

June 11, 2024
In this Patch Tuesday edition, Microsoft addressed 49 CVEs across its entire portfolio of products. One was marked Critical and 48 Important. No zero-days and none of them exploited in the wild. If we include the third-party CVEs documented by Microsoft, the total CVE count rises to 51.

Patches cover components from Windows, Office, Visual Studio, Dynamics, Azure, Edge, SharePoint, SQL, OS Drivers, File System and Storage Services, and Container Services.
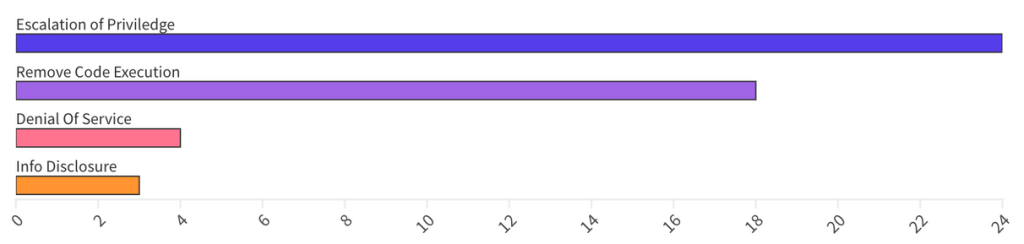
From an Impact perspective, Escalation of Privilege (EoP) vulnerabilities accounted for 49%, followed by Remote Code Execution (RCE) at 37% and Denial of Service (DOS) at 8%.
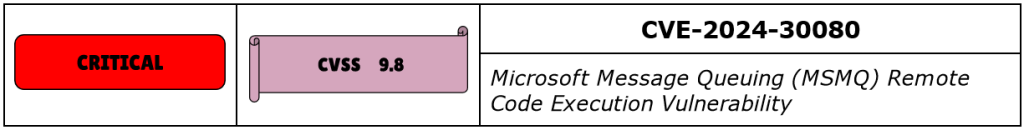
CVE-2024-30080 is a Remote Code Execution RCE vulnerability in Microsoft Message Queuing MSMQ, which is an OS component that enables applications running at different times to communicate across heterogeneous networks and systems that may be temporarily offline. Although MSMQ was discontinued by Microsoft in 2019, and replaced by more modern architectures like Kafka, it’s still being used in Windows 7 / 8 / 10, Server 2008 / 2012.
This CVE has a CVSS score of 9.8 and is rated by Microsoft as Critical. To be able to exploit it, a threat actor may send crafted messages to the MSMQ service on TCP 1801, through which may then run server side RCEs.
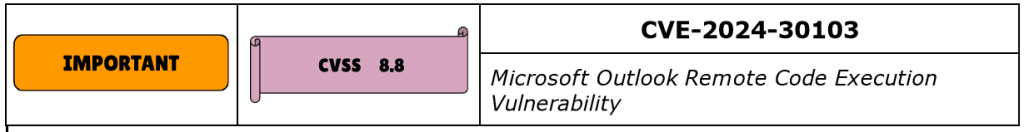
CVE-2024-30103 is another Remote Code Execution RCE vulnerability, this time in Microsoft Outlook. It has a CVSS score of 8.8. The attacker must be authenticated with valid Exchange credentials.
By successfully exploiting this vulnerability using Outlook Application Preview Pane as the attack vector, an attacker can create malicious DLL files, bypassing all of Outlook’s security measures.
Morphisec researchers Michael Gorelik and Shmuel Uzan discovered the vulnerability, noting its particular danger for accounts utilizing Microsoft Outlook’s auto-open email feature, as the execution begins upon opening an affected email.
