January 27, 2025
Most organizations believe they have a solid process for managing vulnerabilities and exposures. Yet attackers continue to exploit vulnerabilities as one of the most common paths to breaches. This isn’t because these organizations use antiquated methods but because they struggle to keep up with all exposures. Security leaders can significantly reduce risk by adopting a Continuous Threat and Exposure Management (CTEM) program while meeting compliance requirements. Here’s why making this shift is not just beneficial; it’s urgent.
The failure of vulnerability management to deliver meaningful risk reduction stems from several critical gaps. Here are the most pressing challenges:
Modern organizations face too many vulnerabilities that seem insurmountable. Security teams often struggle to identify critical vulnerabilities. Much time is spent on analysis paralysis, but little is done to achieve actionable outcomes.
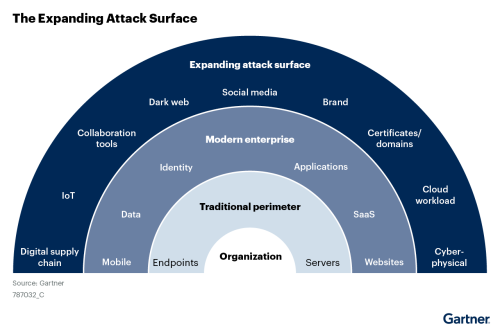
When IT departments are not aligned on remediation priorities, patching, and mitigation efforts stall. A lack of shared understanding creates friction between security and IT, causing delays.
Most security teams communicate in critical, high, medium, and low. Without a way to qualify exposures, the risk is that security teams fail to demonstrate an impact on business and get buy-ins from other executives and leaders.
Managing and deploying fixes requires significant resources. With limited staff and time, IT teams often face significant bottlenecks trying to resolve everything that security teams want them to resolve.
It’s no secret that ineffective or misaligned vulnerability management processes can increase risk and drain team morale and productivity. When combined, these challenges create a compounding burden such as:
An unprioritized flood of vulnerabilities leads to decision fatigue and disengagement. Overwhelmed teams risk overlooking critical issues, leaving the organization exposed to exploitation.
When there is no structured vulnerability management process, the relationship between security and IT teams suffers. Miscommunication and mistrust can derail remediation efforts.
Failure to address critical vulnerabilities promptly perpetuates the problem, leaving the organization exposed to threats that could have been mitigated.
Senior management’s confidence and willingness to invest in security initiatives wanes without demonstrable progress. This creates a vicious cycle of underfunded programs and stagnant improvement.
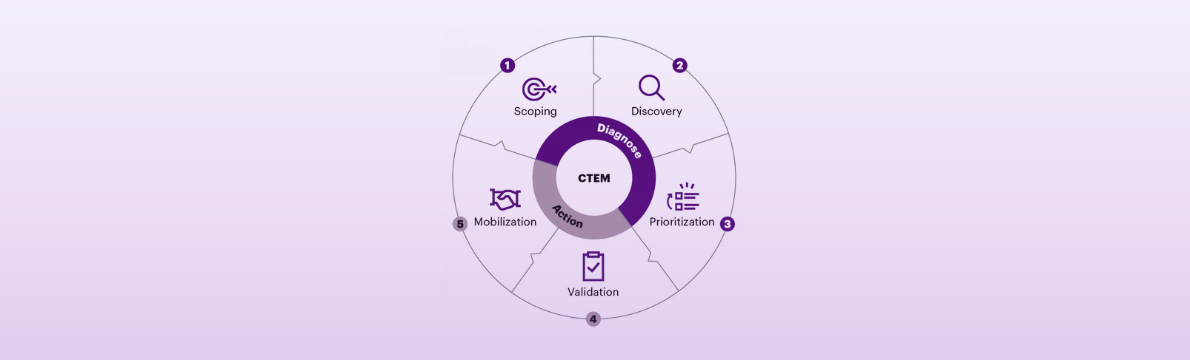
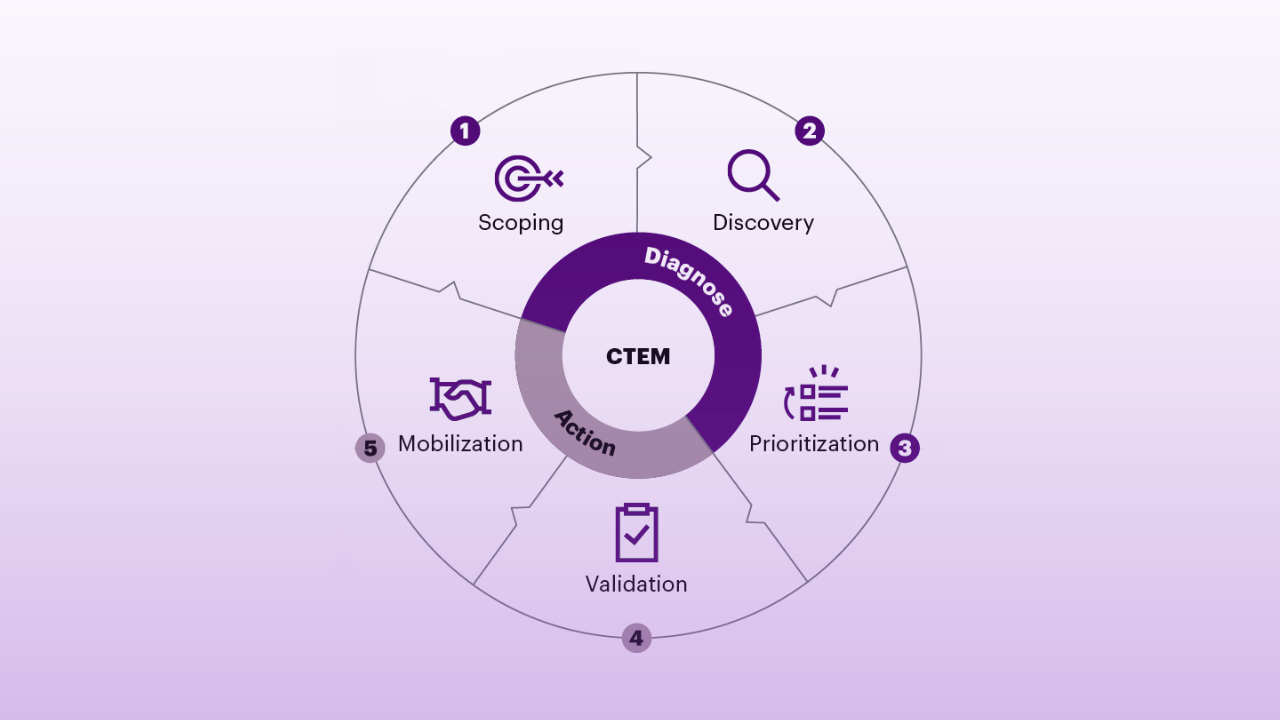
Continuous Threat and Exposure Management (CTEM) offers an opportunity to bridge the gaps left by conventional practices. The continuous process operates in an ongoing cycle of identifying, prioritizing, validating, and remediating exposures. This ensures that security efforts stay aligned with current threat landscapes and organizational priorities, leaving no room for stagnation or oversight.
