
September 25, 2024
When was the last time your board asked, “How many vulnerabilities were patched last week?” They didn’t—and they won’t. What they care about is the impact of those vulnerabilities and exposure on the business. They want to know if the business could be exposed, how bad it is, and what actions you are taking to mitigate it.
As a CISO, your challenge isn’t just identifying the vulnerabilities in your environment—it’s communicating their impact to the board in a way that gets their attention.
The board doesn’t want to hear how many vulnerabilities exist in the environment or the patching cadence. They understand and trust that you are doing your job effectively. Most CISOs struggle to articulate how their work impacts the financial and reputational health of the business.
We recommend an approach focusing on risk, actionable solutions, and measurable benefits.
Imagine you are the CISO of a retail chain with thousands of point-of-sale (POS) systems—that process transactions across all your stores. The system has run smoothly for years, but your team has identified 12 critical vulnerabilities. The technical team knows the risks—delayed patching could expose the system to exploitation. However, what the board needs to know is the business risk.
Your pitch: Failing to patch these vulnerabilities could result in significant system downtime, affecting up to 10% of our stores. For us, even a 2-day outage at a fraction of locations could have a significant impact on daily operations. Research shows that companies affected by security breaches experience operational downtime, and even small disruptions in service can snowball into lost revenue, reputational damage, and lower customer loyalty.
By framing the risk this way, the board can see how delays in patching affect security and threaten the company’s ability to operate at capacity. Instead of focusing on “12 vulnerabilities,” articulate your position regarding locations affected by downtime and how the business could face operational inefficiencies and a direct impact on sales.
Communicating the value of patching vulnerabilities is one thing, but gaining buy-in for the resources needed to mitigate the risk is another. The board may not understand the nuances of how certain vulnerabilities increase the attack surface or how quickly an exploit could occur. Instead, show how unmanaged vulnerabilities can lead to significant business disruption.
Your pitch: Our inventory management system tracks stock and manages supply chain operations nationwide. A recent audit reveals that 15% of stores run outdated software, leaving this system vulnerable to cyberattacks. If a critical vulnerability is exploited, it could lead to supply chain interruptions, potentially leading to inventory issues that will delay restocking items at our store.
Patching these vulnerabilities would require downtime, so the board faces a trade-off. Do they risk leaving the system vulnerable or authorizing a phased patching strategy that minimizes downtime to 1-2 hours per store over weeks? By presenting options, you show the board that vulnerability management is about mitigating risk while maintaining operational efficiency.
Explain that a phased approach can minimize the downtime needed to patch while reducing the company’s risk exposure.
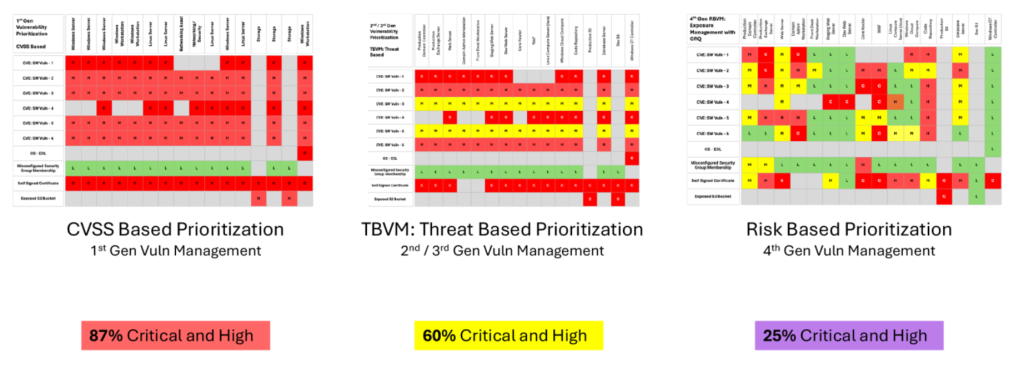
The board wants solutions, not just problems. It’s your job to present actionable steps that demonstrate how you will address the risks without halting operations. For instance, by leveraging 4th-generation vulnerability prioritization, we can prioritize the most critical vulnerabilities based on the risk they pose to the business. This enables the security team to patch high-risk systems first—minimizing downtime and risk while keeping operations intact.
Your pitch: Recent data shows that such AI-powered tools can reduce the number of critical vulnerabilities by 60%. With fewer critical vulnerabilities, we can cut the average time to patch critical vulnerabilities from 15 days to just 4 days. This will put us ahead of time in terms of how quickly attackers exploit vulnerabilities. The rapid response means reducing the exposure window while continuing business as usual, requiring investment in a new tool and training for our security and IT teams. Improving our patch times would reduce the probability of downtime due to cyberattacks to less than 1%, which is best-in-class in our industry.
By shifting the conversation from technical details to business risks and solutions, you not only gain the board’s attention but also make vulnerability management a business priority.
As a CISO, your job is translating technical metrics into actionable insights that resonate with the board. By framing vulnerabilities as business risks, proposing clear solutions, and showing the operational and financial impact of those solutions, you turn vulnerability management into a strategic advantage.
By proactively considering and incorporating AI-powered solutions such as Balbix, you come across as a forward-thinking leader who understands the business language.