April 2, 2024
In the previous blog post, we described how Balbix leverages AI to provide a unified and comprehensive visibility into your attack surface. Establishing it requires deduplicating, normalizing, and correlating data from dozens of tools, which becomes a foundational requirement for cyber risk management.
In this blog, we will outline how Balbix prioritizes cyber risks such as vulnerabilities, misconfigurations, ransomware exposure, out-of-date software, control gaps, and more.
At Balbix, we define vulnerabilities as
While vulnerabilities cause risk of exposure, security controls prevent them. Appropriate risk management requires organizations to understand, document, and track all safeguards or countermeasures to protect against exposure. This includes:
To prioritize cyber risks, security teams need to: :
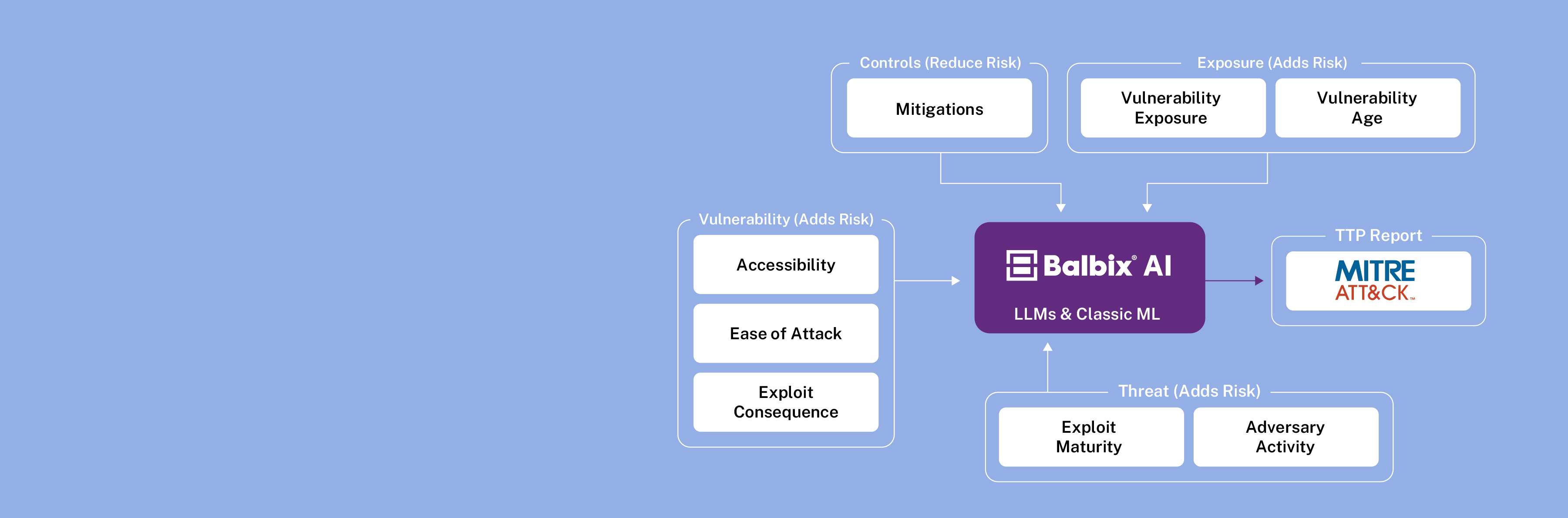
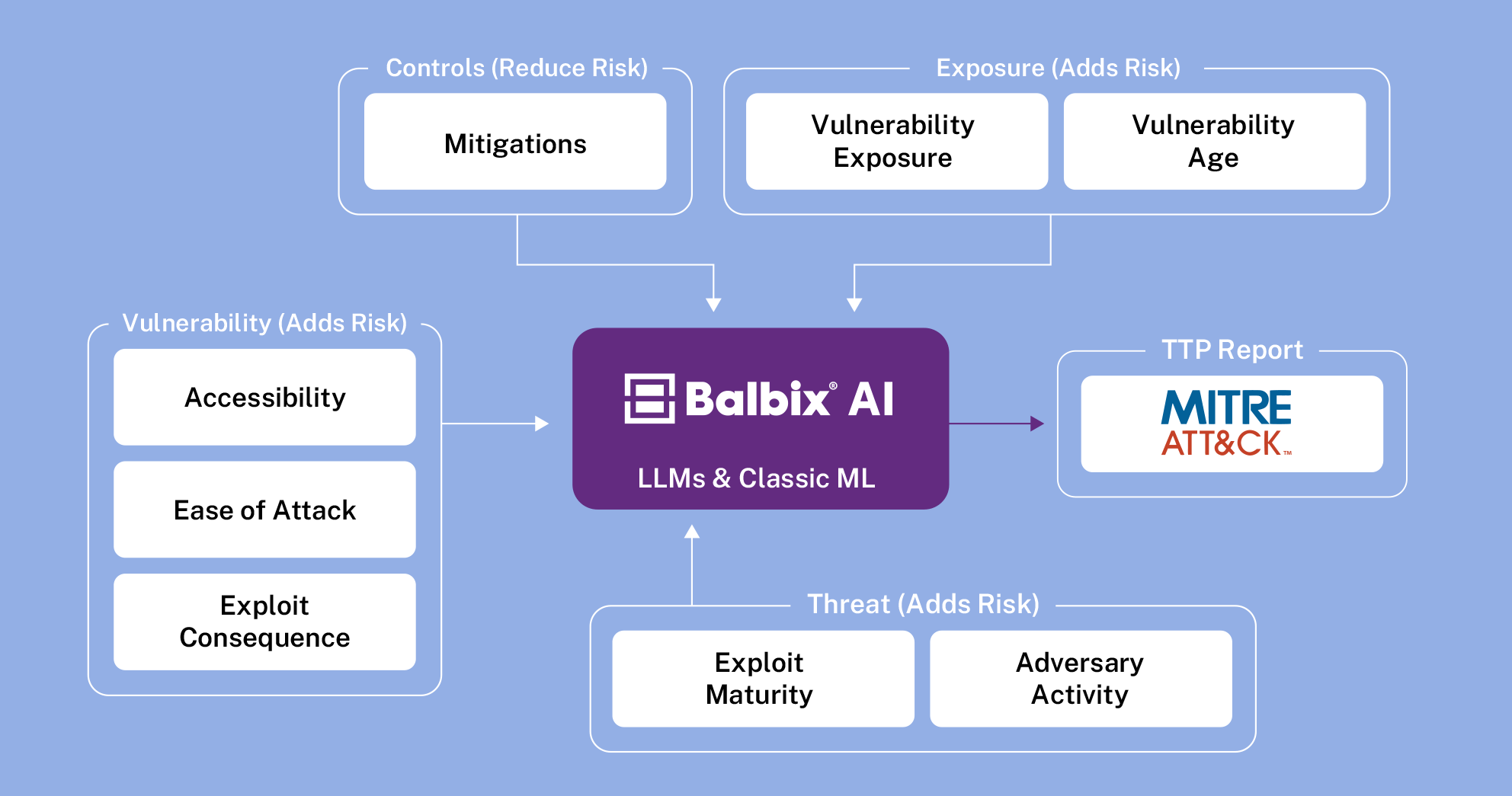
Let us review how all of this works together:
Starting with a comprehensive inventory of the attack surface, Balbix can infer vulnerabilities in the assets and all its components i.e. software, plugins, and ports, and understand how these assets and vulnerabilities are exposed. Balbix also brings in data from external sources to provide a contextualized view of vulnerabilities. This entails the ability to establish requirements for vulnerabilities to be exposed and to assess the degree to which these requirements are met at the granularity of each vulnerability instance or occurrence.
We bring together data from public data sources such as the National Vulnerability Database (NVD), and third-party subscriptions and use LLM-based approaches to analyze tens of thousands of vendor and product web pages and extract data on vulnerabilities on a continuous basis in an automated manner and at scale. This has allowed us to create a vast, high-fidelity database of this information that is put to use to infer vulnerability exposure. This makes the approach inspectable and traceable.
