevant compensating controls.
Continuous risk assessment is a huge step up from traditional episodic or 1-shot vulnerability assessment. An iSOC’s AI platform helps customers get a holistic view of (breach) risk and the detailed insights and actionable intelligence provided by the platform is critical for integrated risk management.
Context in Security Operations
When security events do fire, TechM’s iSOC personnel are provided with deep security and business context related to the specific event, available at their fingertips in a single plane of glass (and via API). There is no need to manually collate parameters extracted from an indicator of compromise (IOC) with log and configuration data from multiple security controls and assets.
Security events are thus handled very efficiently in priority order based on business criticality of the assets involved. If you are concerned that a MSSP’s secops personnel lack the correct business context to correctly handle security events relative to an internal security team, you will be very surprised at the type of deep context that is available in a TechM iSOC.
Focus on Resilience
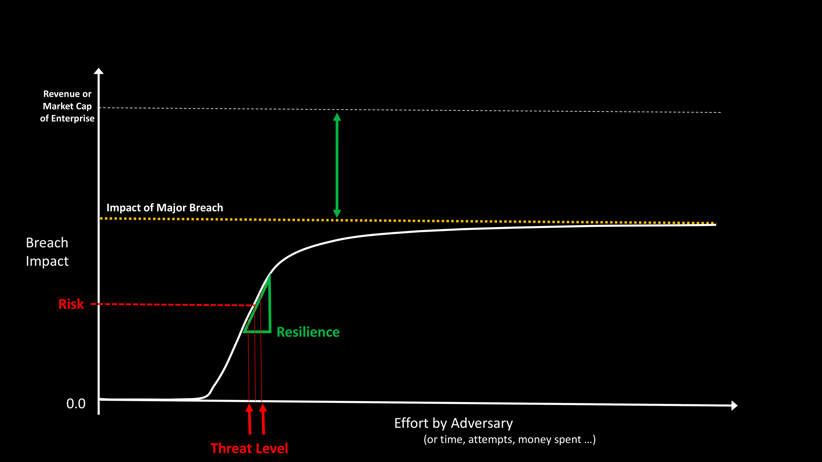
The overall objective of an iSOC is to help maximize the resilience of the network. For lowest breach risk, you want to understand what is on your network, and how breaches might start and move laterally. Your cyber-defenders will want to arrange security controls such that the impact of security attacks is limited in time and in space. And you will want to periodically validate that all mitigating controls are working correctly.
This is exactly what an iSOC does. Balbix continuously measures the effective cyber-resilience of the network understanding areas of risk and possible methods of lateral movement by the adversary. iSOC personnel are provided with actionable insights that can improve resilience. For example, an iSOC analyst might receive a ticket that indicates a specific critical system’s administrator reuses passwords between privileged enterprise accounts and personal accounts, with recommendations to install and enforce 2-factor authentication for this asset and educate the privileged user on avoidance of password sharing via use of a password manager.
Focus on Risk to the Business
Unlike a traditional SOC, an iSOC tries to bring in the notion of risk to all security operations and projects by factoring in business criticality, global and industry specific threat model, and the state of compensating controls on top of system configuration and vulnerability state. This aligns the efforts of the security team with actual business risk, and is a critical step in achieving integrated risk management.
