February 11, 2025
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 67 CVEs, including 4 Zero-Day, 3 Critical, and 53 Important—with 2 Zero-Days actively exploited in the wild.

From an Impact perspective, Escalation of Privilege (EoP) vulnerabilities accounted for 21%, followed by Remote Code Execution (RCE) at 29% and Denial of Service (DoS) at 9%.
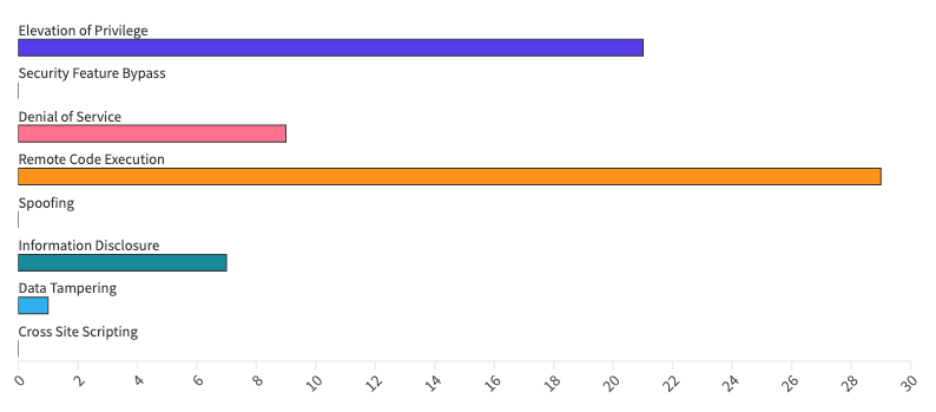
Patches for this month cover components for the following areas:
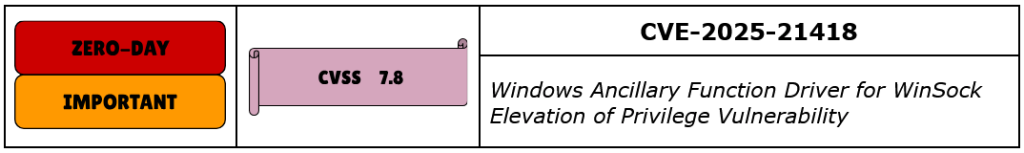
CVE-2025-21418 is an Elevation of Privilege (EoP) vulnerability in the Windows Ancillary Function Driver for WinSock (afd.sys). This heap-based buffer overflow issue has been actively exploited in the wild as a zero-day. It allows a local, authenticated attacker to execute arbitrary code with SYSTEM-level privileges, making it a prime target for post-compromise exploitation.
This vulnerability stems from improper memory handling in afd.sys, where an attacker can trigger a buffer overflow by crafting specific API calls that interact with Winsock. This corruption can lead to controlled memory overwrites, enabling privilege escalation. Since afd.sys operates within the kernel space, successful exploitation grants full control over the affected system.
Microsoft has assigned CVE-2025-21418 a CVSS score of 7.8, rating it as Important. Security researchers have drawn parallels to previous afd.sys vulnerabilities, including CVE-2024-38193, which was leveraged by the Lazarus Group for deploying the FudModule rootkit.
CVE-2025-21391 is an Elevation of Privilege (EoP) vulnerability in Microsoft Windows Storage Services. This flaw exists due to improper handling of symbolic links within the Windows storage subsystem, specifically in the NTFS file system. The vulnerability allows a local, authenticated attacker to delete critical system files by exploiting how symbolic links are processed, potentially leading to system instability, service disruptions, or data loss.
An attacker can create a malicious symbolic link that points to sensitive or essential system files or directories. When the system interacts with the link, it inadvertently deletes the file or directory it points to, because symbolic links are not properly validated before deletion operations are performed. This can be used to disrupt system functionality or lead to a denial-of-service condition if critical files are targeted.
Microsoft has assigned CVE-2025-21391 a CVSSv3 score of 7.1, classifying it as high severity. The vulnerability has been confirmed to be actively exploited in the wild, making patching an urgent priority.
CVE-2025-21194 is a Security Feature Bypass (SFB) vulnerability affecting Microsoft Surface devices. It has been assigned a CVSS score of 7.1, and was rated as Important.