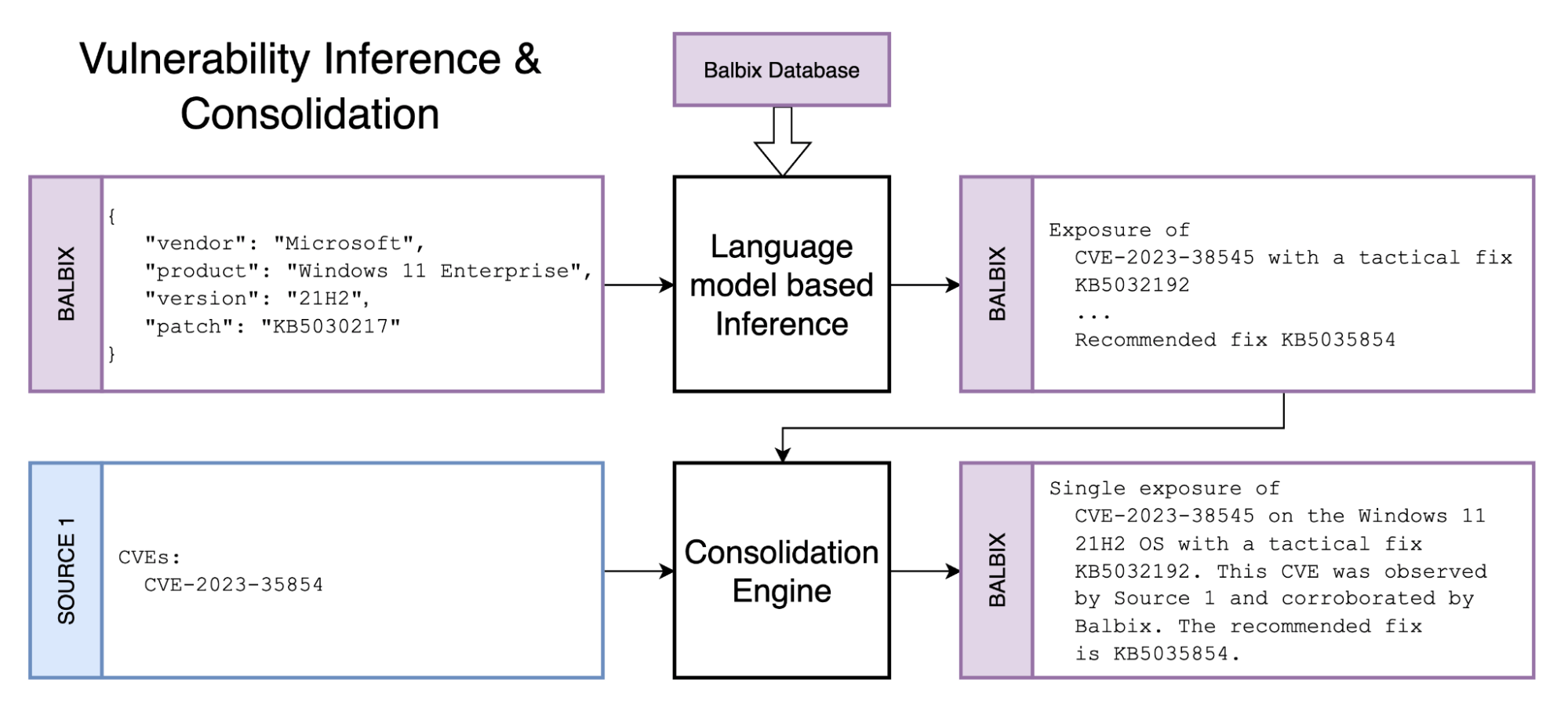
Assessing configuration-related vulnerabilities can be difficult as there is no widely adopted specification for them, unlike Common Weakness Enumeration (CWE), which is useful for assessing weaknesses in custom software.
To address this challenge, Balbix uses the MITRE ATT&CK framework, which provides a common language for adversarial capabilities. Using a single yardstick of risk to measure all vulnerabilities also enables a common prioritization process. Balbix AI uses large language models (LLMs) and Retrieval Automated Generation (RAG) based approaches to assess vulnerabilities based on adversary tactics, techniques, and procedures (TTPs). Additionally, Balbix uses language models to infer what weaknesses are exposed by a vulnerability and identifies attributes necessary to evaluate the likelihood of exploitability and the potential severity of compromise.