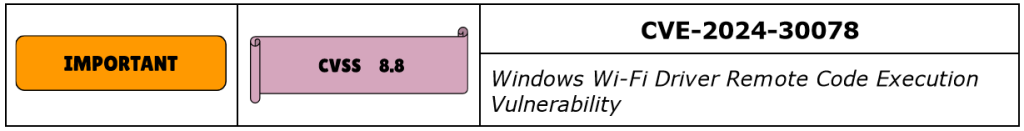
CVE-2024-30078 is another Remote Code Execution RCE vulnerability, affecting the Windows Wi-Fi driver. It has a CVSS score of 8.8, allowing an unauthenticated attacker to initially exploit the vulnerability by sending specially crafted packets, which can then lead to RCE. It’s important to note that the attacker needs to be in the physical proximity of the target to have Wi-Fi access.
We selected this vulnerability because:
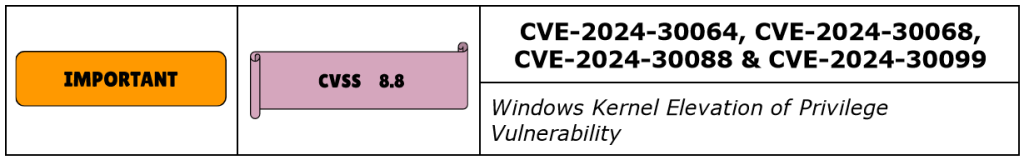
CVE-2024-30064, CVE-2024-30068, CVE-2024-30088, CVE-2024-30099 are Escalation Of Privilege EOP vulnerabilities affecting Windows Kernel, with CVSS score between 7.0 – 8.8 and rated by Microsoft as Important.
CVE-2024-30064 and CVE-2024-30068 have the higher CVSS score and are both rated as “Exploitation Less Likely”, while the other two CVEs are rated as “Exploitation More Likely”.
By exploiting these vulnerabilities through a low-privilege AppContainer, an attacker could gain SYSTEM privileges, from where he could execute code or access resources. It’s important to note that the attacker needs to first be able to authenticate to the system and be able to execute a specially crafted exploit, which makes the exploit to be less likely.
| # | CVE | Severity | Type | CVSS | Known Exploit |
| 1 | CVE-2024-30052 | Important | Remote Code Execution | 4.7 | No |
| 2 | CVE-2024-37325 | Important | Elevation of Privilege | 8.1 | No |
| 3 | CVE-2024-35265 | Important | Elevation of Privilege | 7.0 | No |
| 4 | CVE-2024-35263 | Important | Information Disclosure | 5.7 | No |
| 5 | CVE-2024-35254 | Important | Elevation of Privilege | 7.1 | No |
| 6 | CVE-2024-35253 | Important | Elevation of Privilege | 4.4 | No |
| 7 | CVE-2024-35252 | Important | Denial of Service | 7.5 | No |
| 8 | CVE-2024-35249 | Important | Remote Code Execution | 8.8 | No |
| 9 | CVE-2024-35248 | Important | Elevation of Privilege | 7.3 | No |
| 10 | CVE-2024-30104 | Important | Remote Code Execution | 7.8 | No |
| 11 | CVE-2024-30103 | Important | Remote Code Execution | 8.8 | No |
| 12 | CVE-2024-30102 | Important | Remote Code Execution | 7.3 | No |
| 13 | CVE-2024-30101 | Important | Remote Code Execution | 7.5 | No |
| 14 | CVE-2024-30100 | Important | Remote Code Execution | 7.8 | No |
| 15 | CVE-2024-30099 | Important | Elevation of Privilege | 7.0 | No |
| 16 | CVE-2024-30097 | Important | Remote Code Execution | 8.8 | No |
| 17 | CVE-2024-30096 | Important | Information Disclosure | 5.5 | No |
| 18 | CVE-2024-30095 | Important | Remote Code Execution | 7.8 | No |
| 19 | CVE-2024-30094 | Important | Remote Code Execution | 7.8 | No |
| 20 | CVE-2024-30093 | Important | Elevation of Privilege | 7.3 | No |
| 21 | CVE-2024-30091 | Important | Elevation of Privilege | 7.8 | No |
| 22 | CVE-2024-30090 | Important | Elevation of Privilege | 7.0 | No |
| 23 | CVE-2024-30089 | Important | Elevation of Privilege | 7.8 | No |
| 24 | CVE-2024-30088 | Important | Elevation of Privilege | 7.0 | No |
| 25 | CVE-2024-30087 | Important | Elevation of Privilege | 7.8 | No |
| 26 | CVE-2024-30086 | Important | Elevation of Privilege | 7.8 | No |