The vulnerability is related to the handling of Unified Extensible Firmware Interface (UEFI) settings in virtualized environments on Surface devices. An attacker with access to the same network as the target device could exploit this flaw by convincing the user to reboot their device, leading to a bypass of UEFI security features and potential compromise of the system’s hypervisor.
Microsoft has assessed the exploitation of this vulnerability as “Less Likely” due to the specific conditions required for a successful attack, including network proximity and user interaction.
As of now, there is no evidence of this vulnerability being exploited in the wild.
CVE-2025-21377 is a NTLM Hash Disclosure Spoofing vulnerability affecting Microsoft Windows, allowing an attacker to obtain NTLM password hashes, which can be used in further attacks such as pass-the-hash or brute-force attempts.
The vulnerability has been assigned a CVSSv3 score of 6.5, indicating a medium severity level and is rated as Important. The exploitation of this vulnerability requires the attacker to have access to the same network as the target system. By leveraging this access, the attacker can intercept NTLM authentication traffic and extract the password hashes. These hashes can then be used to authenticate as the user without knowing the actual password, potentially leading to unauthorized access to sensitive information or systems.
As of now, there is no evidence of this vulnerability being exploited in the wild.
CVE-2025-21376 is a critical Remote Code Execution (RCE) vulnerability affecting the Windows Lightweight Directory Access Protocol (LDAP) service. This vulnerability has been assigned a CVSSv3 score of 8.1, reflecting its high severity.
The vulnerability stems from a race condition within the LDAP service. An attacker can exploit this by sending a specially crafted request to the LDAP server, leading to a buffer overflow. This overflow allows the attacker to execute arbitrary code on the affected system, potentially compromising its integrity and confidentiality.
Microsoft has assessed the exploitation of this vulnerability as “More Likely”. Given its critical nature, administrators should fix this one on priority.
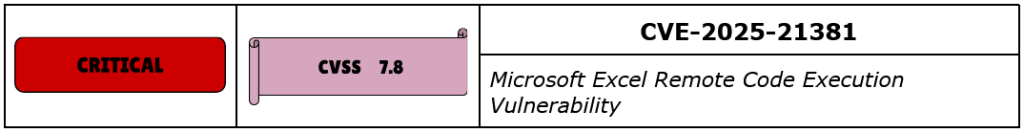
CVE-2025-21381 is a Remote Code Execution (RCE) vulnerability affecting Microsoft Excel. This vulnerability has been assigned a CVSSv3.1 score of 7.8, indicating a high severity level.
The vulnerability stems from improper handling of objects in memory. An attacker can exploit this flaw by crafting a malicious Excel file (e.g., .xls or .xlsx) containing specially crafted data that triggers the vulnerability. When a user opens this malicious file, it can lead to memory corruption, allowing the attacker to execute arbitrary code with the same privileges as the user.
Exploitation of this vulnerability requires user interaction, as the attack vector involves convincing a user to open the malicious Excel file. The attack complexity is considered low, and no elevated privileges are necessary for successful exploitation. The impact on confidentiality, integrity, and availability is high, as arbitrary code execution can compromise the system.
As of now, there is no evidence of this vulnerability being exploited in the wild. However, given its potential impact, and Critical rating, it’s recommended that users apply the update fast.
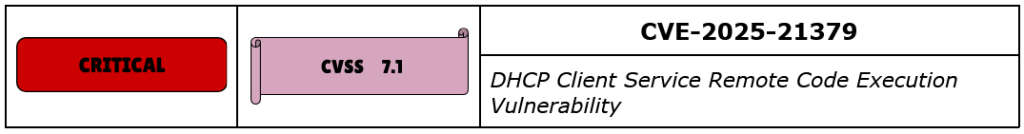
CVE-2025-21379 is a Remote Code Execution (RCE) vulnerability affecting the Windows DHCP Client Service. This vulnerability has been assigned a CVSS score of 7.1, and rated Critical.
The vulnerability stems from improper handling of DHCP responses by the client service. An attacker on the same network segment can exploit this flaw by setting up a rogue DHCP server and sending specially crafted DHCP responses to a target system. These malicious responses can trigger a buffer overflow in the DHCP client service, allowing the attacker to execute arbitrary code with SYSTEM privileges.
