One of the main jobs of a vulnerability management team is to keep all systems patched to safeguard your enterprise network and data. To do this effectively, you need to first know what systems you have, namely an inventory of your enterprise IT assets. Then you need to understand which assets have security vulnerabilities and need patching. To tackle remediation, you also need to know in what priority order these systems should be patched. And finally, you need to know how to report on your organization’s patching posture.
Here are 6 key issues that undermine your ability to keep systems patched:
1. Difficulty in identifying vulnerable systems
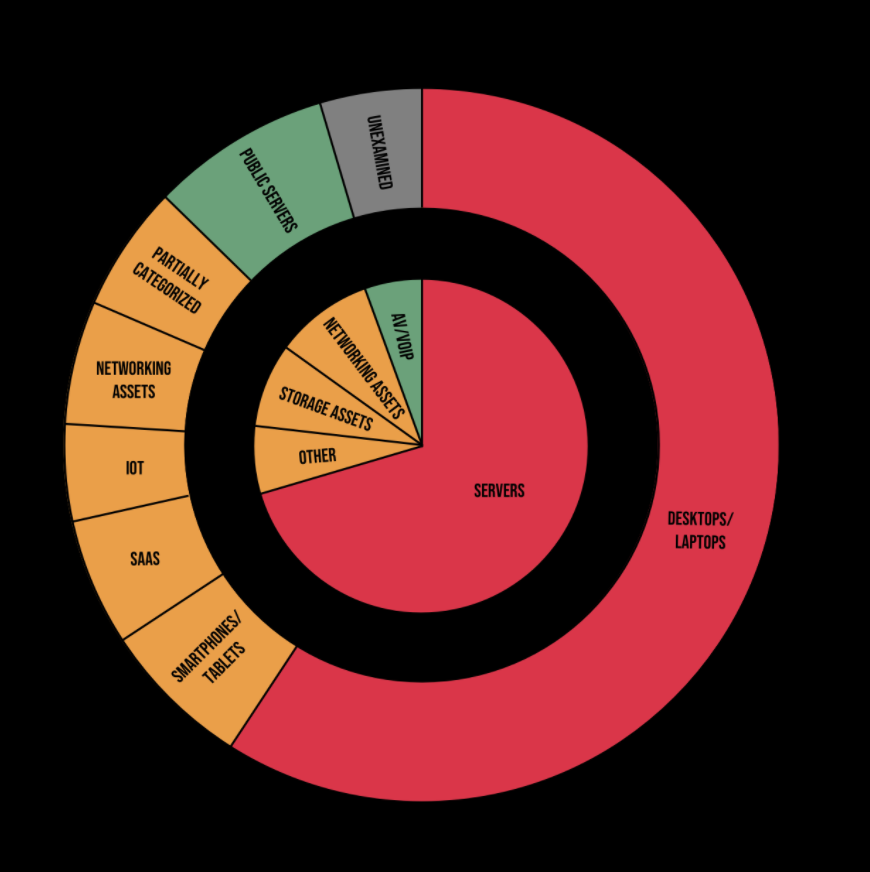
Your enterprise attack surface is massive, with thousands of assets in your enterprise, each susceptible to a myriad of different attack vectors. Unfortunately, it is challenging to keep track of the various devices, applications, and services used by enterprise users. As a result, it is difficult to correctly target vulnerability scans and risk assessments. Covering non-traditional assets such as bring-your-own devices, IoT, mobile assets, and cloud services is particularly problematic. Mechanisms for asset inventory of the organization are manual, don’t discover and inventory IT assets in real time or continuously, and do not provide adequate coverage for all types of assets.
2. Issues with vulnerability scanners
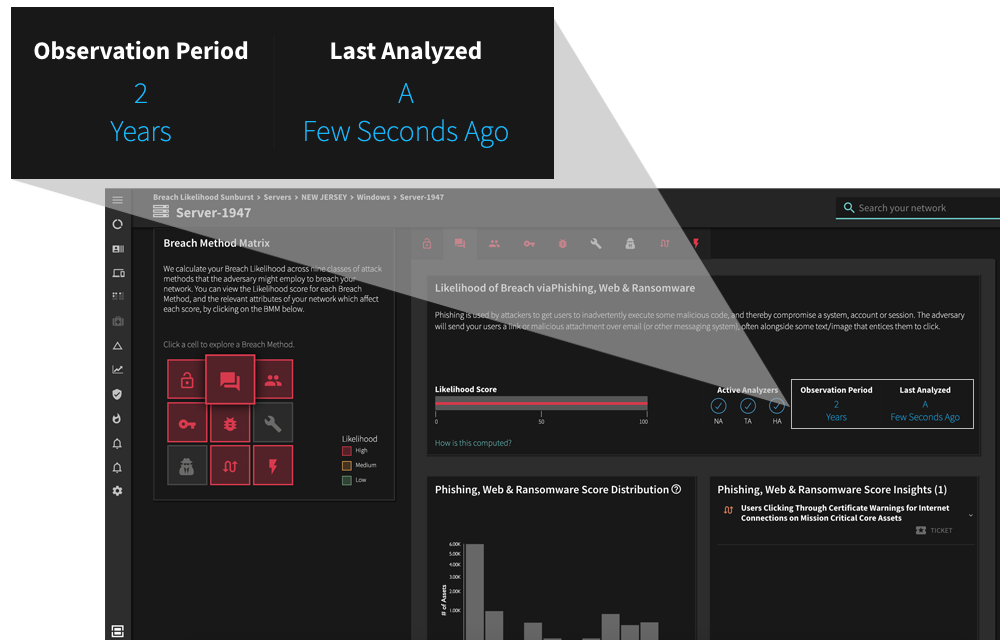
Most vulnerability scanners used in the enterprise today use manual processes that look for known vulnerabilities in networked assets such as servers, routers, and endpoints, generating a report of those vulnerabilities that is sorted based on some severity rating, such as CVSS score. Typically, these scans take a long time to run and not only that, targeting the scans to subnets, hosts, and other parts of the network has to be manually managed. By the time results are available, they are already out-of-date.