| 27 | CVE-2024-30085 | Important | Elevation of Privilege | 7.8 | No |
| 28 | CVE-2024-30084 | Important | Elevation of Privilege | 7.0 | No |
| 29 | CVE-2024-30083 | Important | Denial of Service | 7.5 | No |
| 30 | CVE-2024-30068 | Important | Elevation of Privilege | 8.8 | No |
| 31 | CVE-2024-30067 | Important | Elevation of Privilege | 5.5 | No |
| 32 | CVE-2024-30066 | Important | Elevation of Privilege | 5.5 | No |
| 33 | CVE-2024-30065 | Important | Denial of Service | 5.5 | No |
| 34 | CVE-2024-30064 | Important | Elevation of Privilege | 8.8 | No |
| 35 | CVE-2024-30063 | Important | Remote Code Execution | 6.7 | No |
| 36 | CVE-2024-30062 | Important | Remote Code Execution | 7.8 | No |
| 37 | CVE-2024-29060 | Important | Elevation of Privilege | 6.7 | No |
| 38 | CVE-2024-29187 | Important | Elevation of Privilege | 7.3 | No |
| 39 | CVE-2023-50868 | Important | Denial of Service | 7.5 | No |
| 40 | CVE-2024-35255 | Important | Elevation of Privilege | 5.5 | No |
| 41 | CVE-2024-35250 | Important | Elevation of Privilege | 7.8 | No |
| 42 | CVE-2024-30082 | Important | Elevation of Privilege | 7.8 | No |
| 43 | CVE-2024-30080 | Critical | Remote Code Execution | 9.8 | No |
| 44 | CVE-2024-30078 | Important | Remote Code Execution | 8.8 | No |
| 45 | CVE-2024-30077 | Important | Remote Code Execution | 8.0 | No |
| 46 | CVE-2024-30076 | Important | Elevation of Privilege | 6.8 | No |
| 47 | CVE-2024-30075 | Important | Remote Code Execution | 8.0 | No |
| 48 | CVE-2024-30074 | Important | Remote Code Execution | 8.0 | No |
| 49 | CVE-2024-30072 | Important | Remote Code Execution | 7.8 | No |
| 50 | CVE-2024-30070 | Important | Denial of Service | 7.5 | No |
| 51 | CVE-2024-30069 | Important | Information Disclosure | 4.7 | No |
PHP – Security researcher Orange Tsai uncovered a major vulnerability in PHP CGI, affecting all versions of PHP on Windows systems, enabling attackers to execute unauthorized code. Tracked under CVE-2024-4577, this vulnerability affects XAMPP, a widely used software package for deploying various web server components like PHP, MySQL, Apache Server, and Tomcat.
The development team misused the Windows’ encoding conversion feature, leading to this CVE. Attackers could exploit this flaw by using specific character strings to bypass security measures, leading to arbitrary code execution on remote PHP servers through argument injection attacks. This highlights the importance of thorough testing and review to prevent such vulnerabilities.
Google – announced Chrome 125, which among others includes a fix for a zero day vulnerability. CVE-2024-4947 is a type confusion flaw detected in Java Script V8 engine, which has already been exploited. This CVE enables a remote attacker to execute arbitrary code within a sandbox environment by utilizing a specifically crafted HTML page. Google didn’t provide further details.
Another notable issue resolved in Chrome 125 is CVE-2024-4948, a significant use-after-free vulnerability found in Dawn, an open-source implementation of the WebGPU standard across various platforms within Chromium.
