In most organizations, when an urgent and/or high severity vulnerability needs to be addressed, all assets tend to be treated with equal, high priority. There are a couple major flaws in this approach.
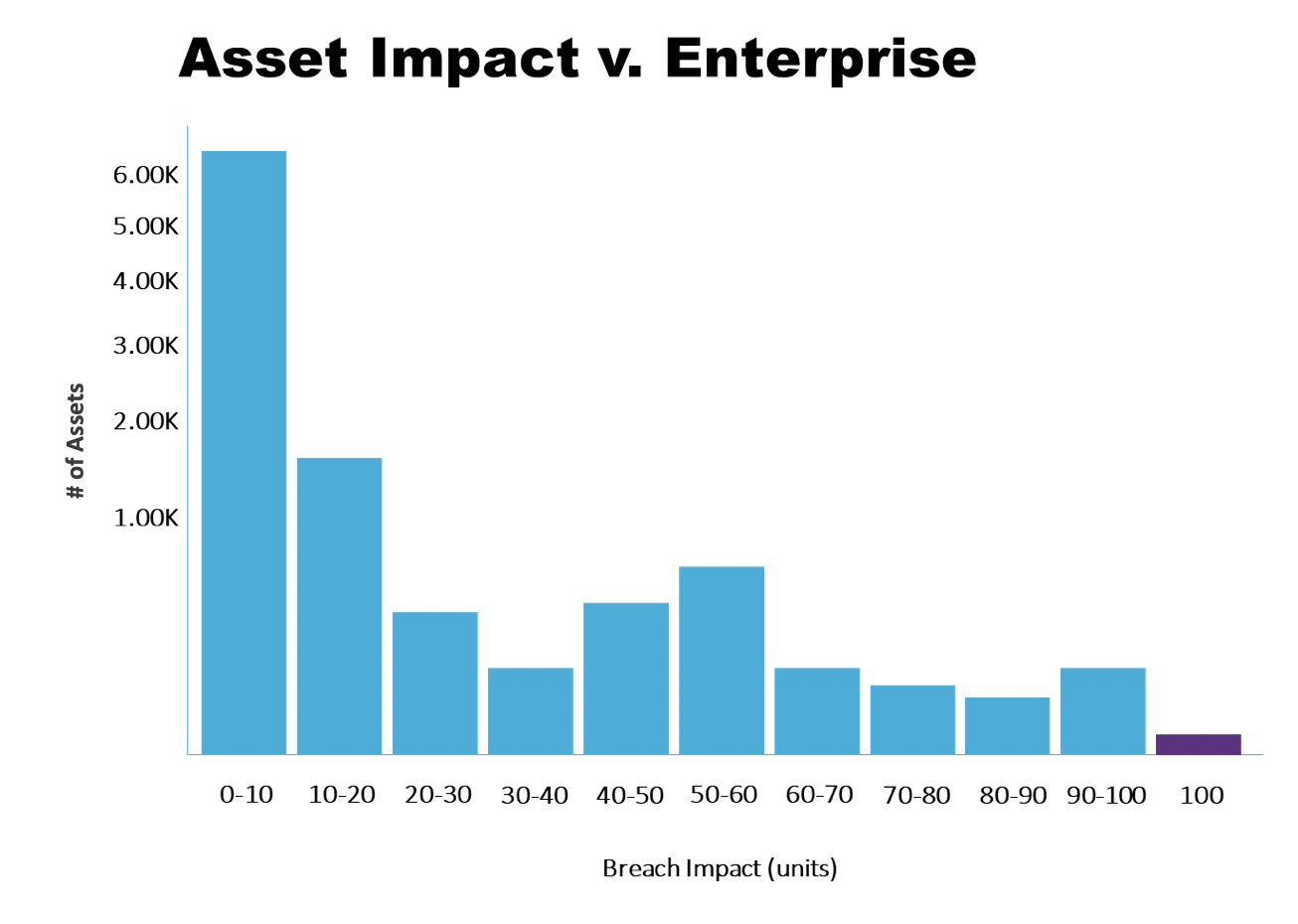
First, in most organizations, there are many more low importance assets than there are critical assets. Below is a screenshot from the Bablix platform, providing an idea of how this looks for a typical medium-sized organization with 10,000 assets. Most organizations, regardless of size, follow a similar reverse exponential distribution, with far more low impact assets than high impact assets.
