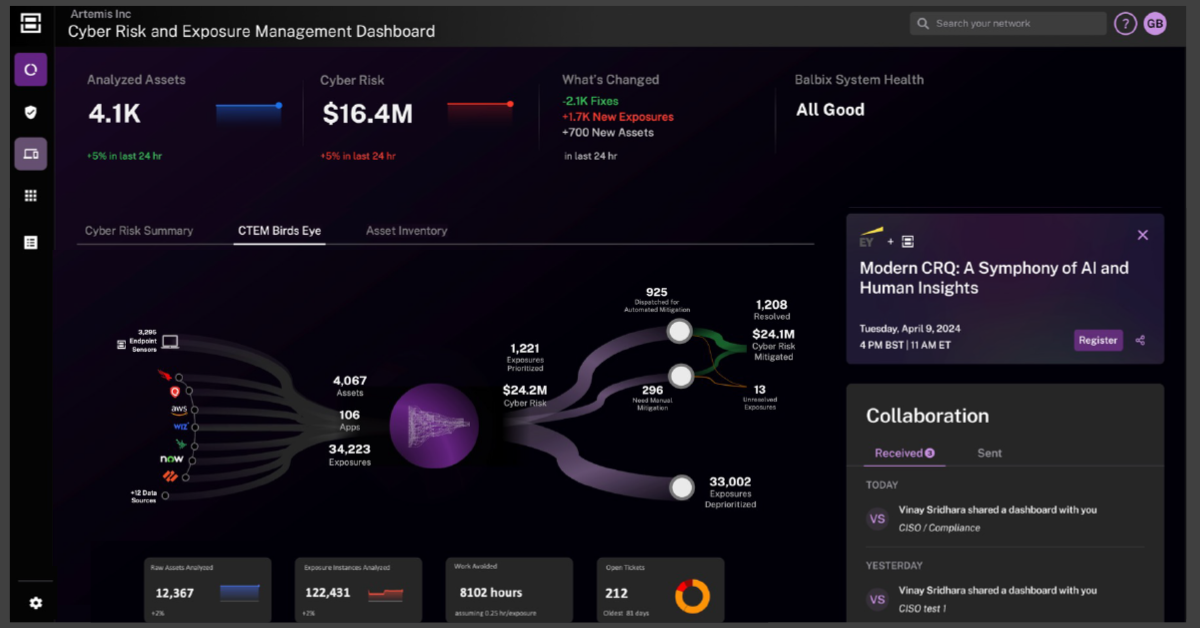
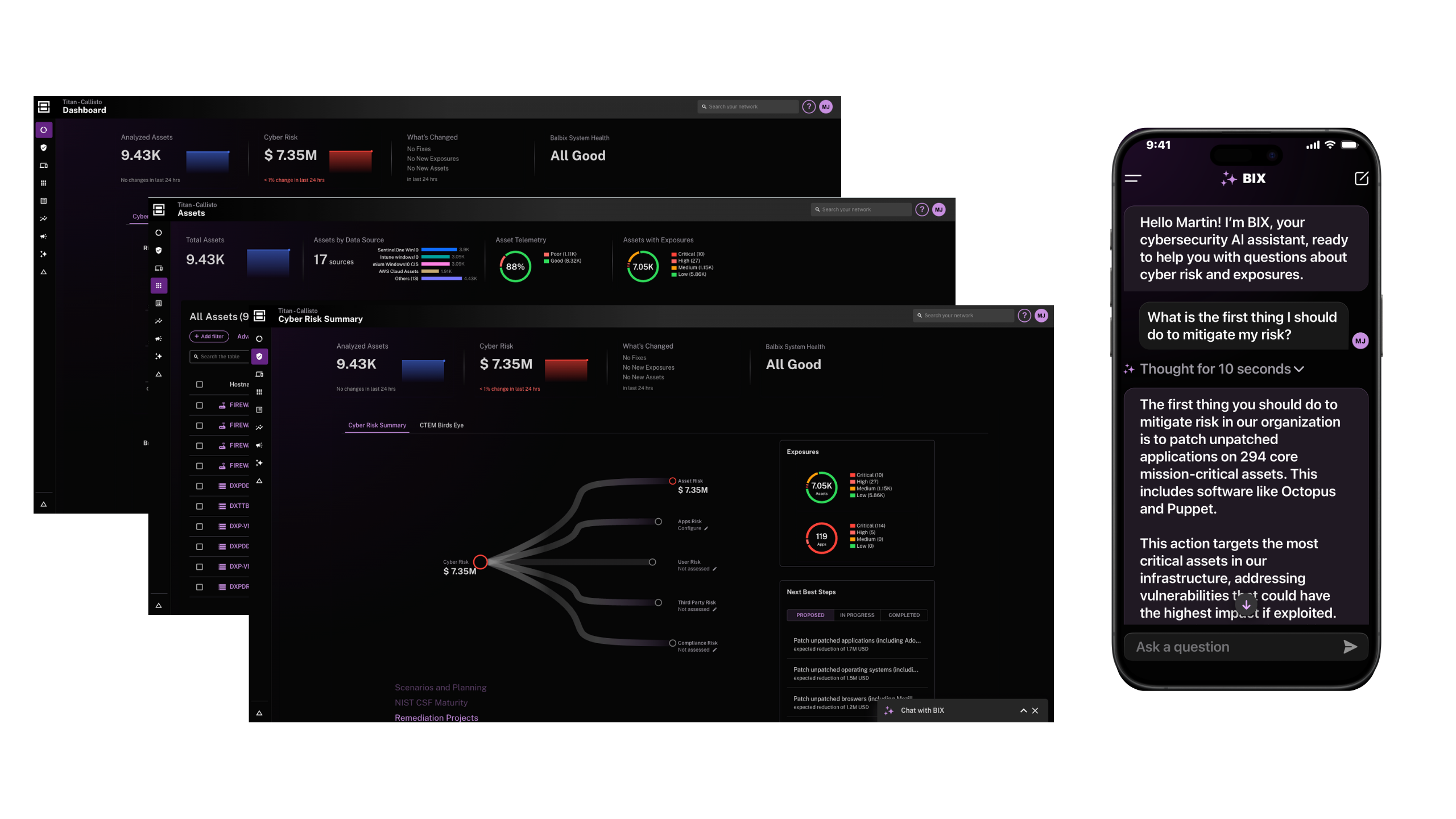
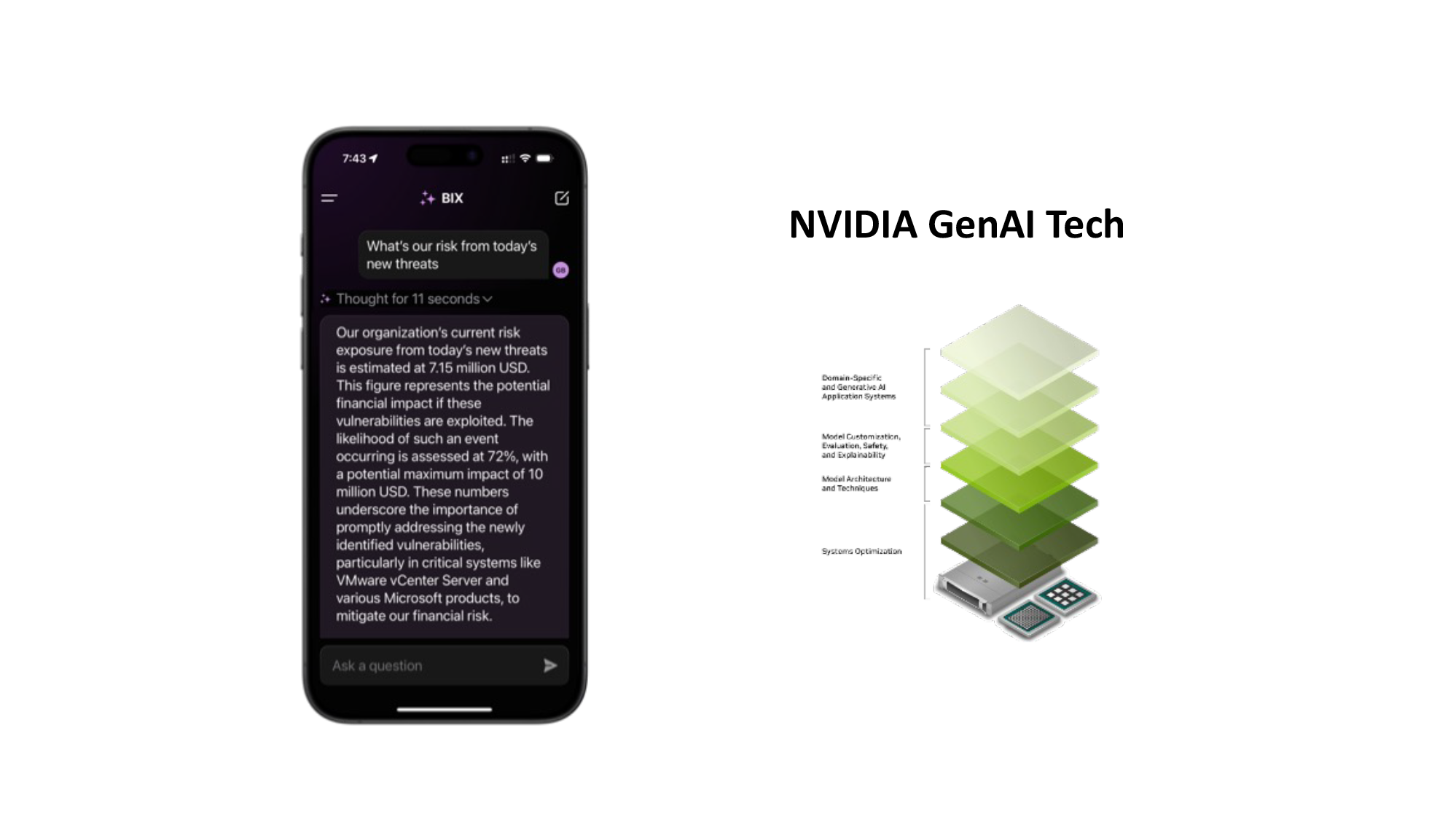
Four New Balbix Capabilities You’ll Love!
The Story of BIX, a Specialized AI Agent for Cybersecurity, Built with NVIDIA AI
Top 11 Cybersecurity Questions Every CISO Should Be Ready to Answer
Stay up to date with us
