Are you spending all your security resources putting out fires?
In recent years, cyber security has emerged as a top concern for enterprises worldwide, driving significant investment in procuring new security products and services. However, nearly all new security spending and effort is directed toward detecting an attack in progress, or responding to one that has already occurred. While putting out security “fires” is an essential practice, the best way to build a secure enterprise is not necessarily by hiring a lot of firefighters (incident response teams), or purchasing all possible anti-fire equipment (controls such as firewalls and endpoint security). Instead, consider building “fire-resilient” infrastructure and understanding your risk at all times.
Consider this for a moment, would you want to enter a 25-story building if someone told that they had no idea if the building had been designed correctly for fire safety, or inspected recently for it, but all the latest and greatest anti-fire gadgets were installed, and there was a big fire station around the block?
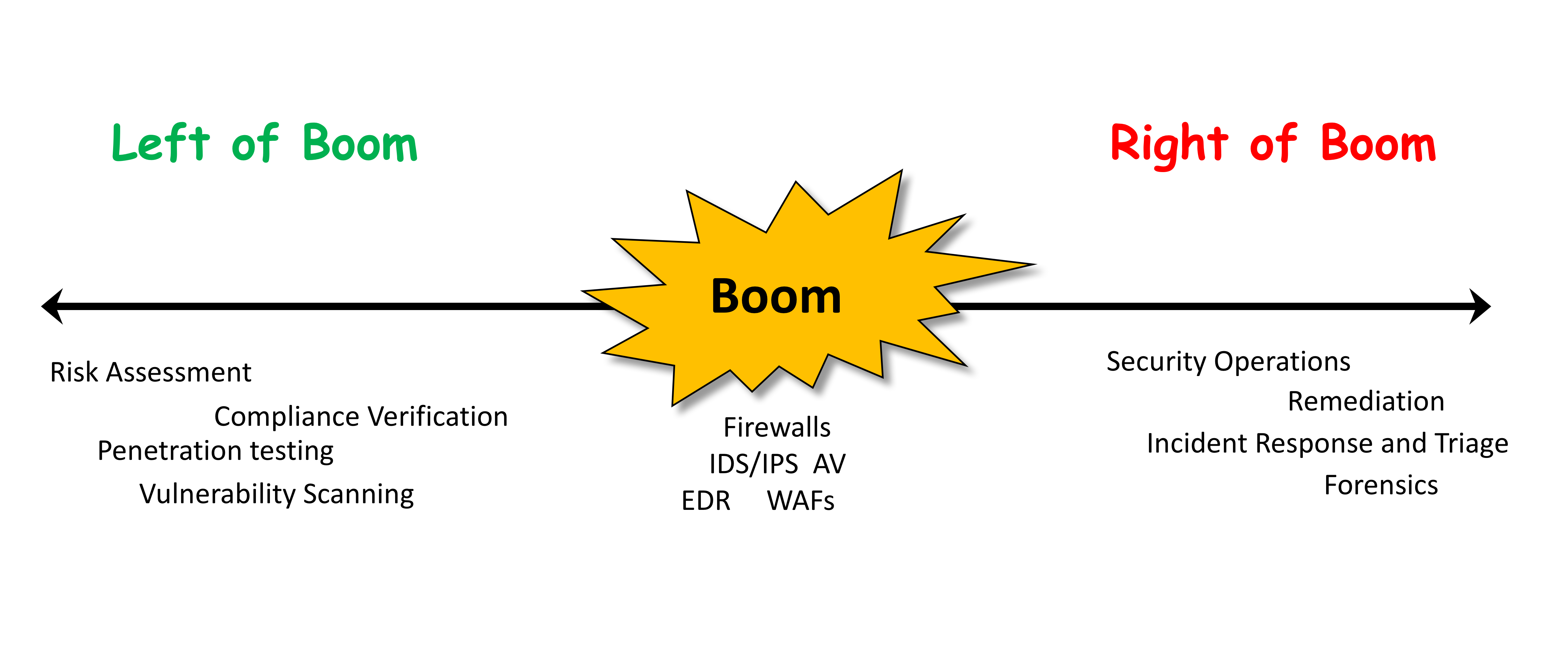
Let’s explore this further by borrowing some terminology and thinking from the military popularized by Washington Post reporter Rick Atkinson. In the realm of cyber, practices and products can be mapped to three phases centered around their operations with respect to the point of “Boom”, with Boom representing an actual attack by an adversary:
- Left of Boom: IT Risk assessment and planning, e.g., Vulnerability Scanning, Risk Assessment, Compliance Verification, Pen testing.
- Boom: Controls to detect and stop attacks in progress, e.g., Firewalls, IDS/IPS, AV, EDR, WAFs.
- Right of Boom: Security Operations, SIEM, UEBA, Incident Response and triage, e.g., Mandiant-style incidence response, security event analytics, Gartner’s SOAR, Forensics.
