

August 13, 2024
In this Patch Tuesday edition, Microsoft addressed 101 CVEs, 89 Microsoft CVEs and 12 non-Microsoft CVEs. Seven are Critical, and 77 are Important. Ten are zero-days, with six exploited in the wild.
Patches cover Windows DNS, Secure Boot, Kernel, Security Center, Smart Screen, App Installer, Scripting and Office components.
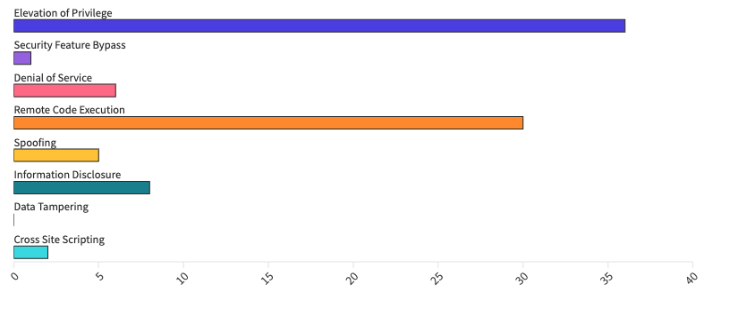
From an Impact perspective, Escalation of Privilege (EoP) vulnerabilities accounted for 41%, followed by Remote Code Execution (RCE) at 34%, and Denial of Service (DOS) at 7%.
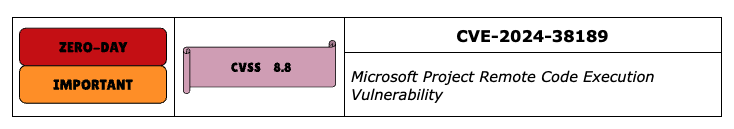
CVE-2024-38189 is a Remote Code Execution (RCE) vulnerability in Microsoft Project, a commonly used project management software that helps professionals manage resources, tasks, schedules and budgets, track progress, and analyze workloads.
This CVE has a CVSS score of 8.8 and is rated by Microsoft as Important. It was already exploited in the wild and added to the CISA KEV list, with a patch target of September 3rd, 2024.
Successful exploitation requires the victim to open a crafted Microsoft Office Project file, either sent as an attachment or through a drive-by download. However, because the exploit only works when the “Block macros from running in Office files from the Internet policy” is disabled and the VBA Macro Notification Settings are disabled, its potential for exploitation is significantly lower.
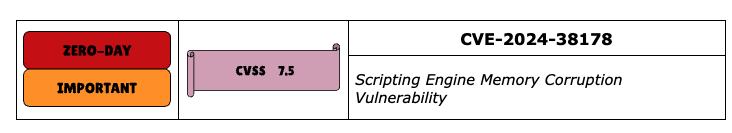
CVE-2024-38178 is another zero-day vulnerability, this time in Windows Scripting. It has a 7.5 CVSS score, but Microsoft notes that successful exploitation has already been observed.
For the exploit to be successful, the attack requires an authenticated user to use Edge in Internet Explorer mode and then click on a compromised URL, providing RCE, which — at first sight — is not that likely to happen in general. However, even with these unlikely prerequisites, several cybersecurity agencies reported observing this CVE exploited in attacks.
Remediation involves patching Windows and the OS itself. All Windows versions are affected.
CVE-2024-38106 is a zero-day vulnerability in Windows Kernel. This Elevation of Privileges flaw gives SYSTEM privileges in case of successful compromise.
Microsoft has not publicly disclosed the exact details, but they mentioned that this CVE would require a highly complex attack, requiring the attacker to win a race condition.
However, CISA added this vulnerability to the KEV list with a target patch date of September 3rd, 2024 — signaling that it might be quite important. We don’t know all the details at this point.
CVE-2024-38107 is another zero-day for which Microsoft shared little detail of how it works and how it can be exploited.
This is an Elevation of Privilege vulnerability that allows an attacker with regular user privileges to elevate access and obtain SYSTEM privileges. This CVE seems to align a lot of stars for a very dangerous kind of attack, considering that it doesn’t require user interaction, works with just a regular user account, and has low attack complexity. This would be a good candidate to prioritize.
