Merriam Webster defines context as the interrelated conditions in which something exists or occurs—such as the environment or setting. Another definition for the word context is also “parts of a discourse that surround a word or passage that can throw light on its meaning.”
As we all know, context is supremely important in our lives. Many of the decisions we make, actions we take and things we say are highly dependent on context. Context serves as a shorthand to denote all the (complex) background information and insights that we store in our heads as it relates to the situation on hand. Human brains are very effective in acquiring, storing and using context. For example, reading the word “car” instantly and unconsciously activates all the information (i.e., mental models) you have in your head about cars—about different makes and models, outer shapes, interiors etc. If you parse the word “wash” after the car, another mental model is activated about information your brain has learnt about washing cars. A completely different set of mental models are activated when you read the words “wash sale”. The meaning of the word wash is highly dependent on the context.
As you might imagine, context is also supremely important in information technology (IT), and in particular with cybersecurity. It is very hard to make a good decision without context. And for cybersecurity, accurate context is often not available. Most organizations end up making poor cybersecurity decisions based on intuition and not on data.

For example, let’s take an alarm generated by a “next-generation” network firewall indicating the download of some malicious payload by a user. This may or may not be relevant based on factors like:
- the type of device and software being used by the user, e.g. iPhone or PC—the malicious exploit may work only on Windows PCs.
- the version of software running on the device, a software update to fix the vulnerability may have been installed yesterday, or not
- the presence or absence of a security control, like anti-virus or other endpoint security protection on the device, which would prevent the malicious payload from doing anything bad
- and several other factors…
If security teams are able to get good context, all those nuances surrounding a security event can help to unravel even the most complex problems.
Having good context is particularly critical in cybersecurity vulnerability management (VM) which involves proactively analyzing and fixing weaknesses before attackers can find and exploit them. For example, a certain emergency patch from Microsoft to fix a major vulnerability in IE that inconveniently shows up just a couple of days before Christmas may only need to be applied to those Windows laptops and desktops whose users actually use Internet Explorer as their main browser (as opposed to Chrome or Edge). This context can save IT and security teams from wasting time and effort on unneeded patches, while focusing on stuff that actually matters (or enjoying their Christmas break).
Context is essential in modernizing your VM effort to take a more advanced risk-based approach. Why? Because risk-based VM (RBVM) is all about understanding the unique risk factors of every IT asset touching a network. And that level of analysis and detail requires context for every asset—and its security state and role in the business.
Why is building security context so difficult?
The main challenge to achieving context within RBVM is the massive, dynamically changing datasets that most organizations must analyze to understand the enterprise attack surface. Instead of looking at functions with a few simple variables — and figuring out what those variables are describing — companies must analyze functions with hundreds, or hundreds of thousands, of variables. And even if they could achieve that feat, those variables change over time, which makes it an uphill struggle that makes gathering accurate context very hard to achieve, much less maintain. This leads to organizations making critical decisions using gut instincts without knowing all the facts. And even one bad call can be disastrous.
Another challenge that makes context so hard to achieve is the fact that legacy VM systems struggle to understand the role of assets in business. For example, traditional VM systems don’t properly interpret the distinctions between print servers and DNS servers, especially as it pertains to how those nodes support business objectives.
As a result, companies are left with large amounts of data, a lack of intelligent insights about it, no automated capabilities to help out, and nonexistent or even flawed information about their assets, valuable data and vulnerabilities.
Ingredients to generating accurate context
Advanced AI techniques offer effective ways companies can gather good contextual information. For an easily accessible example of this, query Google, looking for “coffee”. What does google respond with? It will return information about coffee shops nearby, their operating hours, directions on how to get there by car, on foot, or using public transport (as appropriate), and how much traffic you are likely to encounter. Google may also indicate how those shops have been reviewed by other coffee drinkers, and any conditions related to special events you need to worry about.
Now, if you ask Google about “coffee manufacturing”, you will get a completely different answer, one that probably won’t include directions to the nearest coffee factory, which would be silly.
Google can do this because it overlays your location data as well as whatever preferences it knows about you and other people like you, its model for coffee shops and other coffee related things as this relates to your specific query. However, Google might have tried to send you to Argentina if it didn’t have good context about your query based on millions of other searches that people have made, and your personal preferences. And the key is having good AI that is able to quickly generate context based on a lot of ever-changing factors.
In a similar light, Balbix has created information-driven context engines to achieve similar results in the field of breach risk, vulnerability management and cyber-resilience. Balbix’s content-based VM:
- Uses AI, automation and machine learning to comprehensively capture and compile every relevant data point across the enterprise attack surface. This includes human-inspired understanding of what is on the corporate network, elements sitting on extended or partner networks, users and applications. It then analyzes those data points, in context, to determine the full attack potential aligned against each asset.
