 Most information security professionals are familiar with the Center for Internet Security, the non-profit most famous for publishing the CIS Controls and CIS Benchmarks. The Top 20 CIS Controls are widely used by organizations in the public and private sectors to help reduce the risk of data breach. Of the 20 controls, the first 6 are considered “basic” controls, or the essentials of cyber defense, which should be implemented by every organization.
Most information security professionals are familiar with the Center for Internet Security, the non-profit most famous for publishing the CIS Controls and CIS Benchmarks. The Top 20 CIS Controls are widely used by organizations in the public and private sectors to help reduce the risk of data breach. Of the 20 controls, the first 6 are considered “basic” controls, or the essentials of cyber defense, which should be implemented by every organization.
These controls are the foundation of our information security house. If they are shaky, the whole house is at risk, regardless of how well we lock the doors and windows.
Controls #1 and #2 sound strikingly similar. Control #1 specifies “Inventory and Control of Hardware Assets.” Control #2 specifies “Inventory and Control of Software Assets.”
In each control, the organization must “actively manage (inventory, track, and correct) all software [hardware] on the network so that only authorized software [devices] are installed and can execute [given access].”
The most basic, fundamental starting point for your cybersecurity program is an accurate, up-to-date inventory of the hardware and software assets connected to your network.
Despite the number of organizations adopting the CIS Controls, a strikingly large percentage of them are unable to satisfy the requirements of these first two basic controls. After periodic polling at events and other encounters over the last few months, responses I’ve heard from CISOs when asked whether they have a handle on even the rough number of assets on their networks include:
- “One can only dream”
- “That’s a very good question”
- “Somewhere between 25k and 50k” — a very large range, depending on the size of the organization
- “Does anybody really have a handle on that?”
So what if you never really get a handle on these two controls? Can you still be secure? Unfortunately, you can’t secure what you can’t see.
With the dynamic nature of today’s organizations, seeing everything is simultaneously more difficult, and more important than ever before.
The FTC’s complaint against Equifax offers a view of the real consequences of not properly implementing the first two controls:
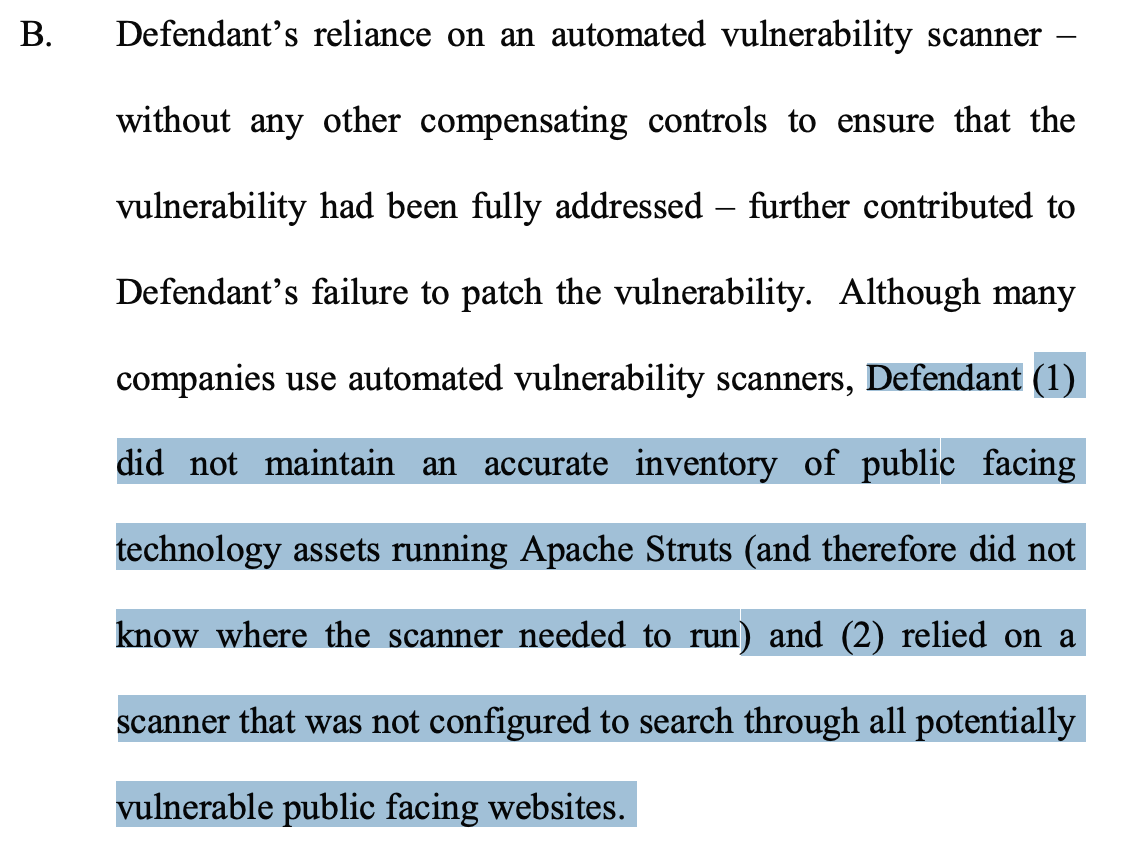
Here are four true statements about Asset Inventory:
- Inventory isn’t sexy.
- Inventory is difficult.
- Inventory needs every group to participate.
- Inventory is absolutely critical to building cyber resilience and a successful information security program
Fortunately, you no longer need to rely on inaccurate Configuration Management Databases (CMDB) or even worse, manual spreadsheets. New tools are on the market that can continuously build and update inventory, automatically categorize assets, provide measures of business criticality, and more.
So, before you move on and forget about this post, commit to driving an initiative to get a better handle on hardware and software inventory. If you want to increase the odds that you’ll actually stick to the commitment, write it down. If you want to increase the odds even further, call Balbix and take a look at our Automatic Asset Inventory.
