March 19, 2024
Creating an accurate inventory of an organization’s assets and applications while ensuring no duplicates or omissions is essential for any IT and security program. Security teams must understand vulnerabilities associated with their assets, their exposure and the blast radius to prioritize assets for remediation and meet their SLAs effectively.
A typical organization has hundreds of thousands of assets in its environment. To get an accurate picture of all assets you must query dozens of tools to resolve conflicts. For example:
Additionally, security teams need to regularly monitor their software, firmware, plugins and ports to identify new vulnerabilities that could increase their risk of exposure. However, using multiple tools to gain visibility into assets and risks can make it difficult for security teams to prioritize remediation efforts effectively. For instance, they need help identifying systems that have reached their end-of-life (EOL) but still run business-critical applications or locating assets running specific versions of Chrome/Firefox or internet-facing assets running FTP services.
To overcome these challenges, Balbix uses AI to analyze IT, security and business data using built-in large language models (LLMs), deep learning, and other specialized ML techniques. An ensemble of models, each with its specific function, provides insights into cyber risks and delivers actionable recommendations. For instance, with Balbix, security teams can identify tens of thousands of assets with Log4J and prioritize remediations for external-facing assets, DMZ assets, and mission-critical/business-critical infrastructure.
Let’s learn how Balbix has improved visibility into the attack surface for hundreds of global organizations.
The first step for any security team is to have a unified view of all assets without duplicates.
However, there are two challenges to overcome:
First, the data comes from different sources and has different formats. This requires security teams to normalize the information coming in from diverse tools. Tools usually report different identifiers, such as hostname, domain name, IP addresses, MAC addresses and unique resource identifiers, to recognize a specific device.
