How should you report on your organization’s cybersecurity posture to your board of directors and C-suite colleagues?
As you know very well, your board members’ and senior executives view of cybersecurity is quite different from how security and IT team members think. It can be quite frustrating to try to explain advanced malware or technical controls to these folks, most of who are not savvy about the technical details of cybersecurity. Many C-Suite and boardroom discussions (and decisions) on cybersecurity are based on gut feelings and incomplete data.
Your board members and non- technical senior executives think about cyber-risk as yet another business risk item to be understood and managed. They have three main questions about cybersecurity and breach risk:
- Where is the organization on the cyber-risk spectrum?
- Where should the organization be?
- How can the organization get to where it should be?
Unfortunately, due to the massive size of the enterprise attack surface and the practically unlimited permutations and combinations by which the adversary can carry out a cyberattack, you know how difficult it is to analyze your overall cybersecurity posture and calculate your organization’s breach risk.
You are not alone. In a recent survey conducted by the Ponemon institute, only 9% of security teams felt that they were highly effective in communicating cybersecurity risks to their board of directors and c-suite colleagues.
How can we do better?
Elements of good cybersecurity reporting
How exactly should you quantify cybersecurity posture for your board of directors and C-suite colleagues? Your overall objective is to help your board do their oversight job better and get funding for your security projects.