CISA signals another high potential risk by adding this CVE to the KEV list, again with a short lead time for patching.
Not to raise too many eyebrows here, but this starts to look like a pattern — vendors are not offering many details of the vulnerability and/or how the exploit works, while CISA is adding it to the urgent patching list.
CVE-2024-38063 — We decided to investigate this critical vulnerability more closely, as it contains many bad ingredients.
First, we start with the 9.8 CVSS score combined with the fact that it’s an RCE (Remote Code Execution), affecting all versions of Windows on one of the most basic components — the TCP/IP stack.
Second, a successful attack would mean sending a sequence of specially crafted IPv6 packets to the host. A Windows kernel’s IPv6 parser bug enables the attacker to run an RCE.
Now, this is where it gets really interesting:
As a workaround, Microsoft suggests disabling IPv6 altogether. Microsoft explained that only IPv6 packets could be exploited and released patches for all Windows versions. But what about the good and old firewall? Shouldn’t this be the first line of defense and one of the mitigations?
This needs to be further analyzed in detail, but it suggests that the parser bug happens BEFORE the traffic is sent to the Windows Firewall. So, as long as IPv6 packets can reach the target host and the IPv6 stack is enabled, the system would be exploitable, regardless of local firewall settings. If confirmed, this puts this CVE at the top of our monthly priority list.
| CVE | Severity | Type | CVSS | Public |
| CVE-2024-21302 | Important | Elevation of Privilege | 6.7 | Less Likely |
| CVE-2024-29995 | Important | Elevation of Privilege | 8.1 | Less Likely |
| CVE-2024-37968 | Important | Spoofing | 7.5 | Less Likely |
| CVE-2024-38063 | Critical | Remote Code Execution | 9.8 | More Likely |
| CVE-2024-38084 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38098 | Important | Elevation of Privilege | 7.8 | Unlikely |
| CVE-2024-38106 | Important | Elevation of Privilege | 7 | KNOWN EXPLOIT |
| CVE-2024-38107 | Important | Elevation of Privilege | 7.8 | KNOWN EXPLOIT |
| CVE-2024-38108 | Important | Spoofing | 9.3 | Less Likely |
| CVE-2024-38109 | Critical | Elevation of Privilege | 9.1 | Less Likely |
| CVE-2024-38114 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38115 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38116 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38117 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38118 | Important | Information Disclosure | 5.5 | Less Likely |
| CVE-2024-38120 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38121 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38122 | Important | Information Disclosure | 5.5 | Less Likely |
| CVE-2024-38123 | Important | Information Disclosure | 4.4 | Less Likely |
| CVE-2024-38125 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38126 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-38127 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38128 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38130 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38131 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38132 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-38133 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38134 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38135 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38136 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2024-38137 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2024-38138 | Important | Remote Code Execution | 7.5 | Less Likely |
| CVE-2024-38140 | Critical | Remote Code Execution | 9.8 | Less Likely |
| CVE-2024-38141 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38142 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38143 | Important | Elevation of Privilege | 4.2 | Less Likely |
| CVE-2024-38144 | Important | Elevation of Privilege | 8.8 | More Likely |
| CVE-2024-38145 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-38146 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-38147 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38148 | Important | Denial of Service | 7.5 | More Likely |
| CVE-2024-38150 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38151 | Important | Information Disclosure | 5.5 | Less Likely |
