

December 10, 2024
In this Patch Tuesday edition, Microsoft addressed 72 CVEs, including 1 Zero-Day, 16 Criticals, 54 Important and 1 Moderate—the one Zero-Day was found to be actively exploited in the wild.

From an Impact perspective, Escalation of Privilege (EoP) vulnerabilities accounted for 23%, followed by Remote Code Execution (RCE) at 38% and Denial of Service (DoS) at 21%.

Patches for this month cover components for the following areas:

CVE-2024-49138 is an Escalation of Privilege vulnerability in CLFS, Common Log File System, the logging service that can be used by applications that need to log events or data. It has a CVSS score of 7.8, and it’s rated Important.
A successful exploit of this vulnerability could allow an attacker to gain access at the system level. Microsoft has evidence that CVE-2024-49138 was exploited in the wild as a zero-day, which prompted CISA to add it to the Known Exploited Vulnerabilities list – as an urgent fix.
Microsoft has not released any information related to the exploit workflow used in attacks, which usually suggests that the exploit is fairly simple. Security researchers are working on this as a priority, so we’ll probably get updates soon. Until then, it’s important to patch this one fast.

CVE-2024-49118 and CVE-2024-49122 are Remote Code Execution vulnerabilities in MSMQ – Microsoft Message Queuing – the Windows component that allows applications to communicate with each other across networks and systems, even if they’re not running at the same time or are temporarily offline.
Both vulnerabilities have a CVSS score of 8.1 and are rated as Critical. An attacker must craft and send malicious packets to a vulnerable MSMQ server to successfully exploit these vulnerabilities. Upon exploitation, the attacker can perform Remote Code Execution on the server side. For a system to be vulnerable, the MSMQ service must first be added and enabled. This can be verified for troubleshooting by checking if a service named “Message Queueing” is running on TCP port 1801. Microsoft noted that CVE-2024-49118 is less likely to be exploited, while CVE-2024-49122 is more likely.

CVE-2024-49106, CVE-2024-49108, CVE-2024-49115, CVE-2024-49116, CVE-2024-49119, CVE-2024-49120, CVE-2024-49123, CVE-2024-49128 and CVE-2024-49132 are Remote Code Execution vulnerabilities affecting the Windows Remote Desktop Gateway (RD Gateway) Service, a Windows service that enables users on public networks to access network resources from any device that supports the Remote Desktop Connection client.
All these vulnerabilities have a CVSS score of 8.1 and are rated as Critical, making them very dangerous, especially as RDP is ubiquitous. However, successful exploitation is complex, requiring the attacker to “create a use-after-free scenario,” leading to malicious code execution. As a result, Microsoft rated these vulnerabilities as less likely to be exploited. Microsoft has not detected active exploitation of these vulnerabilities in the wild.

CVE-2024-49117 is a Critical Remote Code Execution vulnerability in Windows Hyper-V, Microsoft’s virtualization technology that allows users to create and run Virtual Machines on a physical host. Although rated as CVSS 8.8, Microsoft said the exploitation is less likely due to the complexity of the attack and the set of prerequisites:
To successfully exploit this vulnerability, an attacker must be present on the guest VM to craft and send file operation requests to hardware resources on the VM, resulting in potential cross-VM attacks, compromising multiple VMs and expanding the attack’s impact laterally.

