
September 10, 2024
In this Patch Tuesday edition, Microsoft addressed 79 CVEs, including 4 Zero-Days, 7 Criticals, 71 Important and 1 Moderate. Out of the 4 Zero-Days, 3 are actively exploited in the wild.

From an Impact perspective, Escalation of Privilege (EoP) vulnerabilities accounted for 38%, followed by Remote Code Execution (RCE) at 29% and Information Disclosure (ID) at 14%.
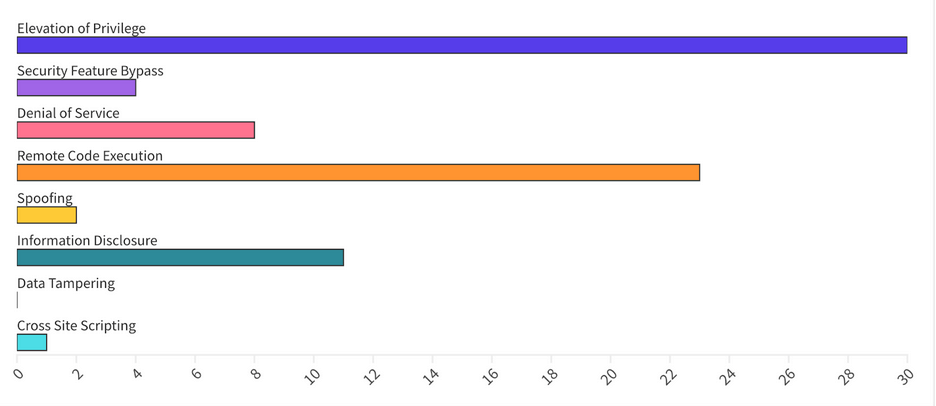
Patches for this month cover components for the following areas:
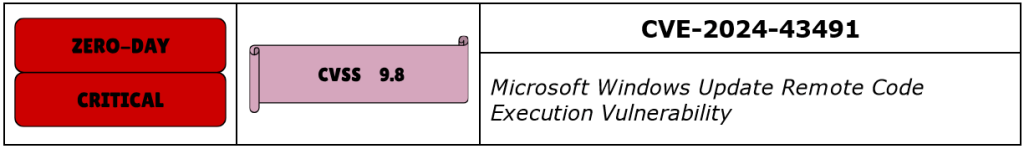
CVE-2024-43491 is a Critical Remote Code Execution vulnerability in Microsoft Windows Update Framework, the main Windows component that enables users to update their operating systems. It affects several versions of Windows 10, but it’s limited to Windows 10, reducing the impact. It has a CVSS score of 9.8, and Microsoft flagged it as exploited in the wild. CISA added it to the list of KEV—Known Exploited Vulnerabilities.
This vulnerability is related to the way the Servicing Stack is handling the Optional Components, and it has effectively rolled back the fixes recently released for several components, including Internet Explorer, Windows Media Player, .NET Framework, LDAP, Admin Tools, SMB File Sharing, etc. Microsoft flagged affected components as “not applicable”, so they were reverted to RTM.
An interesting note here is that Microsoft has marked this CVE as exploited in the wild, but at the same time, they said that there is no evidence of exploitation. CISA added it to KEV, regardless.
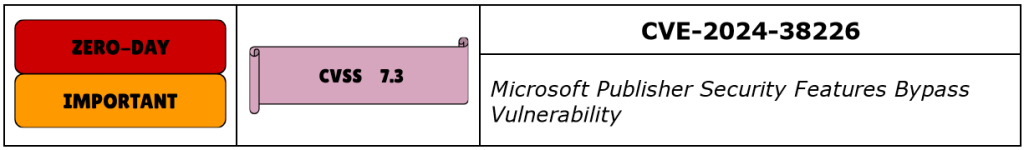
CVE-2024-38226 is a Security Feature Bypass vulnerability in Microsoft Publisher, a desktop publishing software widely used in publication design. It has a CVSS score of 7.3 and was also confirmed by Microsoft to be exploited in the wild. CISA also added it to their KEV list.
Successful exploitation of this vulnerability requires local authentication and a specially-crafted file to be pre-loaded on the asset, which suggests social engineering to get to this stage. This would then enable the bypass of Office macro policies and elevated access to the system.