Get insights on cyber risk management, vulnerability prioritization and board reports
Protecting America’s Water Systems: A Cybersecurity Imperative
What Are We Patching This Tuesday?
A CISO Blueprint for an Effective Board Narrative
Why is Asset Deduplication A Hard Problem?
CISOs: The one question your board will NEVER ask you
What Are We Patching This Tuesday?
Seeing the Unseen: How Generative AI Elevates Situational Awareness in Cybersecurity
CAASM: Dead-End Approach or Worthwhile Journey?
Why I Joined Balbix: Embracing the AI-Powered Future of Cybersecurity
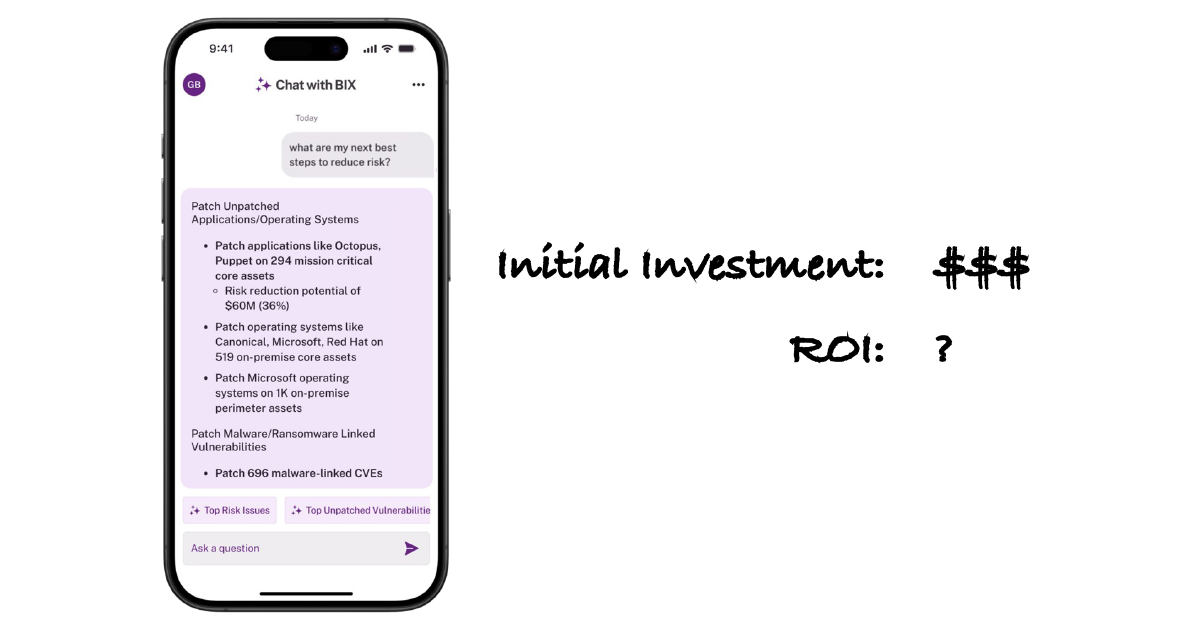
A Cybersecurity AI Assistant: The Pricey Addition You Don’t Need—Or Do You?