Exploitation of this vulnerability requires a high attack complexity, as the attacker must perform a machine-in-the-middle (MITM) attack to intercept or inject DHCP traffic between the client and the legitimate DHCP server. The attack vector is adjacent, meaning it is limited to systems on the same network segment, such as those connected to the same network switch or wireless access point.
| CVE | Severity | Type | CVSS | Exploitation |
| CVE-2025-21177 | Critical | Elevation of Privilege | 8.7 | — |
| CVE-2025-21179 | Important | Denial of Service | 4.8 | Less Likely |
| CVE-2025-21181 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2025-21182 | Important | Elevation of Privilege | 7.4 | Less Likely |
| CVE-2025-21183 | Important | Elevation of Privilege | 7.4 | Less Likely |
| CVE-2025-21184 | Important | Elevation of Privilege | 7 | More Likely |
| CVE-2025-21188 | Important | Elevation of Privilege | 6 | Less Likely |
| CVE-2025-21190 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21194 | Important | Information Disclosure | 7.1 | Less Likely |
| CVE-2025-21198 | Important | Remote Code Execution | 9 | Less Likely |
| CVE-2025-21200 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21201 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21206 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2025-21208 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21212 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2025-21216 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2025-21253 | Moderate | Information Disclosure | 5.3 | Less Likely |
| CVE-2025-21254 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2025-21259 | Important | Information Disclosure | 5.3 | Less Likely |
| CVE-2025-21267 | Low | Information Disclosure | 4.4 | Less Likely |
| CVE-2025-21279 | Important | Remote Code Execution | 6.5 | Less Likely |
| CVE-2025-21283 | Important | Remote Code Execution | 6.5 | Less Likely |
| CVE-2025-21322 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-21337 | Important | Elevation of Privilege | 3.3 | Less Likely |
| CVE-2025-21342 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21347 | Important | Denial of Service | 6 | Less Likely |
| CVE-2025-21349 | Important | Data Tampering | 6.8 | Less Likely |
| CVE-2025-21350 | Important | Denial of Service | 5.9 | Less Likely |
| CVE-2025-21351 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2025-21352 | Important | Denial of Service | 6.5 | Less Likely |
| CVE-2025-21358 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2025-21359 | Important | Information Disclosure | 7.8 | Less Likely |
| CVE-2025-21367 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2025-21368 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21369 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21371 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21373 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-21375 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-21376 | Critical | Remote Code Execution | 8.1 | More Likely |
| CVE-2025-21377 | Important | Information Disclosure | 6.5 | More Likely |
| CVE-2025-21379 | Critical | Remote Code Execution | 7.1 | Less Likely |
| CVE-2025-21381 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-21383 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-21386 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-21387 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-21390 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-21391 | Important | Elevation of Privilege | 7.1 | KNOWN EXPLOIT |
| CVE-2025-21392 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-21394 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-21397 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-21400 | Important | Remote Code Execution | 8 | More Likely |
| CVE-2025-21404 | Low | Information Disclosure | 4.3 | Less Likely |
| CVE-2025-21406 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21407 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21408 | Important | Remote Code Execution | 8.8 | Exploitation Unlikely |
| CVE-2025-21410 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-21414 | Important | Elevation of Privilege | 7 | More Likely |
| CVE-2025-21418 | Important | Elevation of Privilege | 7.8 | KNOWN EXPLOIT |
| CVE-2025-21419 | Important | Elevation of Privilege | 7.1 | More Likely |
| CVE-2025-21420 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2025-24036 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2025-24039 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2025-24042 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2025-0444 | High | Remote Code Execution | N/A | — |
| CVE-2025-0445 | High | Remote Code Execution | N/A | — |
| CVE-2025-0451 | Medium | Remote Code Execution | N/A | — |
| CVE-2023-32002 | Important | Remote Code Execution | 9.8 | — |
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
This way, Risk-Based Prioritization is already done, and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
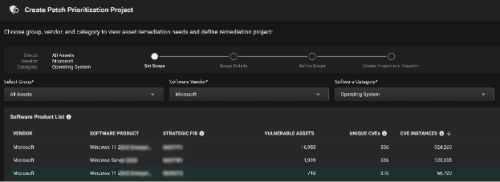
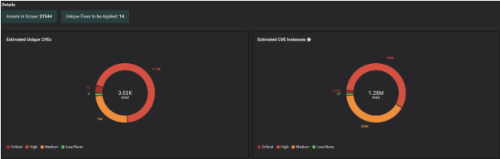
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.