

October 8, 2024
America’s water systems are becoming targets for cyberattacks. Cybercriminals and nation-state actors exploit known vulnerabilities, threatening the safety and security of a critical public resource. Recent attacks have highlighted the urgency for water utilities to bolster their capabilities, especially given their limited resources.
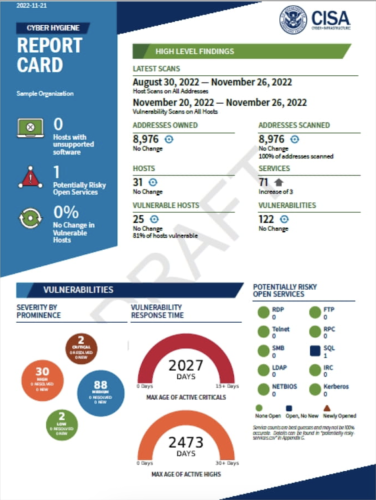
In the past year, around 70% of water utilities inspected by federal agencies violated cybersecurity standards designed to prevent intrusions. Small communities, in particular, have become easy targets for cyberattacks, with threat actors linked to Russia and Iran focusing their efforts on vulnerable systems.
Water utilities rely heavily on sensors and computers to operate treatment plants, control distribution networks, and meet water quality standards. While this reliance improves operational efficiency, it also opens the door to potential cyberattacks. Compromised systems could lead to interruptions in water treatment processes, damage to essential equipment like pumps and valves, or even dangerous changes to water chemistry that could threaten public health.
America’s water utilities face a unique challenge. The sector is highly fragmented, with approximately 50,000 utilities, many serving small towns with limited staff and budgets. These constraints make it difficult to implement comprehensive cybersecurity programs.
Without sufficient funding or technical expertise, these utilities often struggle to protect their systems from evolving threats. For many, simply maintaining clean water supplies and complying with the latest regulations is a full-time challenge. As a result, cybersecurity often falls by the wayside, leaving critical systems exposed to attack.
Key Vulnerabilities:
Cyberattacks on critical infrastructure are not new but are becoming more frequent and sophisticated. The infamous May 2021 ransomware attack on the Colonial Pipeline, which caused widespread fuel shortages across the East Coast, exemplifies how attackers can wreak havoc on infrastructure.
Similarly, in February 2021, a hacker attempted to poison the water supply at a Florida treatment facility by raising the levels of sodium hydroxide to dangerous amounts. Fortunately, an employee acted quickly to neutralize the attack, but the incident served as a wake-up call to the risks facing water systems.
These incidents underscore that cyberattacks can have real-world consequences beyond just financial damage, i.e., threatening public health and safety.
The fragmented nature of the water sector, combined with resource constraints, makes securing water utilities particularly difficult. Most water systems operate with limited IT staff and low budgets, and cybersecurity initiatives often have to compete with more pressing needs like maintaining water quality and upgrading aging infrastructure.
Challenges Include:
Preparedness is the key to safeguarding public health and maintaining the integrity of our water systems in the face of rising cyber threats. While the challenges are significant, there are several practical steps water utilities can take to strengthen their cybersecurity posture.
Here are four key actions that can lead to meaningful improvements:
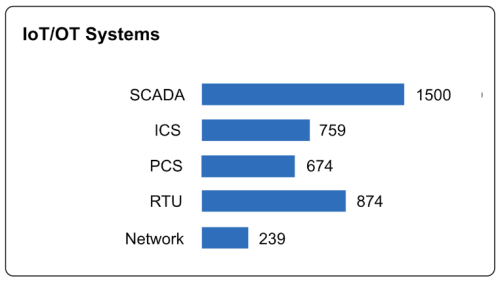
Water utilities cannot afford to take a reactive approach to cybersecurity. By taking advantage of free government resources, joining information-sharing communities like WaterISAC, and deploying advanced tools like Balbix, water systems can better protect their infrastructure from cyberattacks.