Here are some key ideas to keep in mind.
- You need to up level the conversation from cybersecurity to cyber-risk, but stay true to the on-network cybersecurity posture.
- It is helpful to identify key areas of business risk and how your cybersecurity program is aligned to this risk.
- At the board-level it is all about benchmarks, so you must have a mechanism to compare your cybersecurity posture against peer organizations. Your board will look to you to recommend the appropriate level of cybersecurity posture your organization should aim for.
- You must have internal benchmarking data in your back pocket– what is working well, and what is not. And which groups have good cybersecurity posture vs ones that don’t.
- Your report must be backed by a plan– on how you would change the organization’s cybersecurity posture to the recommended level. You will need to explain what you need from the board to execute your plan.
- Last but not least, you will need to execute your plan, and show cyber risk reduction outcomes and other trends in a quarter or two, and forever thereafter.
Your reporting framework must be systematic – you do not want to be doing ad-hoc analysis and building slides by hand before each board meeting.
Let’s dig into some details.
Aligning with Business Risk
Board members are primarily concerned with cybersecurity as a set of risk items. For example, if your organization cares about risk of loss of intellectual property from cyber-attacks, you want to define this as a key risk item to track and report.
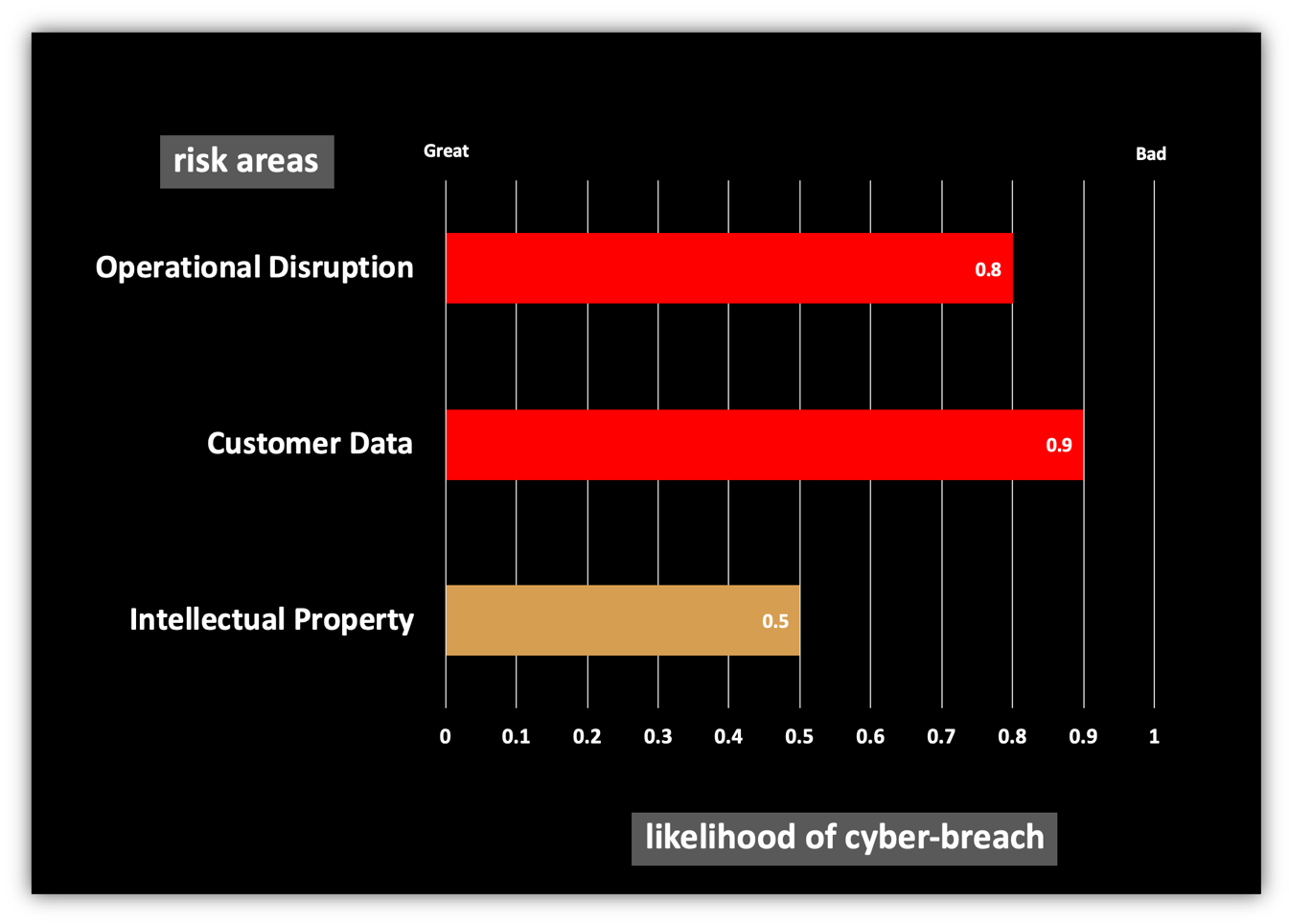