Patching of a low impact asset, such as a front desk reception desktop connected to a non-critical subnet is less important than patching a high impact asset, such as a critical server or the CFO’s laptop.
Another factor to consider is exploitability. Exploitability is more than just the severity of the CVE score (though that’s an important component). Purpose of the asset is also important.
For example, Spectre and Meltdown affect assets that have more than one user logging into the system with limited privileges. This is a highly likely scenario on a server, but quite a bit less likely on an employee’s laptop. Usage and exposure are also important aspects of exploitability. A machine with a web service exposed to the internet through port 443 is inherently more exposed than a machine on a network with all inbound connections blocked.
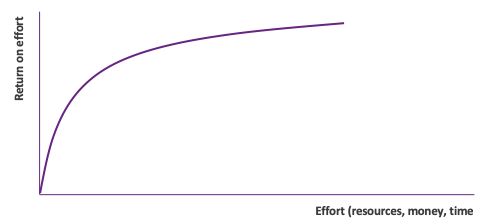
Lack of the ability to identify and prioritize based on attributes such as business criticality and exploitability means that equal effort is placed on all assets. The result is huge amounts of effort needed to get the desired return (breach risk reduction). If you were to graph this, it would look something like this:
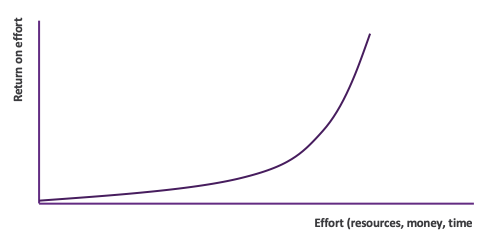
Most organizations can only dream of improving to the point where their return matches the effort put into infosec programs, as in the chart below.
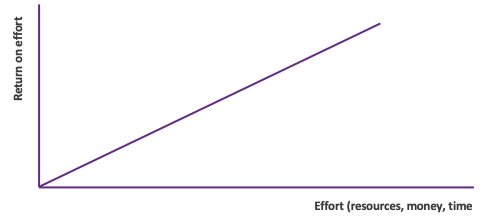
Fortunately, there is a better answer to both of these pictures. By factoring attributes such as business criticality and exploitability into decisions on how to prioritize infosec efforts, enterprises are able to flip the chart entirely, achieving maximum breach risk reduction with minimal effort.
So, how does this look in practice?
A few weeks back, one of our customers called to ask if we could identify all assets with Firefox installed that were vulnerable to 2 particular CVEs he was concerned about. Since Balbix keeps a continuous, real-time inventory of all assets on his network, I said, “Of course,” and walked him through the quick natural language search query he needed to run to identify those assets.