For instance, Configuration Management Databases (CMDBs) report the hostname, while an endpoint agent on the device reports the hostname and associated IP and MAC addresses. A network scanner provides only the IP address or the fully qualified domain name (FQDN). External scanners might only detect the public IP address for the device, and cloud instances could have unique resource identifiers.
Two, the data can be partial, missing, old or incomplete, so a tool needs to fill in the gaps. Data fidelity from a source can be good when fresh but can deteriorate and become unusable as it becomes stale. Overcoming these shortcomings requires sophisticated treatment of incoming data for sanitization and cleansing.
Balbix AI aggregates the data and applies an ensemble of language models and neural information retrieval mechanisms to deduplicate, normalize and correlate asset data to provide a comprehensive and unified inventory.
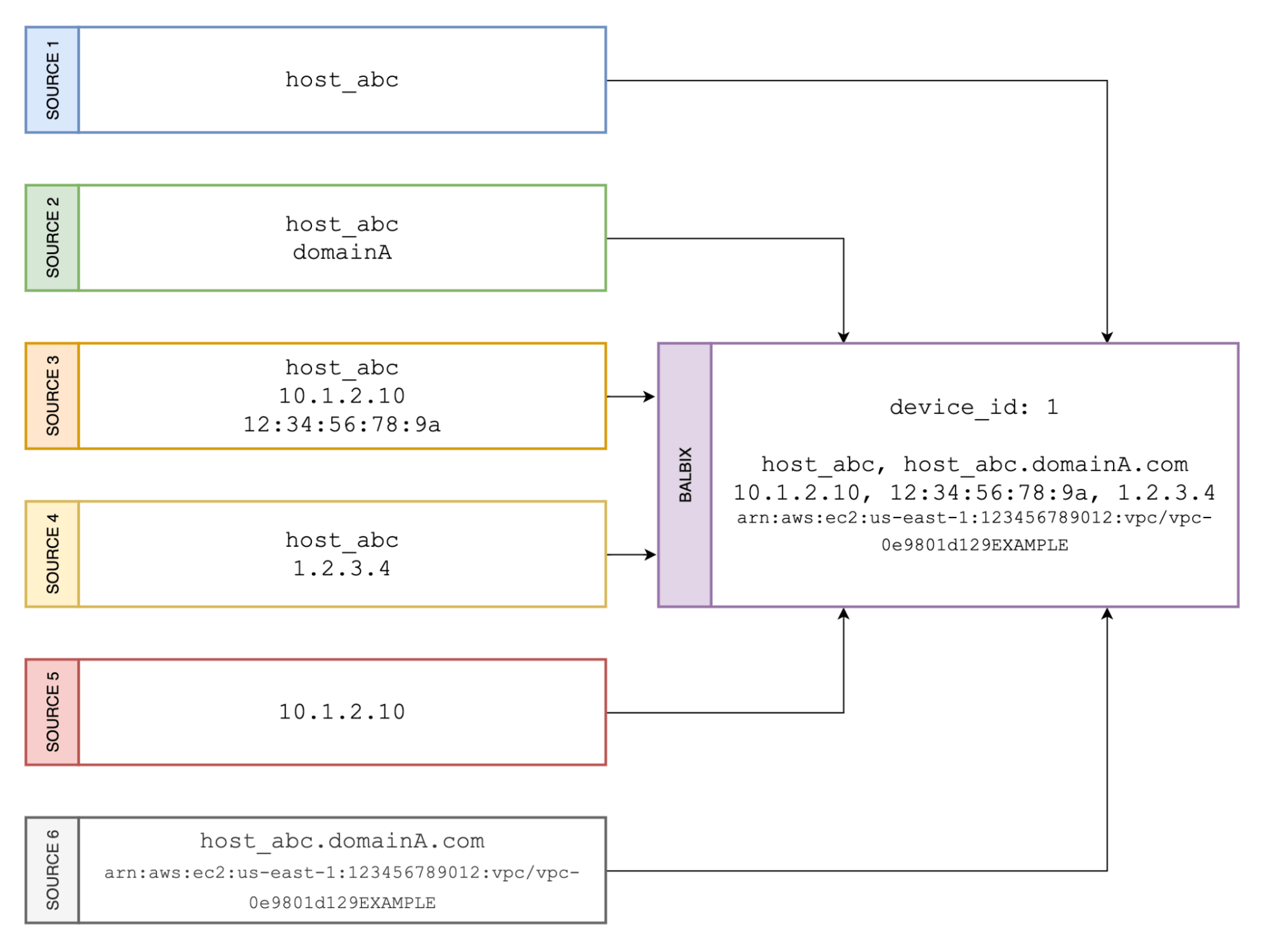
Once the assets are identified, the next step is identifying the components associated with assets. Asset components are critical to understanding the importance of assets, as well as to understanding the risk exposure.
For example:
Balbix correlates information reported by various data sources, such as vendor, OS version, and patch status. However, each source suffers from at least one of the data fidelity issues mentioned in the previous section. To solve this, the information is normalized and examined, resulting in a data set that is free from these issues.
Balbix AI uses state-of-the-art large language models (LLMs) tailored for this use case and best-in-class inference service hardware. These services are optimized using NVIDIA’s TRT-LLM and Triton inference servers and provide an order-of-magnitude improvement in throughput. This approach of analyzing data from multiple sources in conjunction leads to a more complete state of an asset component than can be established from any source independently, as is illustrated in the example below.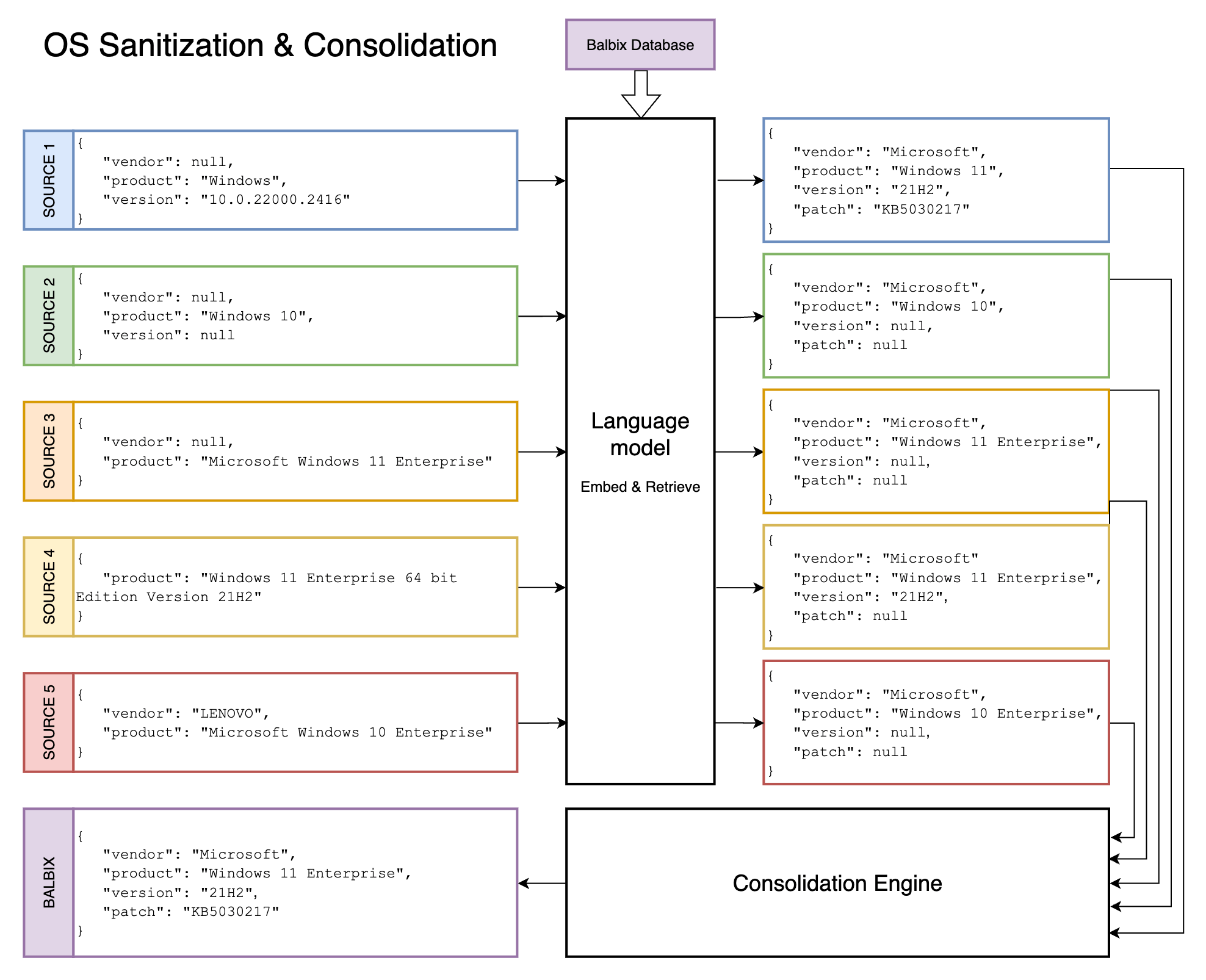
