

May 15, 2024
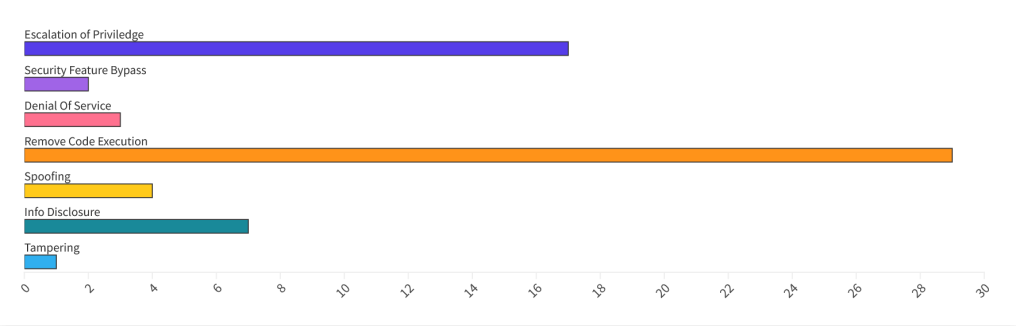
In this Patch Tuesday edition, Microsoft addressed 59 CVEs, one critical, 57 important, and one moderate. Three are for zero-day vulnerabilities, two of which are exploited in the wild. If we include the third-party CVEs documented by Microsoft, the total CVE count rises to 63.

Patches cover components from Windows, Office, .NET Framework, Visual Studio, Dynamics 365, Azure, Power BI, Intune, Edge, Bing, SQL and Mobile Broadband.
From an Impact perspective, Remote Code Execution (RCE) vulnerabilities accounted for 46%, followed by Elevation of Privilege (EoP) at 27% and Information Disclosure at 11%.
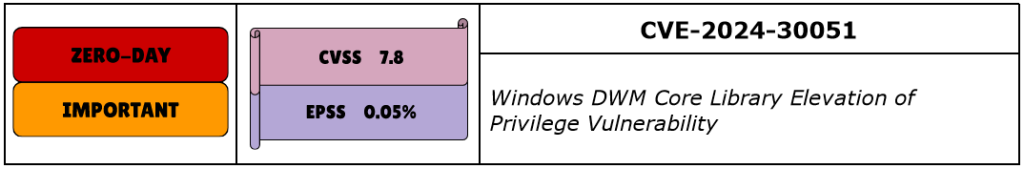
CVE-2024-30051 is an Escalation of Privilege vulnerability in the DWM Core Library of Windows OS and is rated by Microsoft as Important. Given that it’s a zero-day with a CVSS of 7.8, already listed on CISA KEV, this vulnerability should be considered one of key priorities to patch.
An attacker who exploits this vulnerability would need to have local presence on target, as it’s not remotely accessible. No user interaction beyond opening a file is required, increasing its potential for automated attacks. It affects Windows 10, 11 as well as Server 2016 and up.
This vulnerability was discovered by researchers at Kaspersky, Mandiant and Google, who found indications that its TTPs are linked to QakBot and have evidence that multiple threat actors are using it. Kaspersky published a detailed article on how they discovered the exploit and the TTPs.
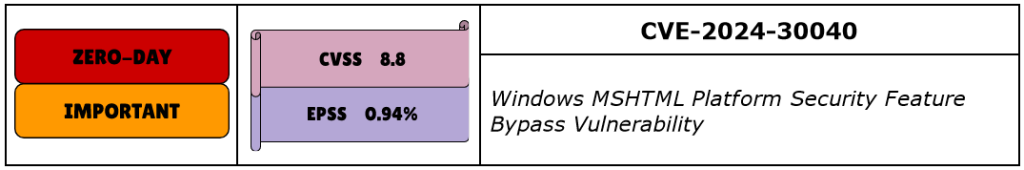
CVE-2024-30040 is a Security Feature Bypass vulnerability in Windows MSHTML engine, which is used to render browser-based content by multiple Windows and Office components. It’s also a zero-day, rated Important, with a CVSS of 8.8, and was also added to CISA KEV.
By opening a malicious document, successful exploitation of this vulnerability bypasses COM/OLE protections and leads to the execution of arbitrary code in the current user context. It could be chained with privilege escalation vulnerabilities to complete complex end-to-end attacks.
Microsoft has not disclosed who reported this vulnerability and did not provide additional details.
