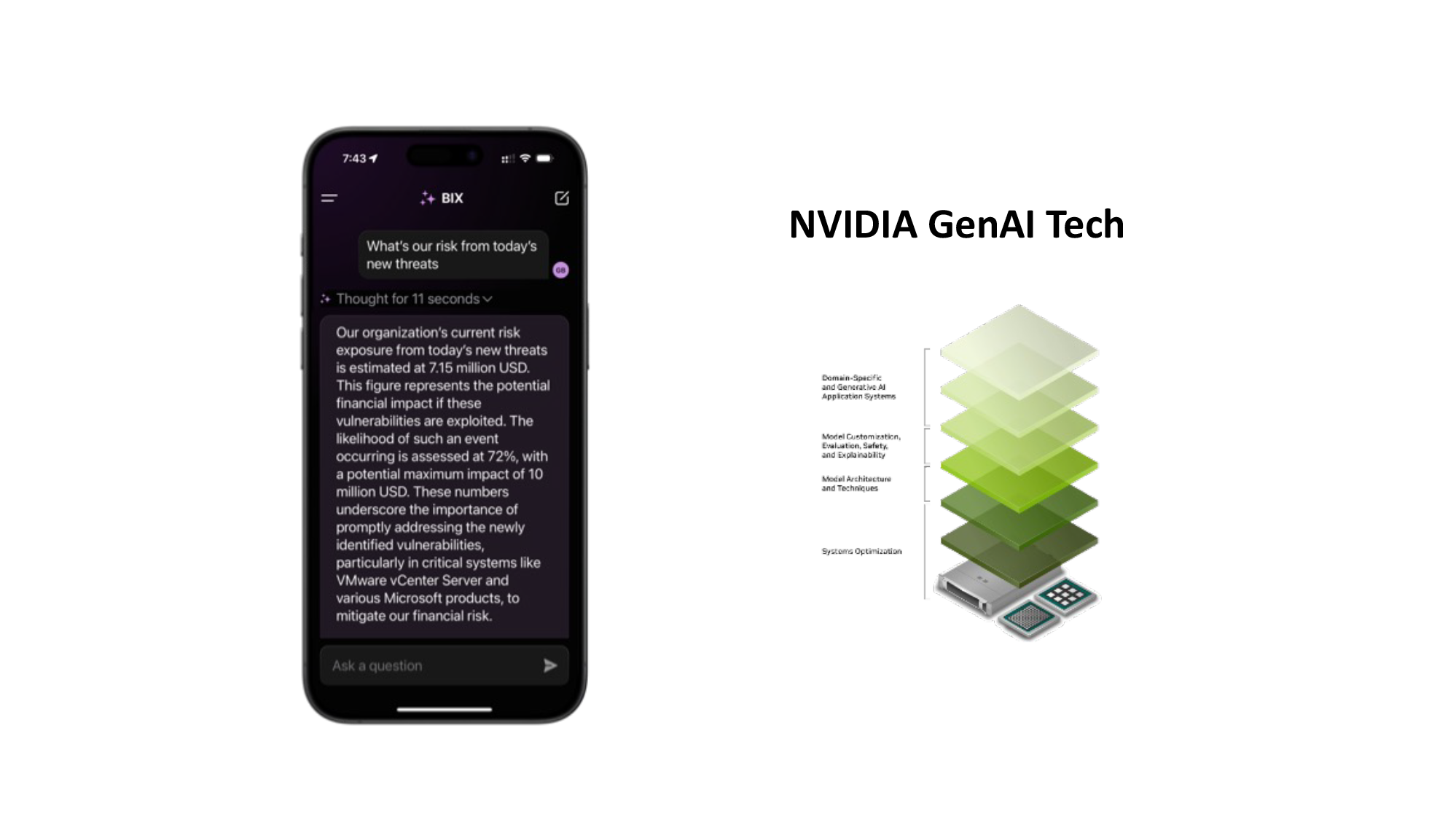
November 7, 2024
The Story of BIX, a Specialized AI Agent for Cybersecurity, Built with NVIDIA AI

October 7, 2024
A CISO Blueprint for an Effective Board Narrative
Stay up to date with us
Get insights on cyber risk management, vulnerability prioritization and board reports

October 4, 2024
Why is Asset Deduplication A Hard Problem?