It is important to identify the category of an asset to understand potential attack vectors and plan an effective infosec strategy. For instance, web servers are highly susceptible to known vulnerabilities to DDoS attacks.
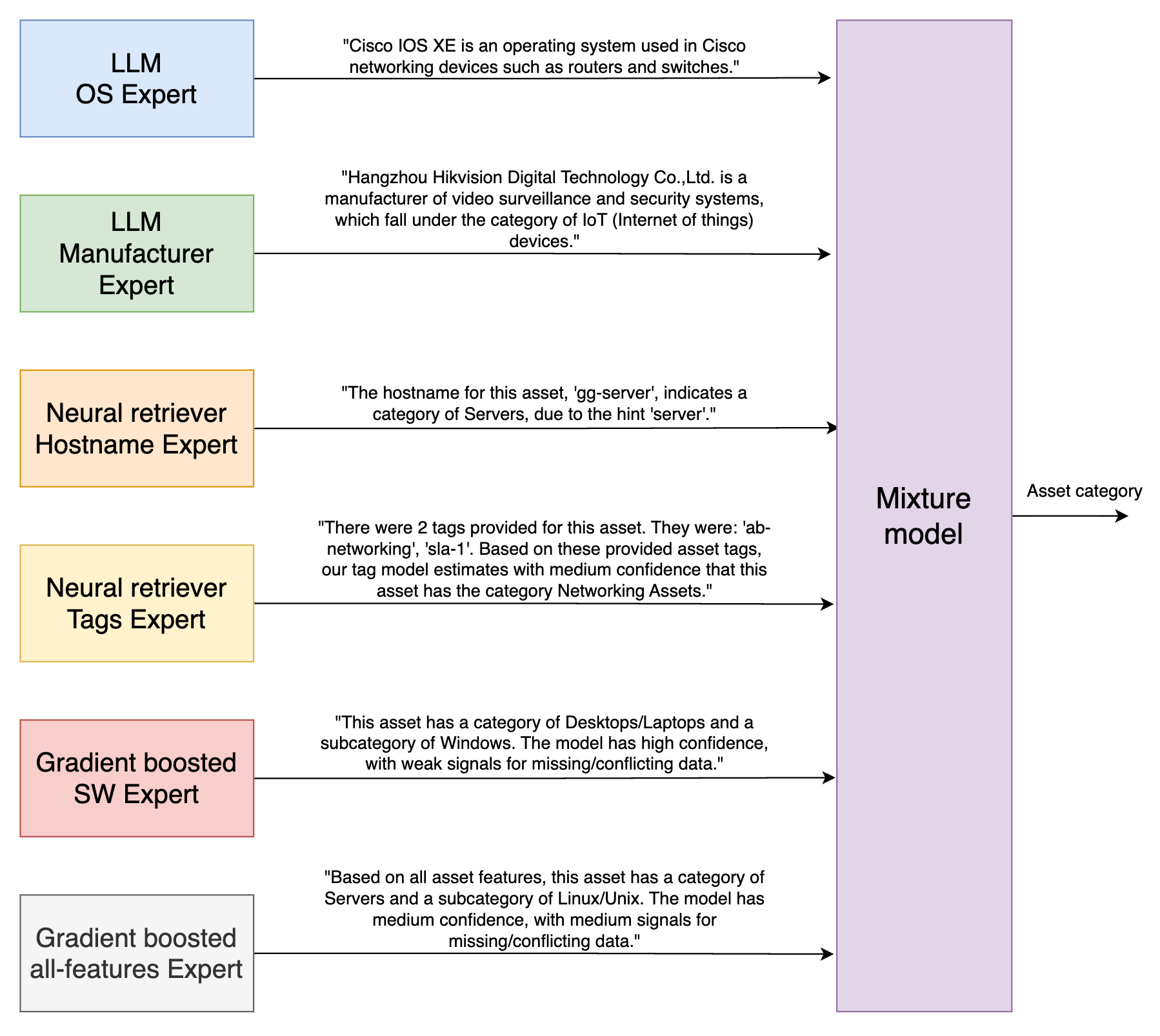
Once you understand your assets, Balbix AI provides additional models to infer attributes such as asset category, type, and subtype. These dedicated models reason based on specific attributes, e.g., when Cisco IOS OS is observed, the OS model infers the device is a networking device and either a router or a switch based on the system model observed, or when the system manufacturer is Hikvision, the model deduces that the device is an IoT security camera.
These models individually reason based on specific attributes and vote for the device category, type, and subtypes based on the confidence gained from observations. These individual models reinforce their deductions, leading to a concrete conclusion on these attributes. This mixture-of-experts approach has dual advantages:
Typically, automated systems cannot handle low-quality inputs, resulting in garbage-in and garbage-out scenarios. In the case of identifying asset inventory, these cases can create a large degree of inefficiency in operationalization. With these advanced inferences, we can distill the portion of the network where we have assets of high confidence as well as assets that are:
The illustration below shows how this system can reason various attributes in several situations. It also depicts how expert outputs are processed in conjunction to conclude the asset category. This approach is advantageous when multiple weak signals can be combined, e.g., when only port 161 is observed, the category is indicative of a networking asset but inconclusive; when a tag “Restricted Storage” is seen, there is some evidence built towards the asset being a storage device; and finally, when “Data OnTap” is seen as the OS, the combined inference is that the asset is a storage device with high confidence.