CVE-2024-38014 is an Elevation of Privilege vulnerability affecting Windows Installer, the main Windows component that allows users to install and uninstall software. It has a CVSS score of 7.8 and was confirmed by Microsoft to be exploited in the wild.
Microsoft did not share details about the exploit or the prerequisites. However, it mentioned that a successful exploitation would grant the attacker system-level privileges.
CVE-2024-38217 is a Security Feature Bypass vulnerability in MoTW (Mark of the Web) – a security feature in Microsoft Windows that uses an identifier to mark files downloaded from the internet as potentially unsafe. It has a CVSS of 5.4, however, it’s flagged as exploited in the wild and publicly disclosed prior to the patch becoming available. It was also added to CISA’s KEV list.
To bypass the MoTW, attackers can sign malicious software with a code-signing certificate, a tactic observed in use by the attackers behind SolarMaker. From there, successful exploitation of this vulnerability requires, again, social engineering. A local user needs to open the specially crafted & signed file that could evade the defense mechanisms employed in MoTW.
CVE-2024-38018 is a Critical Remote Code Execution vulnerability affecting Microsoft SharePoint Server – a collaboration platform, part of Microsoft 365, that helps organizations manage content and streamline teamwork. It has a CVSS of 8.8 and is considered “More Likely” to be exploited.
Microsoft has’t provided information about the exploit, but noted that an attacker would need to be authenticated and have permission to create / edit page components, which would then enable the steps required for the exploitation to take place. So, although the attacker doesn’t need a significant level of access, it still needs to be a Site Member to conduct the attack.
| CVE | Severity | Type | CVSS | Exploitation |
| CVE-2024-21416 | Important | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-26186 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-26191 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-30073 | Important | Security Feature Bypass | 7.8 | Less Likely |
| CVE-2024-37335 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-37337 | Important | Information Disclosure | 7.1 | Less Likely |
| CVE-2024-37338 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-37339 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-37340 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-37341 | Important | Elevation of Privilege | 8.8 | Less Likely |
| CVE-2024-37342 | Important | Information Disclosure | 7.1 | Less Likely |
| CVE-2024-37965 | Important | Elevation of Privilege | 8.8 | Less Likely |
| CVE-2024-37966 | Important | Information Disclosure | 7.1 | Less Likely |
| CVE-2024-37980 | Important | Elevation of Privilege | 8.8 | Less Likely |
| CVE-2024-38014 | Important | Elevation of Privilege | 7.8 | KNOWN EXPLOIT |
| CVE-2024-38018 | Critical | Remote Code Execution | 8.8 | More Likely |
| CVE-2024-38045 | Important | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-38046 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38119 | Critical | Remote Code Execution | 7.5 | Less Likely |
| CVE-2024-38188 | Important | Elevation of Privilege | 7.1 | Less Likely |
| CVE-2024-38194 | Critical | Elevation of Privilege | 8.4 | Less Likely |
| CVE-2024-38216 | Critical | Elevation of Privilege | 8.2 | Less Likely |
| CVE-2024-38217 | Important | Security Feature Bypass | 5.4 | KNOWN EXPLOIT |
| CVE-2024-38220 | Critical | Elevation of Privilege | 9 | Less Likely |
| CVE-2024-38225 | Important | Elevation of Privilege | 8.8 | Less Likely |
| CVE-2024-38226 | Important | Security Feature Bypass | 7.3 | KNOWN EXPLOIT |
| CVE-2024-38227 | Important | Remote Code Execution | 7.2 | More Likely |
| CVE-2024-38228 | Important | Remote Code Execution | 7.2 | More Likely |
| CVE-2024-38230 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2024-38231 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2024-38232 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-38233 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-38234 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2024-38235 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2024-38236 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-38237 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38238 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38239 | Important | Elevation of Privilege | 7.2 | Less Likely |
| CVE-2024-38240 | Important | Elevation of Privilege | 8.1 | Less Likely |