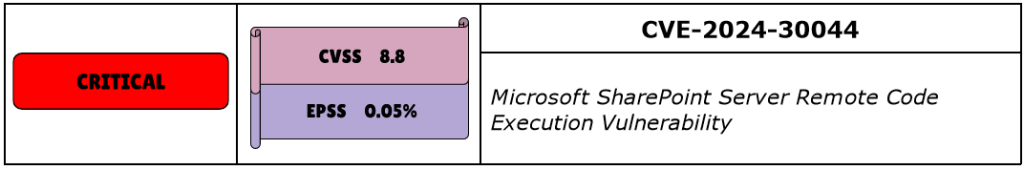
CVE-2024-30044 is a Remote Code Execution vulnerability affecting Microsoft SharePoint Server 2016, 2019 and Subscription Edition. It has a CVSS of 8.8 and is rated Critical. Although it has the tag of “Exploitation More Likely”, the EPSS score is 0.05%. However, it is well known that EPSS is not very accurate for new vulnerabilities.
While severity is very high, to exploit this vulnerability, an attacker needs to be authenticated to a vulnerable SharePoint Server with site owner permissions and perform two steps: 1) upload a specially crafted file to the vulnerable SharePoint Server; 2) send API requests to the SharePoint Server to “trigger deserialization of file’s parameters.” Successful exploitation would result in remote code execution “in the context of the SharePoint Server.”
The last Microsoft zero-day of May is CVE-2024-30046, which is a Denial of Service (DoS) vulnerability affecting Microsoft Visual Studio 2022, .NET 8.0 / 7.0. It has a CVSS of 5.9 and it’s flagged as publicly disclosed, but not under active exploitation.
The reason we pulled this vulnerability forward in today’s article is not related to its severity, but it serves as a good example that not everything that’s marked zero-day should be a priority. Running a good risk-based vulnerability management (RBVM) program means that you have a clear strategy for how you tackle vulnerabilities and cyber risk. And focusing on zero-days without contextual understanding takes up time and resources from other vulnerabilities that have a greater risk.
| # | CVE | Severity | Type | CVSS | EPSS | Public | Exploited |
| 1 | CVE-2024-30051 | Important | EoP | 7.8 | 0.05% | Yes | Yes |
| 2 | CVE-2024-30040 | Important | SFB | 8.8 | 0.94% | No | Yes |
| 3 | CVE-2024-30046 | Important | DoS | 5.9 | 0.04% | Yes | No |
| 4 | CVE-2024-30044 | Critical | RCE | 8.8 | 0.05% | No | No |
| 5 | CVE-2024-30045 | Important | RCE | 6.3 | 0.05% | No | No |
| 6 | CVE-2024-30053 | Important | Spoofing | 7.5 | 0.05% | No | No |
| 7 | CVE-2024-32002 | Important | RCE | 9.8 | 0.05% | No | No |
| 8 | CVE-2024-30019 | Important | DoS | 6.5 | 0.04% | No | No |
| 9 | CVE-2024-30047 | Important | Spoofing | 7.6 | 0.05% | No | No |
| 10 | CVE-2024-30048 | Important | Spoofing | 7.6 | 0.05% | No | No |
| 11 | CVE-2024-32004 | Important | RCE | 8.8 | 0.05% | No | No |
| 12 | CVE-2024-30041 | Important | Spoofing | 5.4 | 0.05% | No | No |
| 13 | CVE-2024-30007 | Important | EoP | 8.8 | 0.04% | No | No |
| 14 | CVE-2024-30042 | Important | RCE | 7.8 | 0.05% | No | No |
| 15 | CVE-2024-26238 | Important | EoP | 7.8 | 0.04% | No | No |
| 16 | CVE-2024-30054 | Important | Info | 6.5 | 0.12% | No | No |
| 17 | CVE-2024-30043 | Important | Info | 6.5 | 0.09% | No | No |
| 18 | CVE-2024-30006 | Important | RCE | 8.8 | 0.09% | No | No |
| 19 | CVE-2024-29994 | Important | EoP | 7.8 | 0.04% | No | No |
| 20 | CVE-2024-30027 | Important | EoP | 7.8 | 0.04% | No | No |
| 21 | CVE-2024-30028 | Important | EoP | 7.8 | 0.04% | No | No |
| 22 | CVE-2024-30030 | Important | EoP | 7.8 | 0.04% | No | No |
| 23 | CVE-2024-30038 | Important | EoP | 7.8 | 0.04% | No | No |
| 24 | CVE-2024-30034 | Important | Info | 5.5 | 0.05% | No | No |
| 25 | CVE-2024-30031 | Important | EoP | 7.8 | 0.04% | No | No |
| 26 | CVE-2024-29996 | Important | EoP | 7.8 | 0.04% | No | No |
| 27 | CVE-2024-30025 | Important | EoP | 7.8 | 0.04% | No | No |