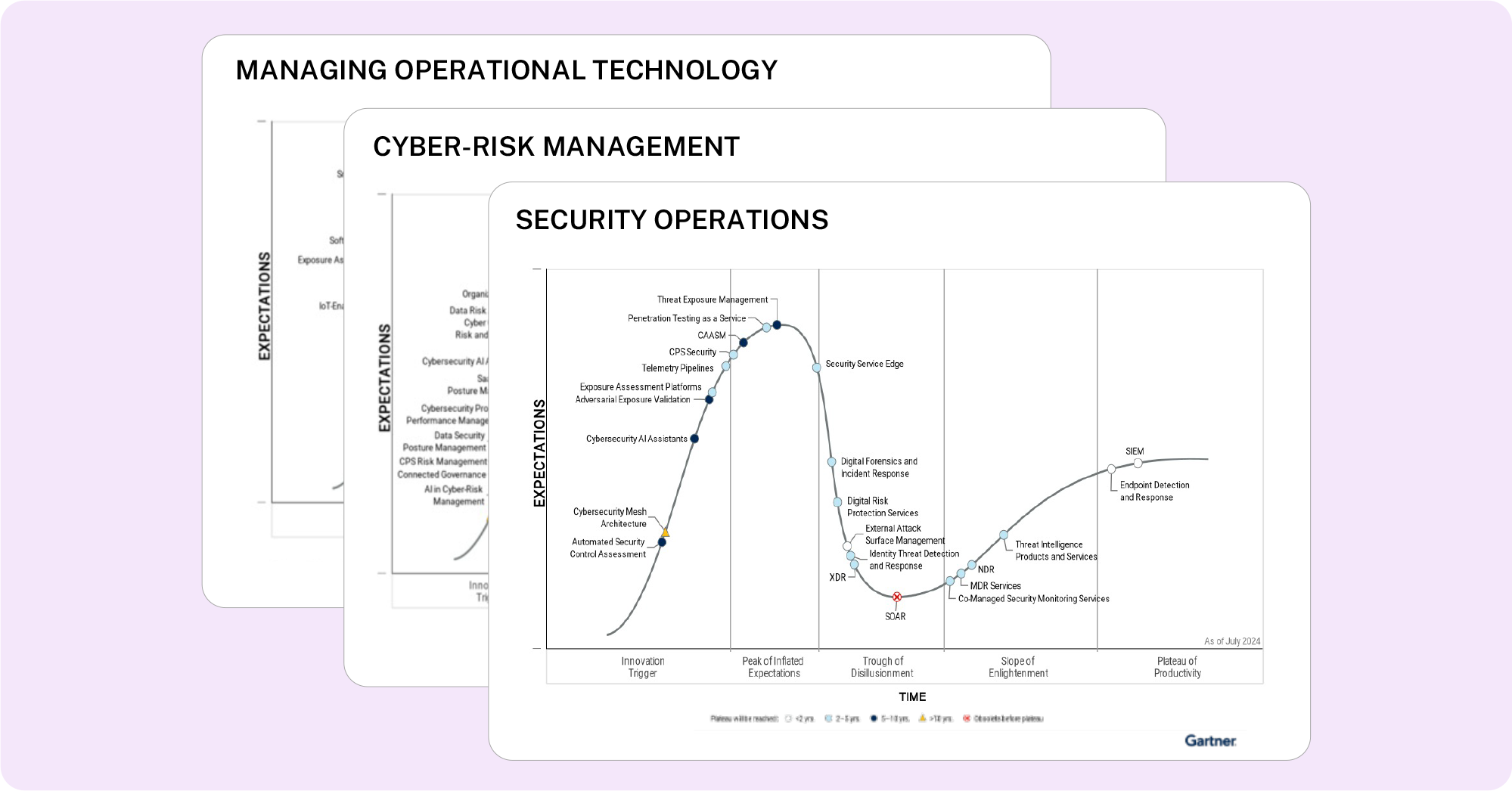
Balbix Recognized in Three 2024 Gartner® Hype Cycle™ Reports
What Are We Patching This Tuesday?