 In recent years, we have seen an explosion of awareness and interest in Controls (Boom) and Security Operations (Right of Boom) areas. We have seen some fantastic innovation in next-generation firewalls and endpoint controls, using technologies such as virtualization, security event analytics, AI, and workflow automation. Several tens of billions of new security spending and investor value has been created in the last five years with new technology.
In recent years, we have seen an explosion of awareness and interest in Controls (Boom) and Security Operations (Right of Boom) areas. We have seen some fantastic innovation in next-generation firewalls and endpoint controls, using technologies such as virtualization, security event analytics, AI, and workflow automation. Several tens of billions of new security spending and investor value has been created in the last five years with new technology.
While there is no dearth of products and innovation in the Boom and Right of Boom areas, there has been a marked lack of innovation in Left of Boom technologies. Left of Boom stuff has very high value– it can inform and direct every aspect of your security practice, driving value and efficiency.
Enterprise risk assessment and planning technologies, such as GRC, are a decade old, rely extensively on manual processes, and are episodic (typically done 1-2 times a year). Essentially, such systems are just some Math equations, piecharts and reports on top of human filled questionnaires, and lead to an incorrect notion of “paper” cyber risk that is very different from the real on-network breach risk.
Another related practice, vulnerability assessment (VA) is the enumeration of systems likely to be compromised from just one attack vector — unpatched software. VA is rules-based and unable to learn new targets or attack methods by itself. VA is also episodic, with periodic scans generally producing a large number of alerts and events that are difficult to act on as they are not prioritized and without business context. VA tools work mostly on managed devices, and have limited coverage of the vast and rapidly expanding enterprise attack surface. For example, vulnerability assessment does not tell you anything about the risk to your business from weak passwords and shared passwords, or incorrect or incomplete implementations of encryption. Similarly, VA cannot tell the difference between a unpatched primary domain controller and an unpatched lab server.
Medium-sized Businesses need to start Left of Boom.As the threat of attack continues to increase exponentially, the need for Left of Boom tools and technologies has rapidly expanded as many more businesses are at risk of suffering a breach. Security solutions once employed only by large enterprises and government agencies are becoming increasingly applicable for mid-size enterprises and even SMBs. The challenge is making IT Risk assessment and planning simple to operationalize and accessible to businesses that lack the security and risk people necessary to manually analyze the attack surface, or the budget to throw a double kitchen sink of controls at the security problem. If you are the Director of Information Security at a company that has revenues of several hundred million to several billions, and a small security team of less than five, you can’t simply try to replicate the controls and operations of a big New York bank. You cannot do your job without a strategy– innovative Left of Boom thinking and tools can help you with this plan.
Large Enterprise needs to upgrade their Left of Boom thinking.Everyone– even security mature organizations, should systematically and continuously assess whether all required controls are present and functioning, and if there are any important gaps, or any non-working or sub-optimal controls. New Left of Boom technologies have the potential of bringing the risk and security practice in your organizations together, and enable you to eliminate the gap between “paper” risk and on-network breach risk, and maximize your security ROI.
What all businesses need, is a smart system of automated risk assessment,which learns the context of your business, and then continuously analyzes the complete attack surface with little or no human effort, and prescribes the necessary tactical and strategic mitigations to eliminate risk. There is a lot of business value in using automation to identify all that might go wrong from a cyber-security standpoint, prioritizing these indicators of risk (IoRs), and taking proactive steps to mitigate the risk– better coverage, hopefully no breaches resulting from attacks, fewer people needed, JP Morgan Chase-like security posture at a micro-fraction of the cost.
Left of Boom investments are like your company’s security radar. You will be able to “see” the riskiest parts of your business and the adversary’s attack paths befiore bad things happen.No fighter pilot today likes to go into combat without friendly radar!

Gartner and other analysts also recognize the overwhelming and urgent need for left-of-boom thinking, and have identified a new and emerging market — Digital Risk Management. Digital Risk Management (DRM) is poised to take over where traditional GRC and VA falls short. DRM technologies will modernize risk assessment for the era of hyper-threats, Cloud, IoTs and the distributed enterprise, leveraging emerging technologies such as artificial intelligence to make assessment automated and continuous.Left of Boom thinking when properly implemented can bepredictive, prescriptive and preventative.
In today’s threat environment, eliminating risk and avoiding breaches requires enterprises to transition from focusing their resources and efforts on responsively putting out fires to transforming their security practice in the Left of Boom area. A key metric to focus on is measuring the cyber-resilience of your enterprise (a blog on this topic is coming soon).Companies adopting Left of Boom thinking will gain a competitive advantage in security spending ROI, and managing and mitigating breach risk efficiently.
Let Balbix show you how you can plan for, predict and prevent cyber-disasters!