October 1, 2024
Balbix D3: A New Dawn for Faster Burndown of Exposures and Vulnerabilities
September 25, 2024
CISOs: The one question your board will NEVER ask you

August 27, 2024
Seeing the Unseen: How Generative AI Elevates Situational Awareness in Cybersecurity
August 13, 2024
4th generation vulnerability prioritization: what is the buzz all about?
August 6, 2024
Meet BIX: Your New AI Ally in Cyber Risk and Exposure Management
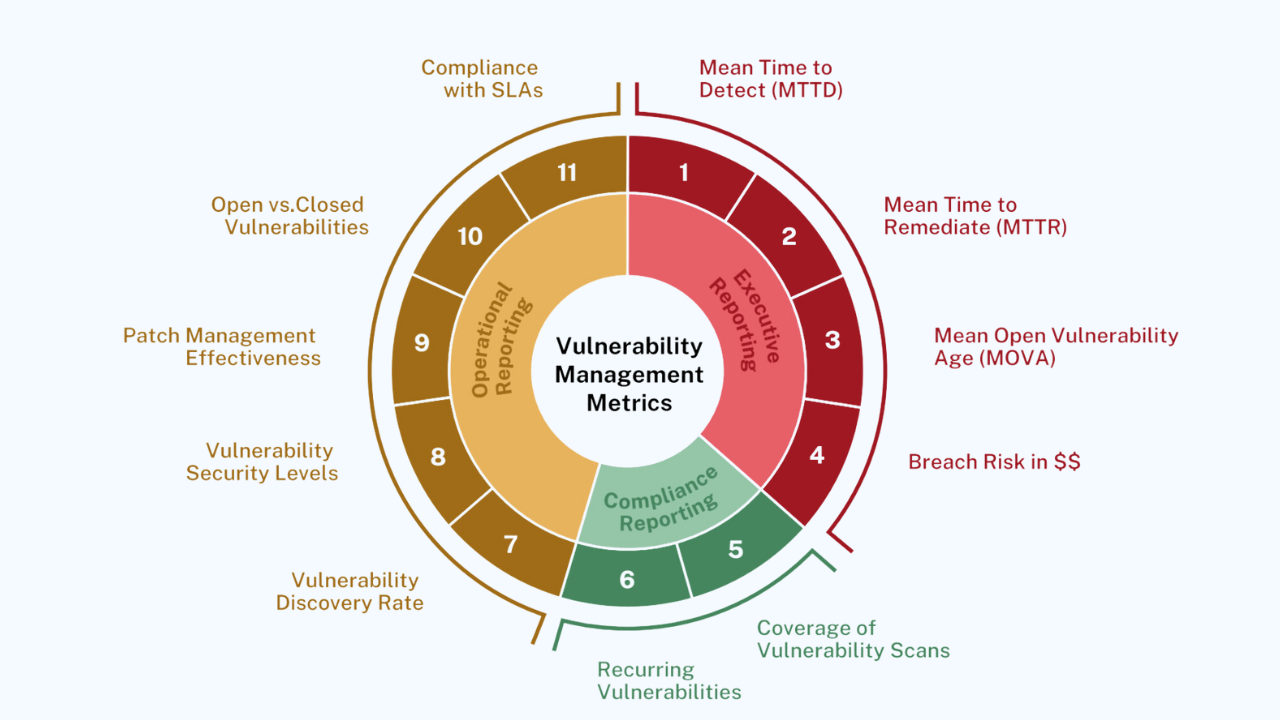
May 29, 2024
The Top 11 Metrics for Successful Vulnerability Management
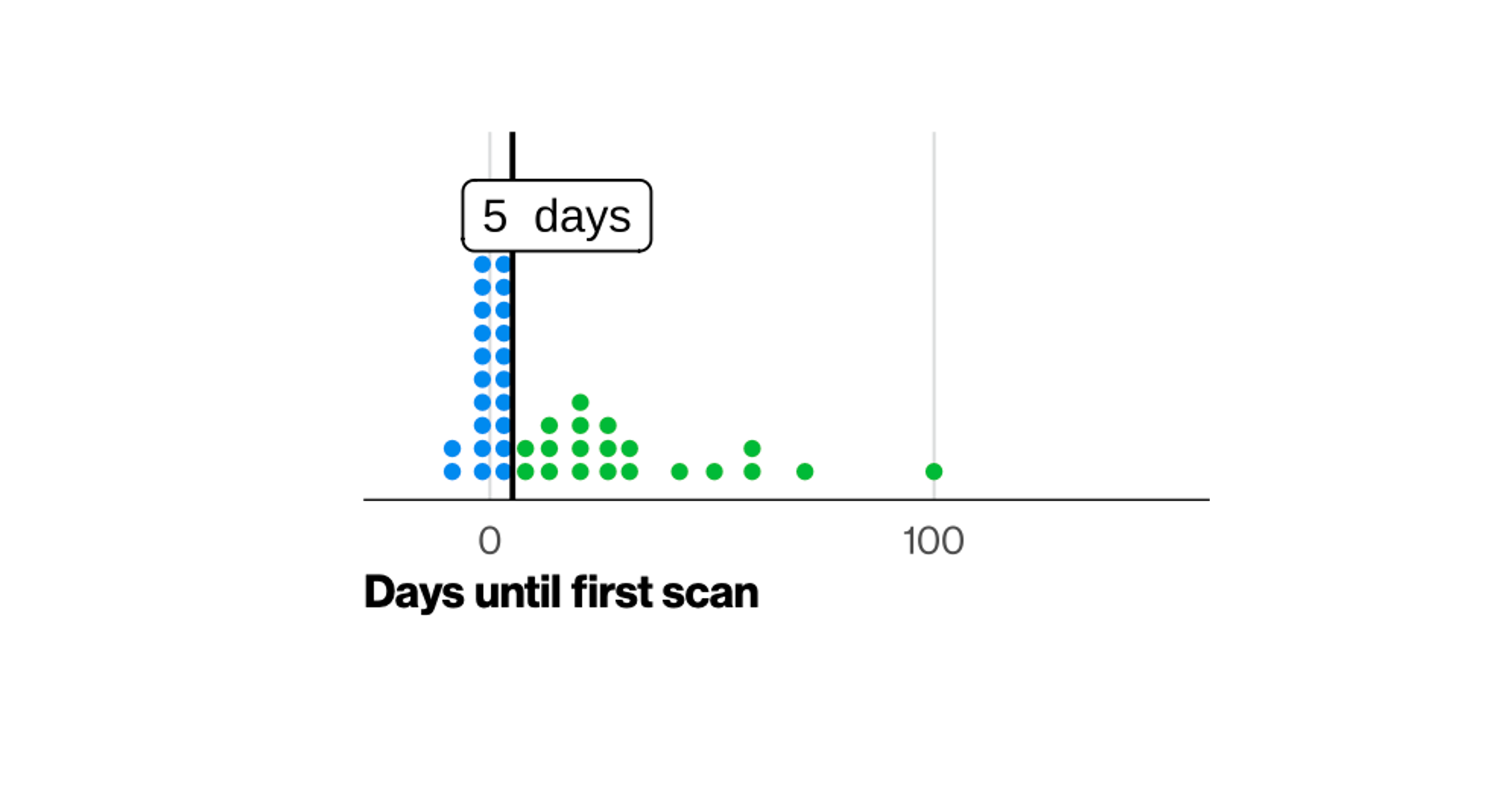
May 14, 2024