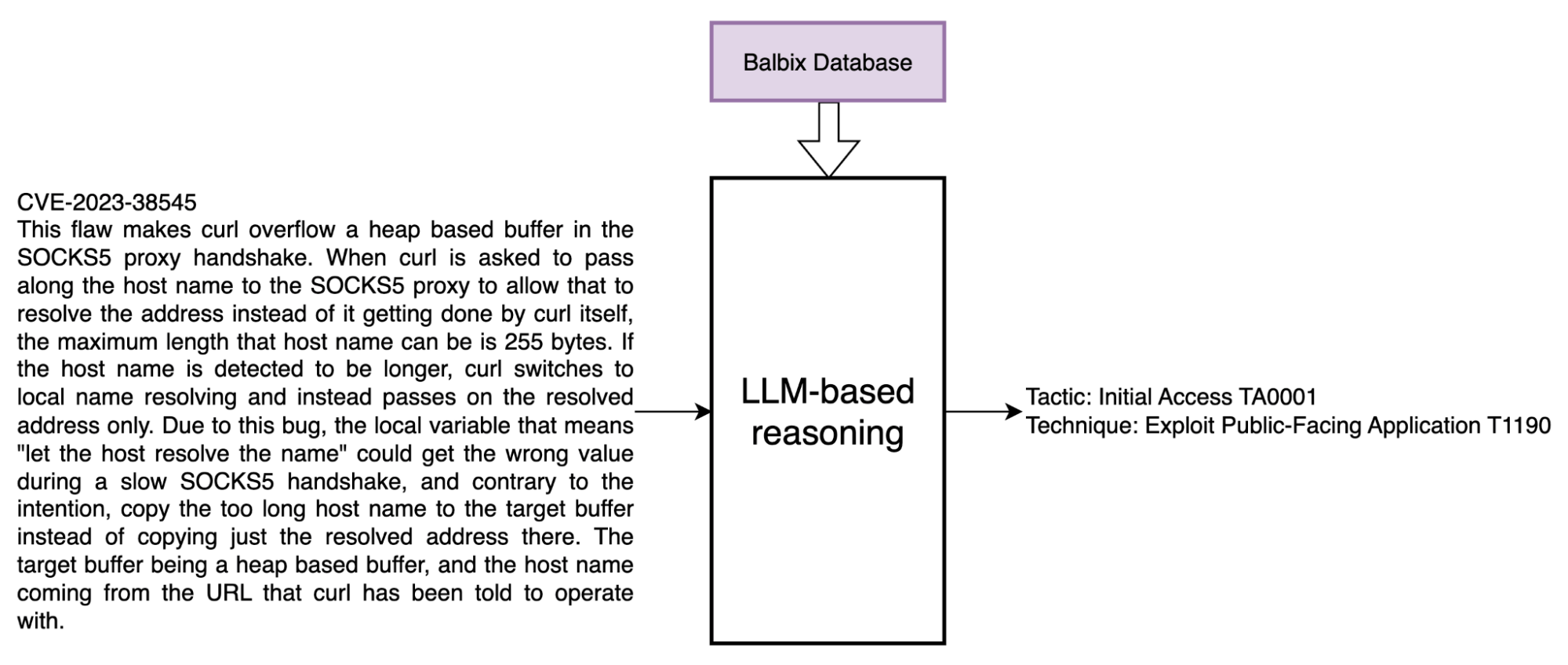
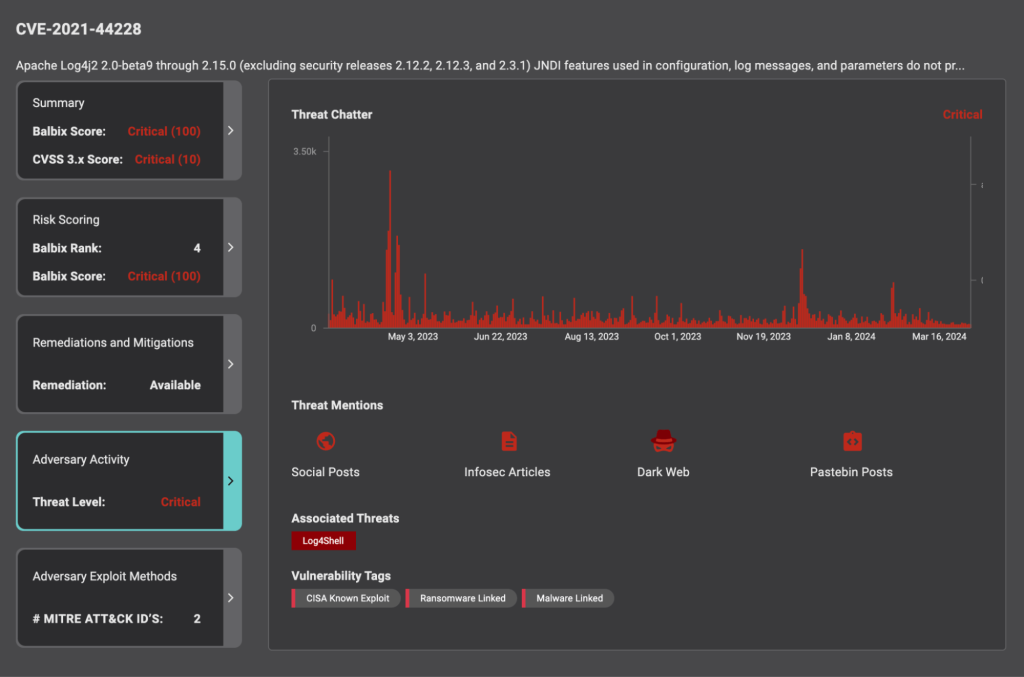
While the Common Vulnerability Scoring System (CVSS) is widely adopted, it rates all vulnerabilities assuming the worst-case threat. Since we know the vast majority of known vulnerabilities are never exploited, we need to enrich and assess vulnerabilities with threat intelligence – which provides context into any exploit kits available, adversarial activity, known exposures etc.