| CVE-2024-38152 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-38153 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38154 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38155 | Important | Information Disclosure | 5.5 | Less Likely |
| CVE-2024-38157 | Important | Remote Code Execution | 7 | Less Likely |
| CVE-2024-38158 | Important | Remote Code Execution | 7 | Less Likely |
| CVE-2024-38159 | Critical | Remote Code Execution | 9.1 | Less Likely |
| CVE-2024-38160 | Critical | Remote Code Execution | 9.1 | Less Likely |
| CVE-2024-38161 | Important | Remote Code Execution | 6.8 | Less Likely |
| CVE-2024-38162 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38163 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38165 | Important | #N/A | 6.5 | Less Likely |
| CVE-2024-38166 | Critical | Cross Site Scripting | 8.2 | Less Likely |
| CVE-2024-38167 | Important | Information Disclosure | 6.5 | Less Likely |
| CVE-2024-38168 | Important | Denial of Service | 7.5 | Less Likely |
| CVE-2024-38169 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-38170 | Important | Remote Code Execution | 7.1 | Less Likely |
| CVE-2024-38171 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-38172 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-38173 | Important | Remote Code Execution | 6.7 | Less Likely |
| CVE-2024-38177 | Important | Spoofing | 7.8 | Less Likely |
| CVE-2024-38178 | Important | Remote Code Execution | 7.5 | KNOWN EXPLOIT |
| CVE-2024-38180 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2024-38184 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38185 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38186 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38187 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38189 | Important | Remote Code Execution | 8.8 | KNOWN EXPLOIT |
| CVE-2024-38191 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38193 | Important | Elevation of Privilege | 7.8 | KNOWN EXPLOIT |
| CVE-2024-38195 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2024-38196 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2024-38197 | Important | Spoofing | 6.5 | Less Likely |
| CVE-2024-38198 | Important | Elevation of Privilege | 7.5 | More Likely |
| CVE-2024-38199 | Important | Remote Code Execution | 9.8 | Less Likely |
| CVE-2024-38200 | Important | Spoofing | 7.5 | Less Likely |
| CVE-2024-38201 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2024-38202 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2024-38206 | Critical | Information Disclosure | 8.5 | Less Likely |
| CVE-2024-38211 | Important | Cross Site Scripting | 8.2 | Less Likely |
| CVE-2024-38213 | Moderate | Security Feature Bypass | 6.5 | KNOWN EXPLOIT |
| CVE-2024-38214 | Important | Information Disclosure | 6.5 | Less Likely |
| CVE-2024-38215 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2024-38218 | Important | Remote Code Execution | 8.4 | Less Likely |
| CVE-2024-38219 | Moderate | Remote Code Execution | 6.5 | Less Likely |
| CVE-2024-38223 | Important | Elevation of Privilege | 6.8 | Less Likely |
| CVE-2022-2601 | Important | Security Feature Bypass | 8.6 | Less Likely |
| CVE-2022-3775 | Critical | Remote Code Execution | 7.1 | Less Likely |
| CVE-2023-40547 | Critical | Security Feature Bypass | 8.3 | Less Likely |
| CVE-2024-6990 | Critical | Security Feature Bypass | 8.8 | More Likely |
| CVE-2024-7255 | High | Security Feature Bypass | — | — |
| CVE-2024-7256 | High | Remote Code Execution | 8.8 | — |
| CVE-2024-7532 | Critical | Remote Code Execution | 8.8 | — |
| CVE-2024-7533 | High | Remote Code Execution | 8.8 | — |
| CVE-2024-7534 | High | Remote Code Execution | 8.8 | — |
| CVE-2024-7535 | High | Remote Code Execution | 8.8 | — |
| CVE-2024-7536 | High | Remote Code Execution | 8.8 | — |
| CVE-2024-7550 | High | Remote Code Execution | 8.8 | — |
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy is prioritizing what matters most and reducing the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify cyber risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
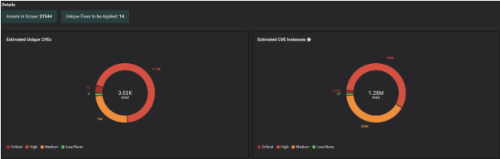
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
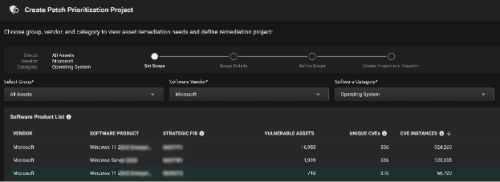
This way, risk-based prioritization is already done, and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
This way, Balbix customers have a clear understanding of the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you are interested in learning more, please sign up for a Balbix demo.