| 28 | CVE-2024-30037 | Important | EoP | 7.5 | 0.05% | No | No |
| 29 | CVE-2024-30016 | Important | Info | 5.5 | 0.04% | No | No |
| 30 | CVE-2024-30020 | Important | RCE | 8.1 | 0.09% | No | No |
| 31 | CVE-2024-30036 | Important | Info | 6.5 | 0.05% | No | No |
| 32 | CVE-2024-30032 | Important | EoP | 7.8 | 0.04% | No | No |
| 33 | CVE-2024-30035 | Important | EoP | 7.8 | 0.04% | No | No |
| 34 | CVE-2024-30008 | Important | Info | 5.5 | 0.04% | No | No |
| 35 | CVE-2024-30011 | Important | DoS | 6.5 | 0.05% | No | No |
| 36 | CVE-2024-30010 | Important | RCE | 8.8 | 0.04% | No | No |
| 37 | CVE-2024-30017 | Important | RCE | 8.8 | 0.05% | No | No |
| 38 | CVE-2024-30018 | Important | EoP | 7.8 | 0.04% | No | No |
| 39 | CVE-2024-29997 | Important | RCE | 6.8 | 0.05% | No | No |
| 40 | CVE-2024-29998 | Important | RCE | 6.8 | 0.05% | No | No |
| 41 | CVE-2024-29999 | Important | RCE | 6.8 | 0.05% | No | No |
| 42 | CVE-2024-30000 | Important | RCE | 6.8 | 0.05% | No | No |
| 43 | CVE-2024-30001 | Important | RCE | 6.8 | 0.05% | No | No |
| 44 | CVE-2024-30002 | Important | RCE | 6.8 | 0.05% | No | No |
| 45 | CVE-2024-30003 | Important | RCE | 6.8 | 0.05% | No | No |
| 46 | CVE-2024-30004 | Important | RCE | 6.8 | 0.05% | No | No |
| 47 | CVE-2024-30005 | Important | RCE | 6.8 | 0.05% | No | No |
| 48 | CVE-2024-30012 | Important | RCE | 6.8 | 0.05% | No | No |
| 49 | CVE-2024-30021 | Important | RCE | 6.8 | 0.05% | No | No |
| 50 | CVE-2024-30039 | Important | Info | 5.5 | 0.04% | No | No |
| 51 | CVE-2024-30009 | Important | RCE | 8.8 | 0.09% | No | No |
| 52 | CVE-2024-30014 | Important | RCE | 7.5 | 0.09% | No | No |
| 53 | CVE-2024-30015 | Important | RCE | 7.5 | 0.09% | No | No |
| 54 | CVE-2024-30022 | Important | RCE | 7.5 | 0.09% | No | No |
| 55 | CVE-2024-30023 | Important | RCE | 7.5 | 0.09% | No | No |
| 56 | CVE-2024-30024 | Important | RCE | 7.5 | 0.09% | No | No |
| 57 | CVE-2024-30029 | Important | RCE | 7.5 | 0.09% | No | No |
| 58 | CVE-2024-30033 | Important | EoP | 7 | 0.05% | No | No |
| 59 | CVE-2024-30049 | Important | EoP | 7.8 | 0.04% | No | No |
| 60 | CVE-2024-30059 | Important | Tamper | 6.1 | 0.04% | No | No |
| 61 | CVE-2024-30050 | Moderate | SFB | 5.4 | 0.05% | No | No |
| 62 | CVE-2024-4331 | High | RCE | N/A | 0.05% | No | No |
| 63 | CVE-2024-4368 | High | RCE | N/A | 0.05% | No | No |
Apple released the macOS Sonoma 14.5 update with over 20 security patches. In addition, a key update is for CVE-2024-23296, a zero-day vulnerability, fixing a memory corruption issue in RTKit that could allow attackers to bypass kernel memory protections. The initial patch was released in March, and now Apple is backporting patches to all other products.
Adobe released 8 patches covering 37 CVEs for many of its products. The priority should be the update for Adobe Reader, which includes a set of critical vulnerabilities that are historically known to be the focus on targeted attacks due to the widespread use of PDF file format. None of the vulnerabilities fixed by Adobe this month are known to be under active exploitation.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy is to prioritize what matters most and reduce the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are being exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all i.e. monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, and others.
If you are interested in learning more, please sign up for a Balbix demo.