Balbix uses threat intelligence feeds, web scrapers, and other techniques for sourcing information on adversary activity, such as online chatter, discussions on the dark web and social media, and Pastebin posts. Balbix evaluates published exploit kits and known exploits using vulnerabilities. This ensures the likelihood of exploitation of vulnerabilities is much more accurate than with CVSS alone.
Additionally, while active exploitation of a vulnerability results in a large threat factor, the existence of any exploit kits, maturity of exploit kits, recency, and volume of the threat sightings also influence the likelihood of vulnerability exploitation.
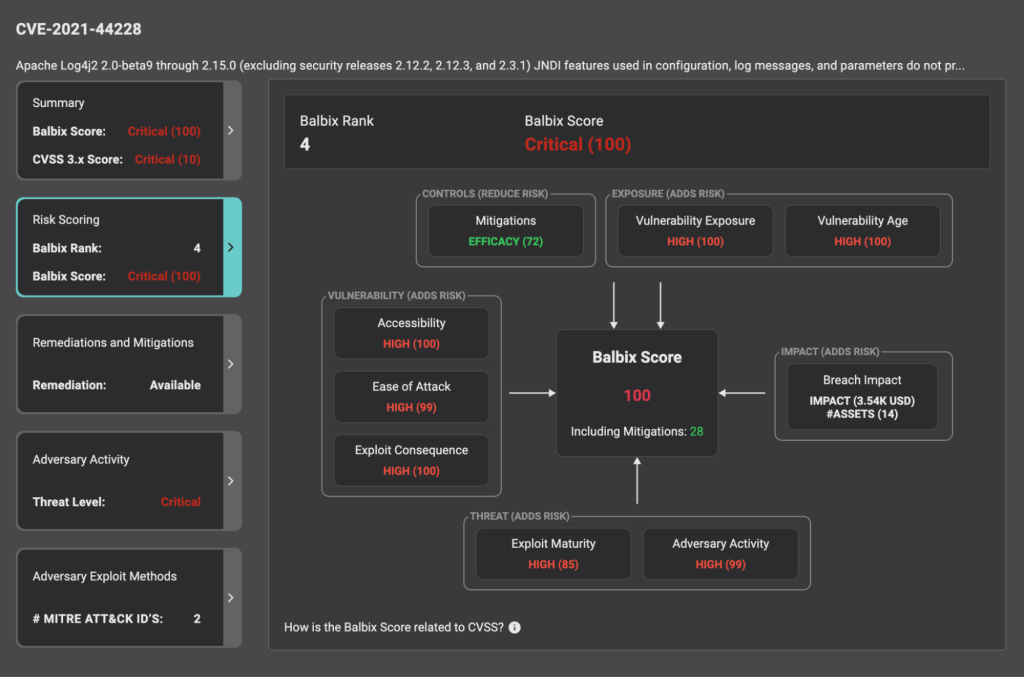
If vulnerabilities and threats alone were considered for prioritizing vulnerabilities, it would not be an accurate assessment state since security controls provide risk mitigation. But, factoring in controls into the prioritization of vulnerabilities is challenging due to the absence of a common denomination of risk exposure and risk reduction.
Balbix AI uses the MITRE ATT&CK framework to evaluate the effectiveness of controls in preventing specific adversarial TTPs. This evaluation includes both endpoint controls, assessed through MITRE Engenuity and third-party evaluations, as well as configuration controls, such as evaluating the efficacy of CIS safeguards. By factoring in the effectiveness of these controls, vulnerabilities can be realistically treated, allowing for a better understanding of risk exposure and the ability to prioritize vulnerabilities accordingly.
Furthermore, Balbix integrates with pen-testing and Breach and Attack Simulation (BAS) tools, to determine the likelihood of specific adversarial techniques used against evaluated assets.
With Balbix AI, organizations can manage risk more effectively by incorporating real-world conditions about the assets, such as their exposure, known threats, and the effectiveness of controls/safeguards adopted. In the next post, we will bring these together to discuss risk quantification and management. Join our Balbix AI demo day to learn more.