

September 21, 2023
This blog is part 2 of our ongoing series focused on reshaping trust in CRQ.
In the earlier part of this blog series, we delved deep into the challenges plaguing the world of CRQ. We underscored how the pervasive lack of trust and accountability in conventional methods has led to unsatisfactory outcomes, confusion, and a crisis of confidence among CISOs and other security leaders. As we pivot from diagnosing the issues to presenting a transformative solution, Part 2 shifts focus towards Balbix—a solution engineered to mend this trust deficit. Here, we will discuss how Balbix fuses the strengths of both top-down and bottom-up approaches in CRQ to offer a seamless, transparent, and dependable risk quantification model.
The Balbix risk model follows a data-driven approach to cyber risk quantification. It involves the following phases:
With traditional CRQ methods, handling the sourcing, gathering, cleansing, and staging necessary data presents a significant challenge. The process is often manual, tedious, and lacks repeatability. Balbix’s highly scalable connector framework makes life easy here. It is designed for efficient and continuous data ingestion and manages large enterprise-scale volumes of data in environments housing millions of assets.
Balbix ingests data from diverse sources, including IT, cybersecurity, business tools, and home-grown tool categories like IT Asset Management, Cloud, CMDB, EDR/XDR, Vulnerability Assessment, IoT/OT, CSPM, BAS, and Networking. Furthermore, Balbix automatically deduplicates and correlates asset inventory and vulnerability data, ensuring that you have a high-fidelity base for asset and vulnerability information. Balbix further enriches this foundation by incorporating business context around assets and integrating pre-curated and pre-integrated threat intelligence.
For customers with data source gaps across part or all of the environment, Balbix provides a variety of software-based sensors to fill in the gaps and provide robust data assurance.
The result is a continuous, unified view of all assets, consolidating all vulnerabilities into a single, cohesive risk model.
After establishing the foundation, Balbix calculates the risk by solving a specific risk equation that considers the organization’s entire attack surface.

For predicting likelihood, Balbix incorporates information about the severity of the issue, the threat level – determining whether attackers are using this specific attack method, and the exposure – assessing whether the software is deployed or used in a way that allows attackers to exploit it using this vulnerability and attack methods, and the effectiveness of any security controls deployed to protect the asset.
To predict the impact of a potential cybersecurity incident, Balbix takes into account the financial consequences that would occur if an asset were compromised. So, how do we assess this financial impact? Balbix performs an asset criticality analysis, ranking and scoring assets based on their importance to the business. This score is leveraged to attribute a financial impact to each asset, enabling a more targeted and practical approach to risk management.
Why is this a challenging problem to solve? All the data that drives the likelihood side of the risk equation changes daily, if not hourly. Assets come and go, software gets updated with new versions, new vulnerabilities are discovered and published, new exploits emerge, and security tools are updated, installed, or removed.
In a typical Fortune 500 company, the amount of data that needs to be analyzed daily to produce an accurate picture of cyber risk ranges from hundreds of terabytes to several petabytes. It is not humanly possible to analyze such volumes and draw insights from them. Balbix addresses this challenge through its automation capabilities and AI-driven models, making such complex and large-scale analysis possible.
While automated risk calculation significantly changes how risks are managed and perceived, it also raises the challenge of making that data actionable for real business impact. Dynamic dashboards and cybersecurity operation improvements help drive actionability. Specifically, it allows CISOs and security teams to:
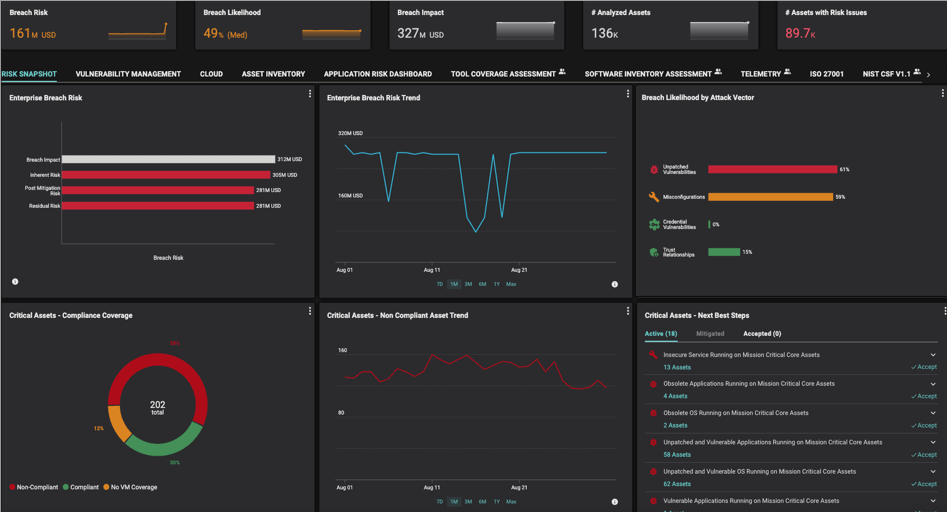
Trust in CRQ isn’t just about using advanced algorithms or aggregating large data sets; it’s about offering a solution that stands up to scrutiny, adapts to the evolving threat landscape, and, most importantly, drives actionable insights for securing your organization. Balbix meets these needs by embodying four vital principles: Practicality, Automation, Transparency, and Actionability.
Practical: Unlike traditional approaches that may be rigid or theoretical, Balbix is designed to be highly data-driven, using near-real-time inputs for its risk calculations. It considers each asset’s IT, cybersecurity, and business context, ensuring an accurate and relative risk representation.
Automated: Gone are the days of manual data crunching and one-off analyses. Balbix continuously calculates risk using real-time asset-level data, including vulnerabilities, threats, exposure, applicable security controls, and business criticality via its automation capabilities.
Inspectable: Understanding what drives the numbers is essential. Balbix is transparent in its calculations, providing insights into what factors drive higher likelihood and impact. Balbix can predict where and how breaches are most likely to happen by analyzing different attack scenarios. It then provides actionable prescriptions that your security team can use to reduce risk consistently.
Actionable: The true value of information lies in its capacity to catalyze meaningful action. Balbix doesn’t just identify risks; it provides actionable insights and automates the workflow for risk mitigation. Following remediation actions, the risk calculations update the model immediately. All this is performed automatically and in near real-time without a need to manually reassess risk, enabling prospects to see tangible risk reduction within 6-12 months.
By choosing Balbix, you’re not just measuring risk but laying the groundwork for a more secure and resilient organization.