You must also map this risk item to the actual on- network attributes and that drive it, and put in place a system or process that continuously observes and analyzes the relevant parts of your cybersecurity posture. Note that you need to able to report on business-level risk metrics, without having to explain the technical details of your cybersecurity program. But the mapping from business risk to technical details should be in your back pocket.
External and Internal Benchmarking
Your board members and executives want to know the level of acceptable risk that is appropriate for your organization. Comparison with peer entities is a common method which senior leaders use to grade performance.
You need to be able to benchmark your security posture against similar organizations, and use this information to help the board understand your recommendations for cyber-risk goals for your enterprise.
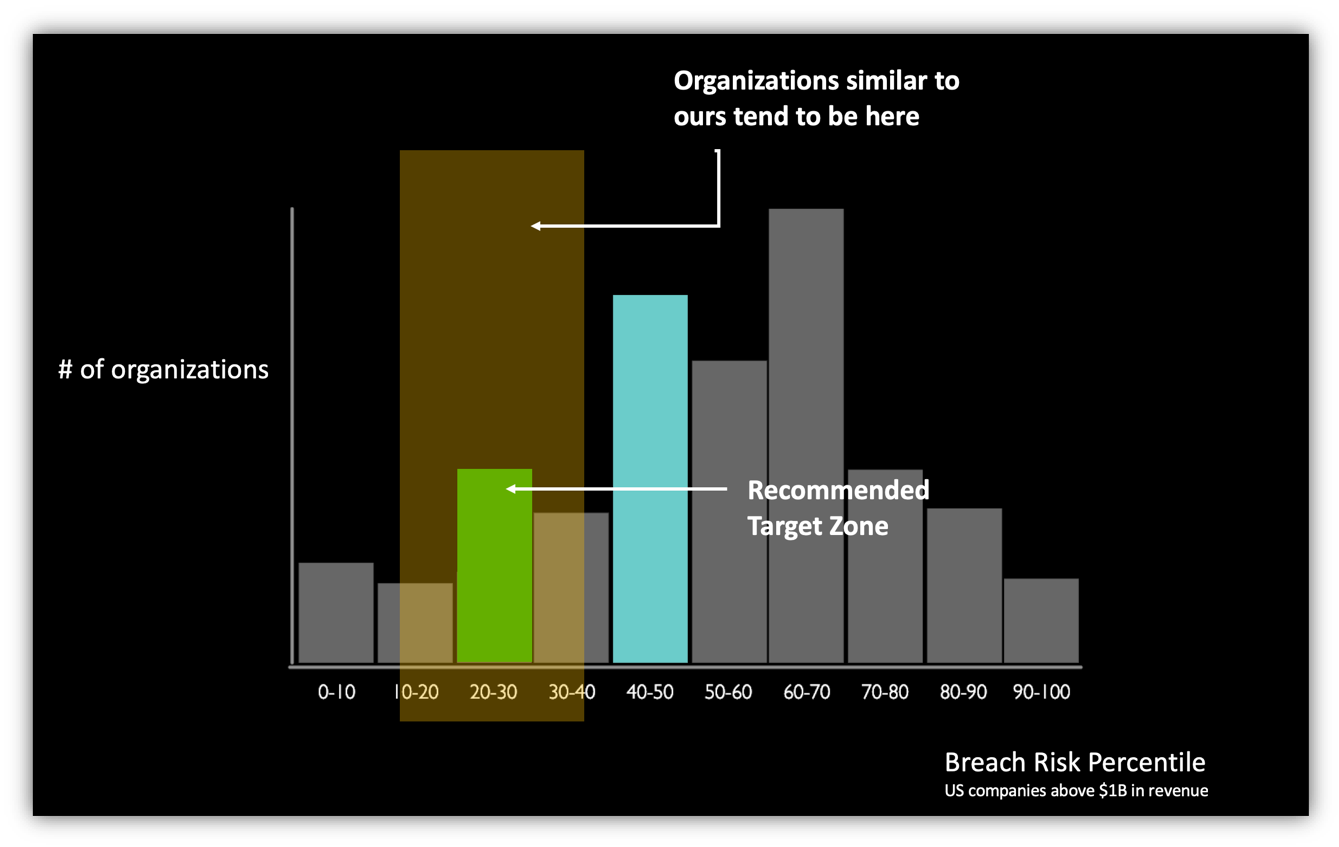
For example, you can show the percentile of breach risk that your organization falls in, and where organizations similar to yours are placed. If your enterprise has a good cybersecurity posture, you are “done”, and it is just a matter of maintaining your current level of cybersecurity preparedness. More likely though, you will have work to do and this type of benchmarking can be useful in helping you justify to your board and senior colleagues the need to do this work.
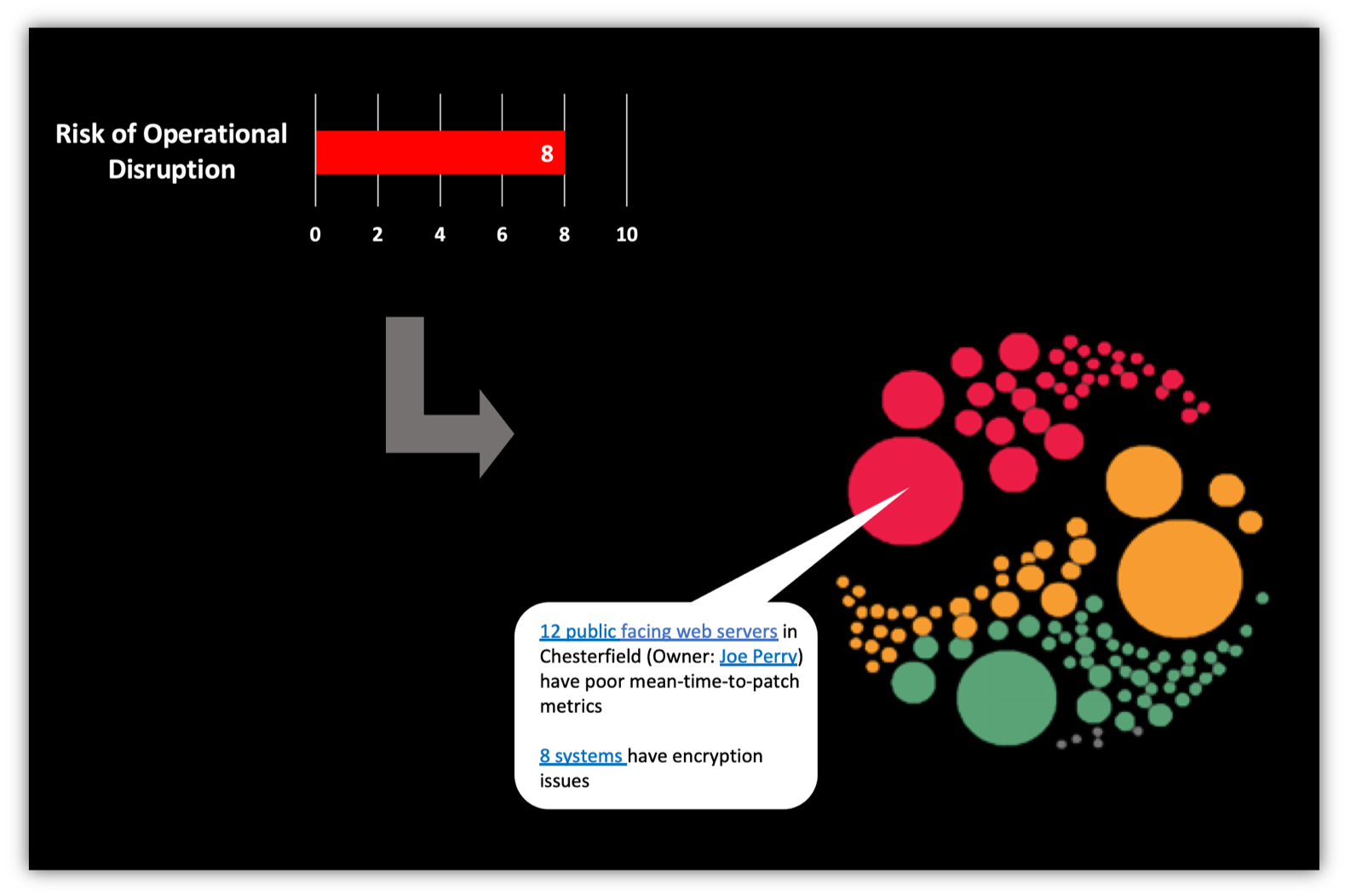
Similarly, with internal benchmarking information, you are able to show to your board and senior executives how risk is distributed in your organization, which teams/areas are driving the greatest risk. You need to be able to explain at a high level the types of actions necessary to remediate these risk hot-spots. Your objective is to bridge the gap between perceived risk in the boardroom and the actual on-network conditions.