CVE-2024-49112 is the highest-scored Remote Code Execution vulnerability, with a CVSS of 9.8 and rated as Critical. It affects Windows Lightweight Directory Access Protocol (LDAP), the widely used cross-platform protocol for directory services authentication.
This vulnerability can be used in the context of CVE-2024-49124 and CVE-2024-49127, where successful exploitation would allow an attacker to execute arbitrary code on Domain Controllers in the context of the LDAP service by sending a specially crafted set of LDAP calls. It’s important to note that Microsoft recommends disconnecting Domain Controllers from the internet, which is highly unlikely to happen in real life. Still, it speaks volumes about the severity of this one. Therefore, patching this one as fast as possible is highly recommended.
| CVE | Severity | Type | CVSS | Exploitation |
| CVE-2024-49138 | Important | Elevation of Privilege | 7.8 | KNOWN EXPLOIT |
| CVE-2024-49106 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49108 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49112 | Critical | Remote Code Execution | 9.8 | Less Likely |
| CVE-2024-49115 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49116 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49117 | Critical | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-49118 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49119 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49120 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49122 | Critical | Remote Code Execution | 8.1 | More Likely |
| CVE-2024-49123 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49124 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49126 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49127 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49128 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-49132 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2024-43594 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2024-43600 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-49057 | Important | Spoofing | 8.1 | Less Likely |
| CVE-2024-49059 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2024-49062 | Important | Information Disclosure | 6.5 | Less Likely |
| CVE-2024-49063 | Important | Remote Code Execution | 8.4 | Less Likely |
| CVE-2024-49064 | Important | Information Disclosure | 6.5 | Less Likely |
| CVE-2024-49065 | Important | Remote Code Execution | 5.5 | Less Likely |
| CVE-2024-49068 | Important | Elevation of Privilege | 8.2 | Less Likely |
| CVE-2024-49069 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-49070 | Important | Remote Code Execution | 7.4 | More Likely |
| CVE-2024-49072 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-49073 | Important | Elevation of Privilege | 6.8 | Less Likely |
| CVE-2024-49074 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-49075 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-49076 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-49077 | Important | Elevation of Privilege | 6.8 | Less Likely |
| CVE-2024-49078 | Important | Elevation of Privilege | 6.8 | Less Likely |
| CVE-2024-49079 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-49080 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-49081 | Important | Elevation of Privilege | 6.6 | Less Likely |
| CVE-2024-49082 | Important | Information Disclosure | 6.8 | Less Likely |
| CVE-2024-49083 | Important | Elevation of Privilege | 6.8 | Less Likely |
| CVE-2024-49084 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2024-49085 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-49086 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-49087 | Important | Information Disclosure | 4.6 | Less Likely |
| CVE-2024-49088 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-49089 | Important | Remote Code Execution | 7.2 | Less Likely |
| CVE-2024-49090 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-49091 | Important | Remote Code Execution | 7.2 | Less Likely |
| CVE-2024-49092 | Important | Elevation of Privilege | 6.8 | Less Likely |
| CVE-2024-49093 | Important | Elevation of Privilege | 8.8 | More Likely |
| CVE-2024-49094 | Important | Elevation of Privilege | 6.6 | Less Likely |
| CVE-2024-49095 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2024-49096 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-49097 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2024-49098 | Important | Information Disclosure | 4.3 | Less Likely |
| CVE-2024-49099 | Important | Information Disclosure | 4.3 | Less Likely |
| CVE-2024-49101 | Important | Elevation of Privilege | 6.6 | Less Likely |
| CVE-2024-49102 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-49103 | Important | Information Disclosure | 4.3 | Less Likely |
| CVE-2024-49104 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-49107 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2024-49109 | Important | Elevation of Privilege | 6.6 | Less Likely |
| CVE-2024-49110 | Important | Elevation of Privilege | 6.8 | Less Likely |
| CVE-2024-49111 | Important | Elevation of Privilege | 6.6 | Less Likely |
| CVE-2024-49113 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-49114 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-49121 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-49125 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-49129 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-49142 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-49041 | Moderate | Spoofing | 4.3 | Less Likely |
| CVE-2024-12053 | High | Remote Code Execution | 8.8 | More Likely |
ADOBE released patches addressing more than 160 vulnerabilities across 16 products. Ninety of these vulnerabilities are related to Adobe Experience Manager, while only six have been fixed in Acrobat and Reader. These vulnerabilities could potentially lead to code execution, DoS, or memory leaks. CVE-2024-43711 is the only vulnerability with a critical severity (high based on the CVSS score).
Google released CHROME version 131, addressing 12 vulnerabilities. MOZILLA released FIREFOX version 133, addressing 18 vulnerabilities, including CVE-2024-11691, an out-of-bounds write affecting Apple GPU drivers via WebGL, and CVE-2024-11699, a set of memory corruption vulnerabilities that could allow attackers to execute unauthorized code, potentially leading to system compromise, privilege escalation, or data theft.
CISCO also released security updates for multiple products, for Cisco NX-OS and Cisco ASA. SAP releases security updates for multiple products as well, while VEEAM released security updates for a critical vulnerability in their Service Provider Console.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
This way, Risk-Based Prioritization is already done, and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
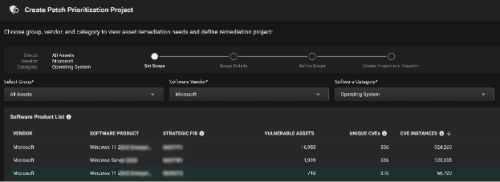
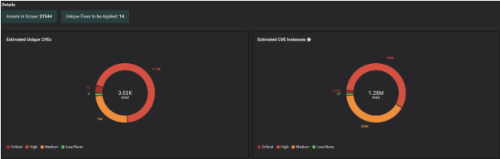
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.