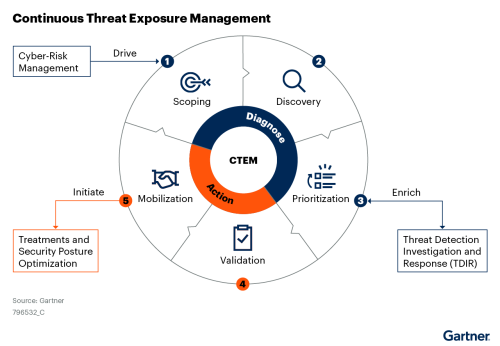
While it is easy to say that you should start by consolidating and gaining visibility into your attack surface, accomplishing it is challenging. Instead, an organization should focus on a specific attack surface, business unit, or geo and map out every associated asset. The aim is to have a comprehensive assessment that uncovers known and unknown vulnerabilities and exposures and gives you the framework to expand and grow this program.
To excel at scoping and exposure assessment, organizations must first define the boundaries and prioritize areas with the highest potential business impact. If the answer is “I don’t know”, they should focus on mission-critical assets, applications, and IoT/OT systems that may directly impact revenue.
A good scoping process involves collaboration to define what’s in and out of scope. Leaders must ensure that scoping remains adaptable, regularly revisiting and refining it as the organization’s threat landscape evolves. Conversely, avoid over-scoping by including too many low-priority assets or irrelevant systems, as this can dilute focus and resources.
Recognize that not all vulnerabilities pose an immediate threat. Focus on those actively exploited or likely to be targeted. Key prioritization techniques include:
Validation adds an extra layer of insight by verifying the real-world impact of vulnerabilities within your unique environment. This ensures prioritization aligns with your organizational risks.
Operationalizing CTEM findings is critical to achieving measurable results. Effective mobilization includes:
A CTEM program enables security leaders to transform their vulnerability management strategy from reactive to proactive. By focusing on exposure assessment, prioritization, and mobilization, organizations can reduce risk more effectively while improving team collaboration and resource allocation.
According to a recent report by Gartner®, security operations teams must embrace exposure management. Gartner® highlights several key strategies like the ones we discussed above for building an effective exposure management program, including:
Balbix empowers organizations to implement CTEM principles with an AI-powered platform that unifies asset visibility, identifies critical exposures, and guides remediation efforts. With Balbix, leaders can confidently reduce exposure, secure critical systems, and communicate ROI to stakeholders.
For a deeper dive into transitioning your organization’s vulnerability management strategy, check out Gartner’s 2024 report, How to Grow Vulnerability Management Into Exposure Management.