

April 8, 2022
For many CISOs, “what’s the ROI from our cybersecurity tools?” is one of the most difficult questions they face during a board meeting. While it should be a simple question, it’s not easy to answer. Often CISOs may deflect and use operational security metrics, such as mean time to patch. However, operational security metrics aren’t well understood by board members and senior leaders who are trying to understand what measures the organization is taking to reduce risk and the effectiveness of those measures. This is essentially the definition of security ROI: the reduction in risk (in monetary terms) as a result of investing in a security tool.
Being able to measure and report on security ROI allows you to collaborate with your CFO. With ROI metrics in hand, your CFO can help you better communicate the value of existing, and future, security investments to the board. ROI metrics also facilitate discussions with IT and other business owners to get the necessary resources to deploy and maintain security tools.
One way to demonstrate the ROI of a security investment is to calculate the reduction of breach risk in monetary terms. Breach risk is equal to breach likelihood (%) multiplied by breach impact ($). For example, breach likelihood could be reduced by making an investment in a browser isolation solution to lower the risk of drive-by phishing. Similarly, an investment in backup software could reduce breach impact by allowing you to protect your assets against ransomware, by quickly restoring maliciously encrypted software and avoiding the payment of a ransom.

Let’s look at an example of how to calculate the ROI for a security control such as an Endpoint Detection and Response (EDR) solution, which reduces breach likelihood by providing enhanced visibility into attacks on your endpoints and faster response times. In this example, you’re considering increasing the number of EDR licenses (which are currently being used to protect your laptops) to be able to protect a critical group of servers. If the cost of the additional licenses (including deployment) runs $200,000, and the reduction in your breach risk is $2 million, you have a 10x ROI.

Having established the importance and methodology for calculating the ROI of security controls, there are prerequisites to being able to do so. For example, you must have a good asset inventory. Specifically, you need to understand where a security control is deployed and context about the assets your controls are protecting.
You also need to be able to calculate breach impact. Breach impact can be determined by examining each asset’s type, role(s), access, users and other attributes. To assess business criticality of an asset, you need to consider both inherent (e.g., asset category, business unit) and contextual properties of the asset (e.g.,roles, applications, user privilege, and interaction with other assets). For example, your breach impact is significantly higher for core servers containing sensitive data than for personal smartphones sequestered on your guest network. Similarly, an attack on your company’s source code repositories is likely to have a greater impact than the guest sign-in kiosks in your building lobby.
Unfortunately, many organizations have no idea what assets they have in their environment, nor the business significance of those assets.
At Balbix, we’re committed to solving our customer pain points, especially those that are career defining. That’s why we’re pleased to announce the availability of the new security controls ROI calculator.
With our security control ROI calculations, you’ll be able to demonstrate the impact your security controls have in reducing risk, as expressed in monetary terms, to your CFO, board, and other senior leaders.
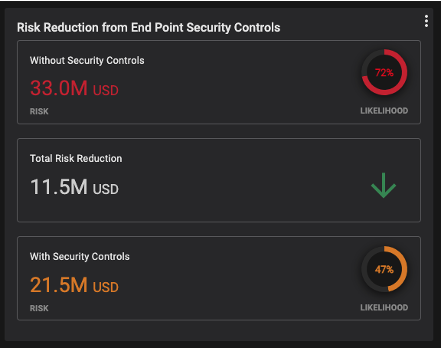
Balbix calculates security controls risk reduction by determining the efficacy of your security controls in reducing breach risk. Today, the ROI calculation is available for endpoint security tools.
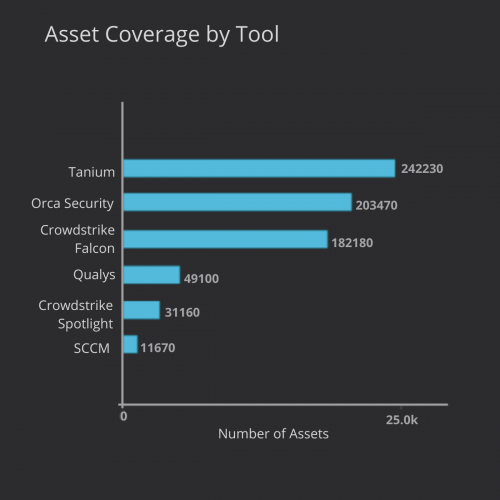
To start, Balbix provides you with real-time visibility into the security controls deployed on your assets, by automatically identifying all your IT assets – including desktops/laptops, smartphones/tablets, IoT/OT devices, servers and cloud workloads. Over 400 attributes are mapped for each asset, including deployed security controls.
Balbix then determines breach likelihood by considering four critical factors: vulnerability severity, threat level, asset exposure and security controls. This compares favorably to other vulnerability assessment products, which only consider two risk factors to determine breach likelihood: vulnerability severity and threat level.
Balbix can consider the additional factors because, unlike other vendors who only provide a CVE-centric model of risk, the Balbix risk model also provides an asset-centric view of risk. In parallel, Balbix calculates breach impact by assessing the business context of the underlying asset and data being protected.
Balbix then allows you to measure and report on changes in breach risk (in dollars) due to the deployment of your security controls and combine that with your cost information to calculate the ROI of changes to your security controls.
Be prepared to answer other tough questions.
While it’s important to answer questions about the ROI of your security program and the tools you’ve deployed, it’s quite possible that you’re going to get other difficult questions at board meetings. Questions like:
To see how Balbix can answer those and other questions, schedule your cyber risk quantification demo today.