
July 17, 2024
The 2024 State of Enterprise Cyber Risk in the Age of AI report, independently conducted by Ponemon Institute and analyzed and published by Balbix, is fueled by over 20,000 answers from hundreds of CIOs, CISOs, CSOs, and leaders from information security.
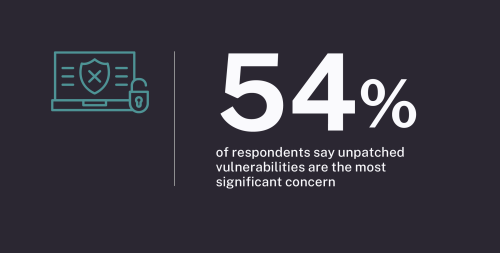
According to the report, enterprise organizations need help keeping up with the growing needs and requirements of cyber risk strategies. Unpatched vulnerabilities were identified as one of the top concerns. Additionally, many organizations plan their cyber strategies more than 12 months in advance. In the age of AI, this results in outdated choices on tooling, processes, and procedures, resulting in weakened security postures against emerging AI-powered threats.
This report reveals the pressing issues that keep cybersecurity professionals awake at night in a new, fast-changing world of cybersecurity where AI plays a dual role in defending and targeting organizations. It explores the growing divide between cybersecurity operators and executive teams regarding the approach, prioritization, and investment in cyber risk management, offering potential solutions to bridge this gap.
However, nearly half of these organizations are concerned about vulnerabilities arising from AI-generated code despite already integrating AI tools into their operations and tech stacks.
While AI-generated vulnerabilities seem intimidating, organizations should fall back to basics. The speed of coding and development may cause the number of vulnerabilities to rise. Rather than focus on how the vulnerabilities are generated, organizations should have a system to identify and remediate them. This includes prioritizing vulnerabilities based on organizational context and integration with tools to patch and remediate them.

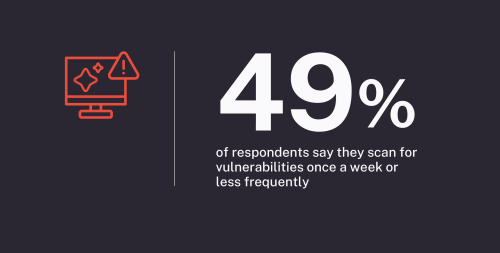
Alongside misconfigurations and end-of-life (EOL) software, organizations are struggling to manage an increasing number of vulnerabilities. This challenge is compounded by inadequate vulnerability scanning practices, with half of the organizations scanning for CVEs only once a week or longer. Industry reports indicate that attackers can exploit vulnerabilities within days, challenging defenders to always play catch-up.
Organizations need to invest in risk-based frameworks and approaches to tackle CVEs, misconfigurations, and EOL software. CVE scanners can provide visibility, but they are siloed in nature. Instead, enterprises should consolidate and unify all exposures and vulnerabilities into a single tool and ensure they prioritize based on impact rather than individual tool scoring.
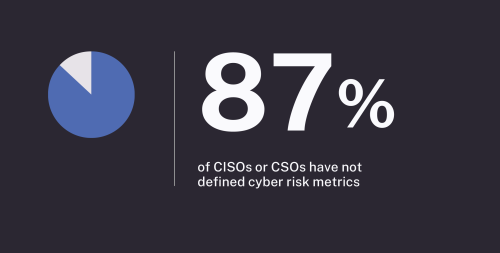
Security teams grasp the potential business impact of an exploited vulnerability but need help to convey this effectively to leadership. Astonishingly, 87% of CISOs and CSOs lack overall responsibility for defining metrics in their cyber risk management strategy. Challenges include the time-consuming nature of report preparation and infrequent cybersecurity briefings of executives.
Consequently, more than half of the executives who do receive reports find them unengaging.However, there is hope in bridging this communication gap. Translating cyber risk into monetary terms can help executives understand the potential business impact of cyber risks. This approach can make cybersecurity reporting more relevant and impactful for leadership.

There’s a lot more to dive into in the full report. You can download the PDF here.
Lastly, hear directly from our experts in an upcoming webinar walking through the full report findings and offering best practices for improving your cyber risk. Sign up for the webinar with Ponemon Institute on September 11, 2024.