Risk has been a key element of business strategy for hundreds of years. The idea of managing risk can be traced back to games in ancient civilizations, where famous mathematicians like Pascal and Fermat developed the basics of modern probability theories. Entrepreneurs who harnessed and built on these theories formed the foundation of business as we know it today.
Insurance has been the most notable industry to capitalize on risk, helping people and businesses hedge their losses in the occurrence of a costly event. The concept of risk prevention and prediction has given rise to other industries like training and safety companies, management consulting firms, and cybersecurity, which has a projected market value of $261 billion by 2024.
What is cyber risk?
Cyber risk is the probability of exposure or potential loss resulting from a cyberattack or data breach. When thinking about cyber risk levels, we should first consider the vectors that can be used to breach sensitive assets and the various devices and apps at risk of being hacked. Today, there are more than 100 attack vectors that adversaries can utilize to attack enterprises.
To make matters worse, the enterprise attack surface is exploding with new devices and apps being added to a company’s infrastructure, endpoints, IoTs, cloud, and supply chain regularly. Keeping an accurate, up-to-date inventory of these digital assets is no longer a human-scale task.
Calculating cyber risk
As you can see, there is already an overwhelming number of factors to consider when thinking about cyber risk in terms of the attack vectors and attack surface that can be exploited; unfortunately there is still much more to account for. Calculating cyber-risk accurately requires a precise inventory of what you are defending and an understanding of two key factors.
The first is likelihood, which is simply the probability that an asset will be breached. Calculating likelihood means accounting for vulnerability severity, exposure due to usage, threat level, and the risk-negating effect of compensating controls. It should be noted that vulnerabilities go beyond CVEs and include things like weak passwords, easily phishable users, and misconfigurations.
The second factor is impact, which only has one variable at play: business criticality. Business criticality asks the simple question, “Just how bad would it be if said asset were to get breached.” For example, information from a CFOs laptop being leaked would be much more detrimental to a company than that of the front desk receptionist.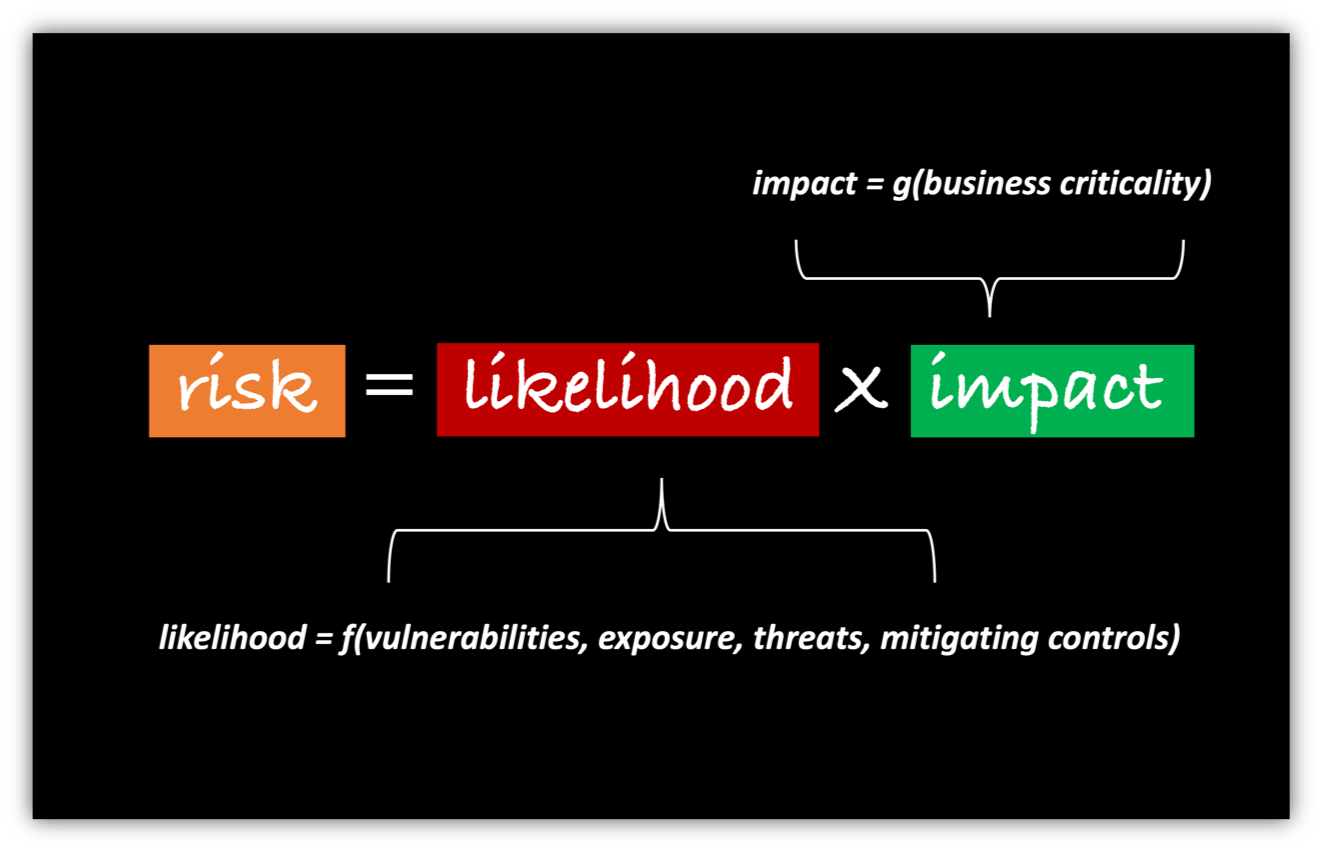
Risk is defined as the probability of a loss event (likelihood) multiplied by the magnitude of loss resulting from that loss event (impact). To accurately calculate risk, this must be computed for every asset in your organization. For today’s enterprise, this might mean anywhere from 10’s of millions to 100’s of billions of calculations, all of which change over time and must be continuously recomputed.
Super-charging calculations with AI
It is probably obvious to you that calculating breach risk is not something that can be done by hand. The quantity and variation of data that goes into these calculations is overwhelming. Today, organizations need tools that use AI and ML algorithms to accurately calculate risk levels.
At Balbix, we use a number of very unique machine learning algorithms to categorize and prioritize cyber risk. Sensors, connectors, and collectors deployed across the enterprise network continuously discover and monitor devices, apps, and users across 100+ attack vectors. The Balbix Brain then uses specialized AI to analyze these 10’s of 1000’s of observations to predict likely breach scenarios.
Probabilistic graphical models (PGMs) are used for calculating the likelihoods of breach across all breach methods. PGMs are extremely effective models for predicting risk because they encode security domain knowledge and continually learn from the observations in an enterprise’s network.
But wait, there’s more
Balbix uses additional advanced machine learning models to figure out other important details that impact risk, such as whether a particular device is on the perimeter or core, whether there are reused passwords on the network or if a user’s device is caching login credentials. An ensemble of such models is chained together to build an overall picture of security posture and breach risk, device by device, group by group, and site by site.
Balbix also provides a clickable risk heat map to drill down into details and a powerful natural-language search to access specific insights. To learn more about how Balbix or schedule a demo, contact us.