Compliance and Reporting
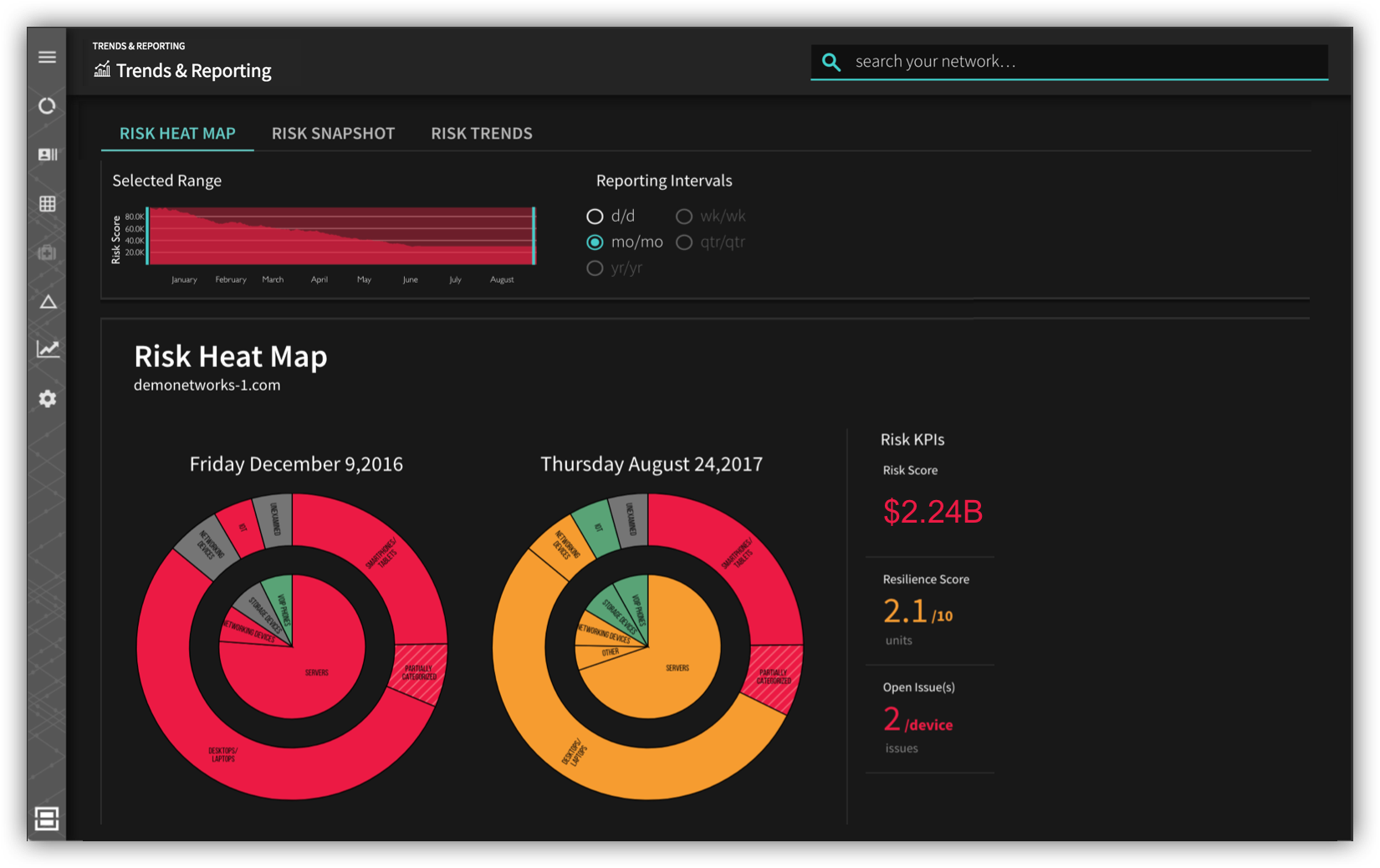
The self-learning and automation capabilities of an iSOC reduce compliance verification cycles from months to minutes. A TechM iSOC is constantly collecting, crunching and analyzing data, and accurately measuring overall breach risk and cyber-resilience. The framework of all calculations is business risk and not just security state. CISOs and CIOs are able to greatly decrease reporting cycles and improve the relevance of reporting to business leaders, the board of directors, auditors and regulators.
The overall objective is that all relevant insights are extracted from millions of security related data points, such that the the right decisions are made and the correct projects are funded and tracked. This is critical to enabling cyber-resilience.
An iSOC is a quantum leap forward in the quest for a cyber-resilient enterprise. We are very pleased to be working with Tech Mahindra in bringing this offering to life.