GitHub – has released an advisory addressing a critical vulnerability in GitHub Enterprise Server. Identified as CVE-2024-4985, this vulnerability has the maximum CVSS score of 10 and is affecting all versions of Enterprise Server up to 3.13.0 that utilize SAML single sign-on (SSO) authentication with encrypted assertions enabled. Exploiting this vulnerability could allow an attacker to gain administrative privileges without authentication by changing SAML responses.
CheckPoint – Tracked under CVE-2024-24919, a critical zero-day vulnerability has been detected in CheckPoint VPNs, linked to attacks detected since April 2024. This vulnerability has a CVSS score of 8.6 and involves arbitrary file reading in gateways with IPSec VPN or Mobile Access blades. Exploitation could lead to access to sensitive information and domain administrator privileges. CheckPoint released urgent patches for their CloudGuard and Quantum product lines. This CVE allows remote exploitation without user interaction or special privileges on compromised CheckPoint gateways with remote access VPN and mobile access enabled.
As always, you should patch everything as soon as possible… 😉
But, that’s a lot easier said than done. The strategy is to prioritize what matters most and reduce the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are being exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all i.e. monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, and others.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as CVEs were announced by vendors. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs, the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
In this way the Risk Based Prioritization is already done and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
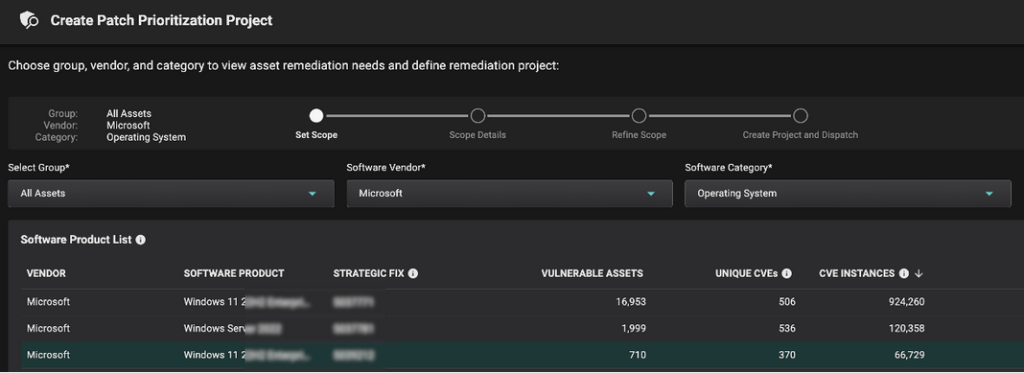
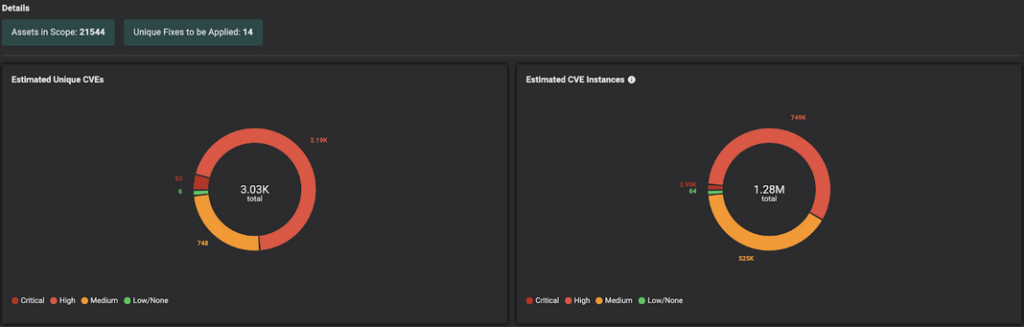
This way Balbix customers have a clear understanding of the assets in scope, unique CVE detections, unique patches to be applied, etc. And most importantly, the priority in which patches need to be installed, to burn down risk in the most efficient way possible.
If you are interested in learning more, please sign up for a Balbix demo.