- Continuously performs its data capture and analysis to ensure that none of its context becomes stale or irrelevant. Decisions made based on the context provided by Balbix’s engines are always founded on accurate, timely and complete information.
Balbix enables security and IT team members to query the enterprise security context using natural language search (e.g., “what is my risk from phishing”) as well as clickable dashboards where you can drill down from a ten-thousand feet risk and view to an individual device’s security posture.
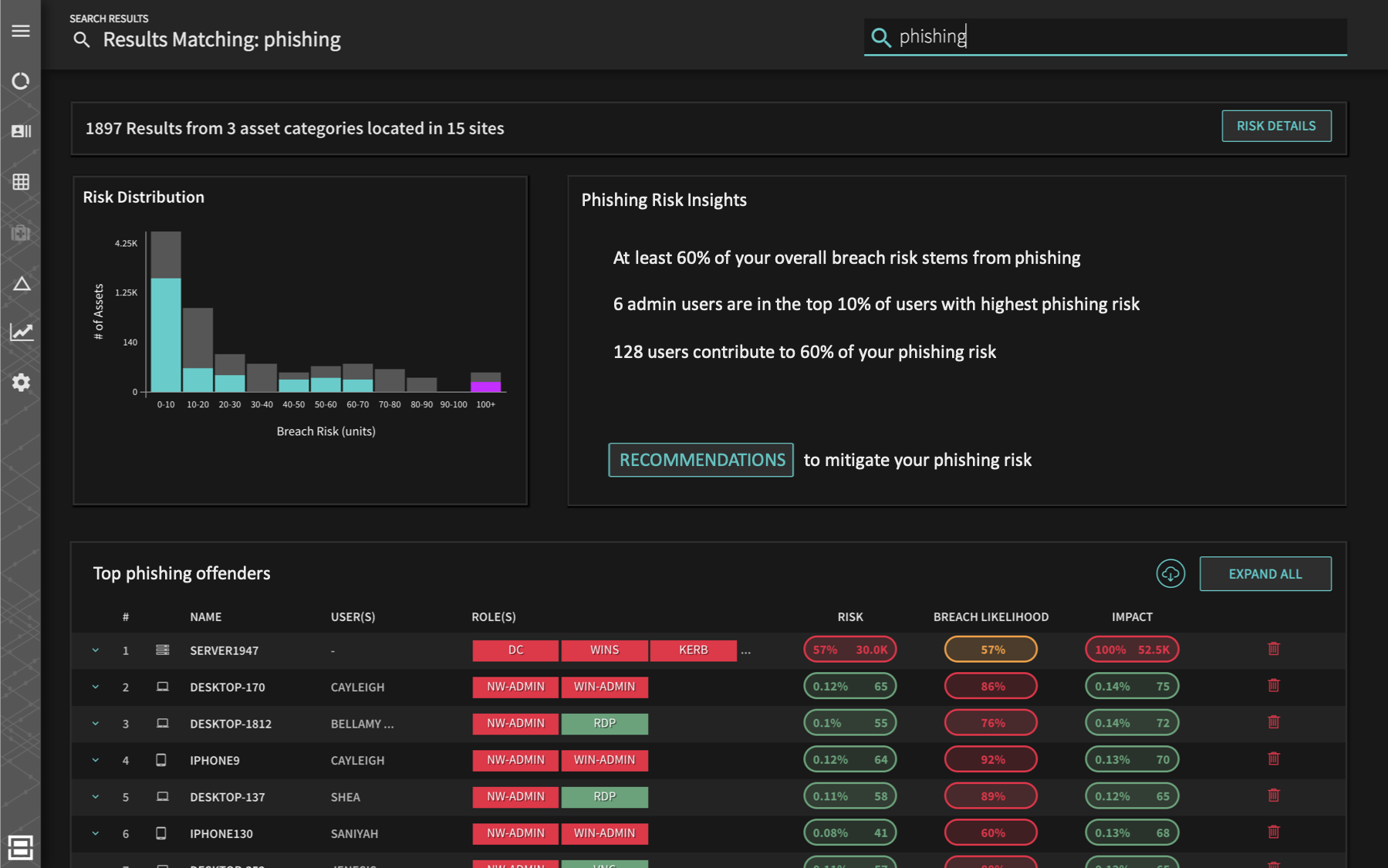
Context is very essential to be effective within cybersecurity. Unfortunately, capturing and studying the full context surrounding a cybersecurity situation or an event is almost never very straightforward. Organizations need to partner with a company that can leverage AI and machine learning to produce accurate, timely and contextually sound results. Doing that can support a highly efficient, risk-based vulnerability management program capable of locating and mitigating critical vulnerabilities long before attackers can strike.