Geolocation and exposure of an asset are critical for operational use cases such as compliance reporting, materiality determination, ticket resolution, and patching. Assets may either be managed based on organizational units that may be geographically distributed, or even when they are not, geopolitical events might warrant tactical operations for enterprises.
For example, the Russia-Ukraine war required real-time management of assets based on their geographical locations. In this case, although the asset attributes are standard geolocations, the observations are specific to each enterprise, either in terms of site names or physical addresses of assets. This requires both:
The association with a location is achieved through inferences on graphs denoting network topologies observed, which entails leveraging data from multiple sources with varying fidelities across time and network hierarchies – for example, a CMDB may provide accurate information regarding the location of a laptop at the time of procurement, but an endpoint agent might report a more accurate IP address at a later point in time which can be used to infer its most recent location.
We use NLP approaches and retrieval mechanisms that leverage parallelizable inferences on GPUs to sanitize the location and pin it to geolocation. We also employ these technologies to understand the relative location on the network as an asset by analyzing tags indicative of assets being internet-facing, in the DMZ, as part of the segmented subnetwork, or in an air-gapped subnetwork.
As previously discussed, Balbix AI can process petabytes of data to provide comprehensive visibility into an enterprise’s attack surface. Attack surface management is just one aspect of risk management. In subsequent blog posts, we will demonstrate how Balbix measures other components to equip an enterprise for better cyber resilience.
If you want to learn more about how Balbix uses AI for risk management, join our upcoming demo day.