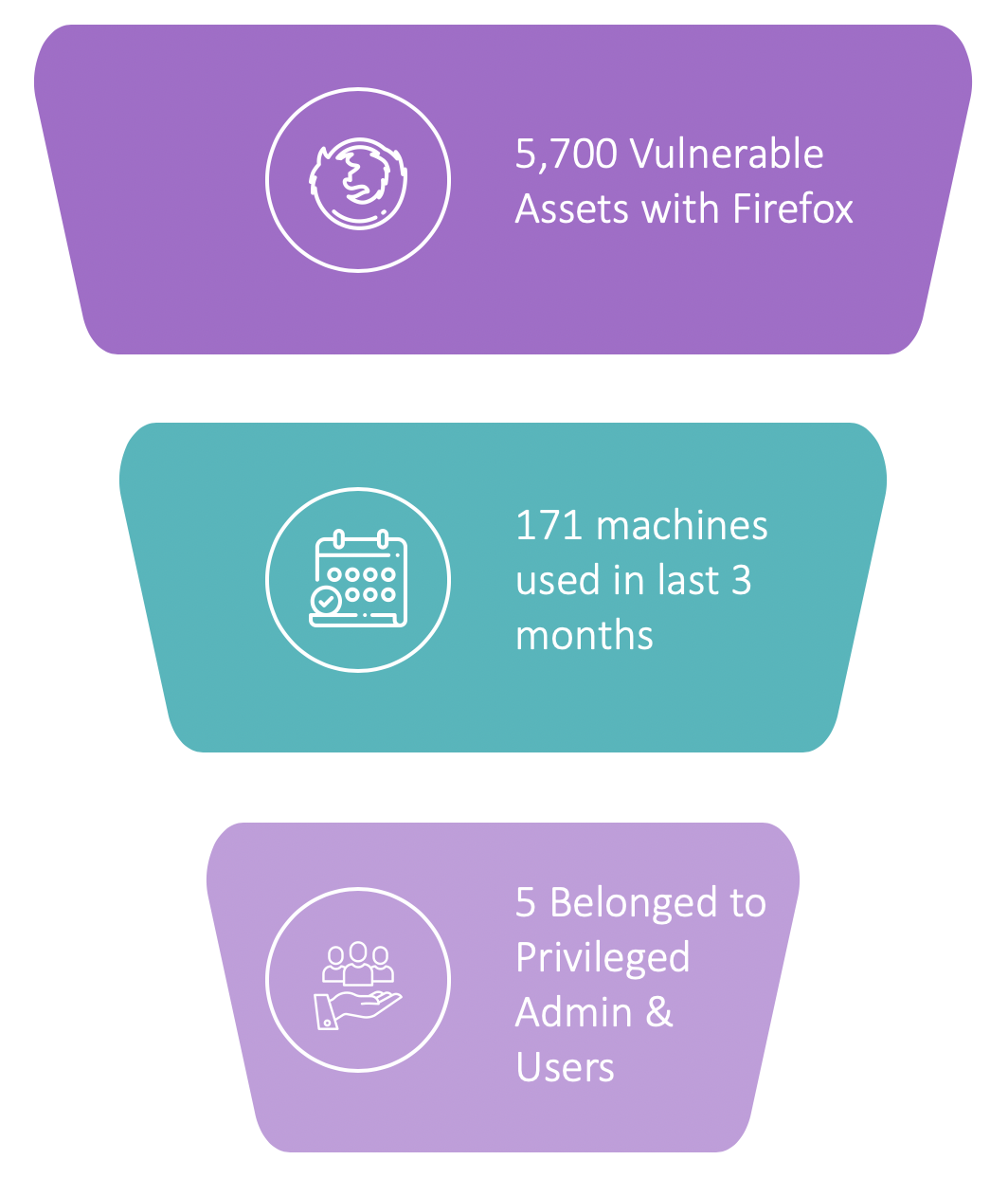
The result? 5,700 assets with Firefox that were vulnerable.
Since this was an urgent situation, this was not the answer that he wanted to hear. The effort involved in patching those 5,700 assets would be monumental, if not impossible for his team to complete in short order.
So how did he flip the graph and achieve maximum results with minimal time and effort?
Another quick search in the Balbix platform revealed that, of those 5,700 machines, Firefox hadn’t been used in more than 3 months on 97% of them. Since the software wasn’t in use, the vulnerabilities in question were not going to be a priority issue. This finding immediately filtered his priority list from 5,700 to 171 machines.
This was much more manageable, but the situation remained urgent. Tracking down 171 end user laptops, many of which might not even be on the network, or even powered on, is still a time consuming task.
How could he prioritize this even further?
Another quick search revealed that of those 171 vulnerable laptops, only 5 belonged to privileged users and admins.
Voila! Within just a couple of minutes, this customer had reduced his focus area to just 0.1% of the vulnerable machines. The target 5 were addressed first, followed by the remainder of the 171 machines with Firefox in active use. And the other 97%? The company scheduled a GPO push to uninstall Firefox from those machines.
Maximum return, minimal effort.