The Plan
Your board and C-Suite colleagues expect you to have a well thought out execution plan to transform your organization’s cybersecurity posture to the recommended risk level. Showing up to a board meeting to raise an issue but without a plan is career-limiting.
Obviously this requires a lot of homework and thought. Depending on your organization’s level of security maturity, you may need to put in a system to give you accurate and comprehensive security posture visibility. Then you may have to implement or enhance your organization’s identity framework, vulnerability management practices, incidence response and cyber-resilience.
As before, your plan will need to be up-leveled into a small number of steps or initiatives, each with a time-frame, required resources and a dollar cost. Your board will expect that you have considered alternative plans and have good reasons to recommend the specific plan that you put forward.
Your board will expect you to be able to drive and execute your plan. However, as we all know, other departments may not necessarily co-operate with the plan you want to execute with the right level of urgency. You need to be able to highlight all the responsible constituents of the cybersecurity posture transformation plan, and get the board’s and senior managements clear buy-in.
Trends and Reporting
Of course, the next quarterly cybersecurity review with the board comes along soon enough, and you need to produce slides which show the risk reduction outcomes your team has been able to achieve in the last 90 days. You need trends over 90 days, 6 months, and year-over-year.
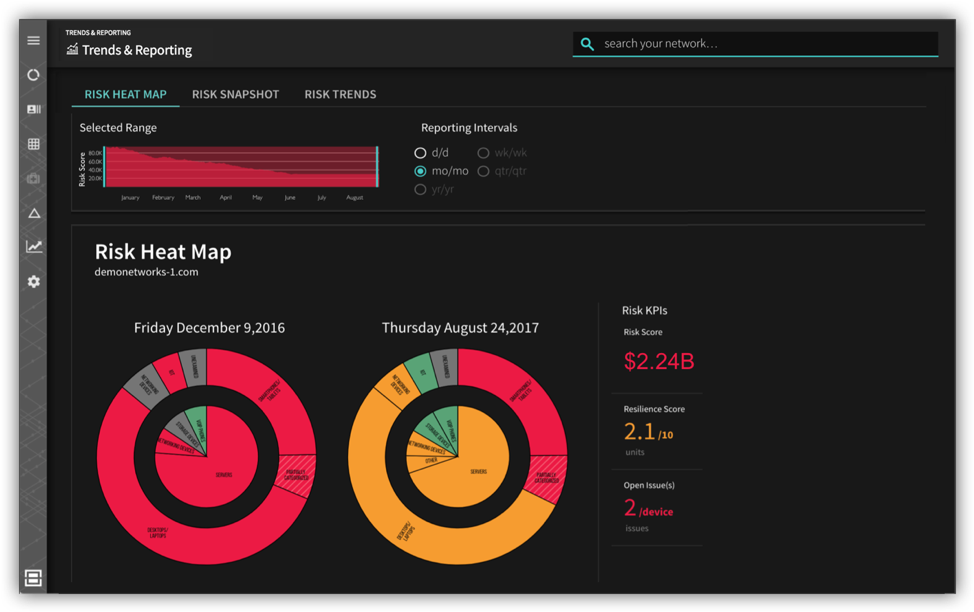
Today, you have to ask your subordinates for various reports, and then do quite a few hours of painstaking work to interpret these reports and do slide-work. Fortunately, there are better ways of doing this.
At Balbix we have been doing a lot of work with our customer CIOs and CISOs on this topic. You can find more information here. Please contact us to see how we might be able to help you develop a world-class cyber risk reporting framework for your board of directors and c-suite.