| CVE-2024-38241 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38242 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38243 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38244 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38245 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38246 | Important | Elevation of Privilege | 7 | More Likely |
| CVE-2024-38247 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38248 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2024-38249 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38250 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38252 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38253 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38254 | Important | Information Disclosure | 5.5 | Less Likely |
| CVE-2024-38256 | Important | Information Disclosure | 5.5 | Less Likely |
| CVE-2024-38257 | Important | Information Disclosure | 7.5 | Less Likely |
| CVE-2024-38258 | Important | Information Disclosure | 6.5 | Less Likely |
| CVE-2024-38259 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38260 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38263 | Important | Remote Code Execution | 7.5 | Less Likely |
| CVE-2024-43454 | Important | Remote Code Execution | 7.1 | Less Likely |
| CVE-2024-43455 | Important | Spoofing | 8.8 | Less Likely |
| CVE-2024-43457 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-43458 | Important | Information Disclosure | 7.7 | Less Likely |
| CVE-2024-43461 | Important | Spoofing | 8.8 | More Likely |
| CVE-2024-43463 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-43464 | Critical | Remote Code Execution | 7.2 | More Likely |
| CVE-2024-43465 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-43466 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2024-43467 | Important | Remote Code Execution | 7.5 | Less Likely |
| CVE-2024-43469 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-43470 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2024-43474 | Important | Information Disclosure | 7.6 | Less Likely |
| CVE-2024-43475 | Important | Information Disclosure | 7.3 | Less Likely |
| CVE-2024-43476 | Important | Cross Site Scripting | 7.6 | Less Likely |
| CVE-2024-43479 | Important | Remote Code Execution | 8.5 | Less Likely |
| CVE-2024-43482 | Important | Information Disclosure | 6.5 | Less Likely |
| CVE-2024-43487 | Moderate | Security Feature Bypass | 6.5 | More Likely |
| CVE-2024-43491 | Critical | Remote Code Execution | 9.8 | KNOWN EXPLOIT |
| CVE-2024-43492 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-43495 | Important | Remote Code Execution | 7.3 | Less Likely |
ADOBE has released patches covering 28 vulnerabilities in a wide range of products, from Reader, Photoshop, After Effects, Premiere and Illustrator, to ColdFusion and Media Encoder.
Vulnerabilities released for Reader are of a particular importance, as this software is so widely adopted. CVE-2024-41869 (CVSS of 7.8) and CVE-2024-45112 (CVSS of 8.6) are to be patched as soon as possible, as both could potentially lead to Remote Code Execution.
CISCO has also fixed a few important security issues. CVE-2024-20469 (CVSS of 6.0) affects Identity Services Engine (ISE) – an identity-based NAC and Policy Enforcement solution and could allow a local attacker to perform command injections on the underlying OS.
CVE-2024-20439 and CVE-2024-20440 (CVSS of 9.8!) are affecting Cisco Smart Licensing Utility, potentially allowing an attacker to access the system remotely with admin permissions.
APACHE fixed a critical security vulnerability in its open-source OFBiz, tracked under CVE-2024-45195 (CVSS of 9.8!), which could allow a remote and unauthenticated attacker to execute remote code on vulnerable Linux and Windows servers.
IVANTI released a critical update resolving a security issue tracked by CVE-2024-7593 (CVSS of 9.8!) for Virtual Traffic Manager (vTM) appliances that could allow an attacker admin access. This vulnerability is caused by an incorrect coding of an authentication algorithm that allows remote unauthenticated attackers to bypass authentication on Internet-exposed vTM admin panels.
VEEAM has released several security updates for their products including Veeam One, Backup & Replication, Service Provider Console. The most important one is CVE-2024-40711 (CVSS of 9.8!), which is an RCE vulnerability in VBR that can be exploited without authentication.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy is prioritizing what matters most and reducing the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
This way, Risk-Based Prioritization is already done, and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
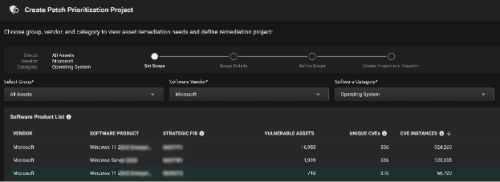
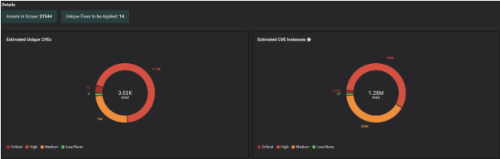
This way, Balbix customers have a clear understanding of the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.