3. Overwhelming vulnerability scan reports
Understanding and acting on data output from your vulnerability assessment scanner is a critical component of your vulnerability management program. But it is a well-known fact that vulnerability scan reports are long, extensive, and riddled with false positives. Your vulnerability scanner produces vulnerabilities in the thousands every time a scan completes, leaving your team overwhelmed and struggling with how to proceed.
This inability of security teams to address the vulnerabilities in a timely manner due to the vast number of action items is a significant factor that undermines your ability to keep systems patched.

4. Inaccurate and inefficient prioritization of vulnerabilities
Security teams are typically unable to patch all vulnerabilities, so the list of vulnerabilities gets longer with each new scan. It’s not uncommon for a large enterprise to have thousands or even tens of thousands of vulnerabilities at any time.
As a result, figuring out which vulnerabilities to prioritize and how becomes a daunting task as there are too many unpatched systems and too many updates. Your list of unanswered questions keeps growing:
- You don’t know which systems must be patched right away vs. those which can wait.
- You don’t know which assets are critical or more important than others
- You don’t know which CVEs are actively being exploited
- You don’t know which assets have more exposure based on usage patterns or where they exist in the network and whether they are core or internet facing
- You don’t know if your security controls work well enough to mitigate risk from vulnerabilities on unpatched assets
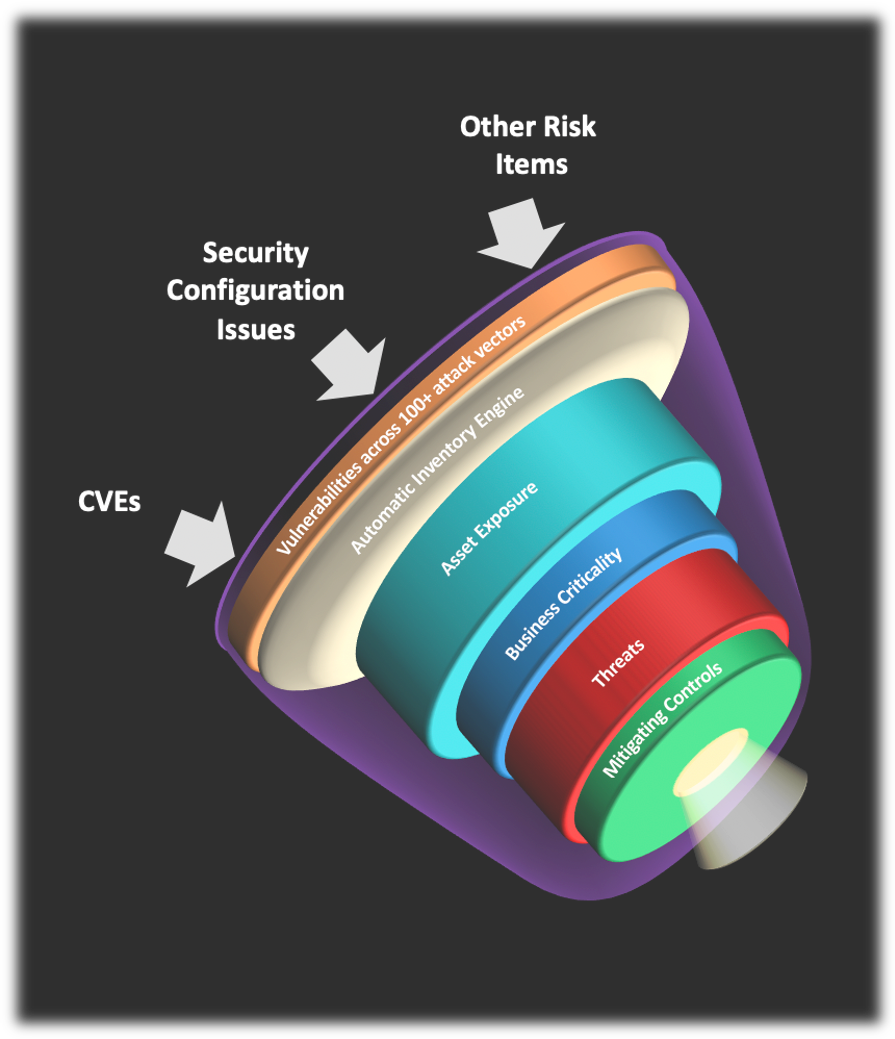
Using primitive risk metrics such as CVSS scores alone or a simple business impact model (high medium and low) to prioritize vulnerabilities is a key factor that undermines your patching processes and results in wasted effort.
5. Knowing whether to act or not to act
Even after knowing which systems are vulnerable or need to be patched, you don’t know if the mitigation steps you plan to take will reduce risk. And what about systems that can’t be patched right away or at all. What do you do about those? Often, it is also not clear what your options for reducing risk are if patching is not possible or if you can reduce the risk from an unpatched asset by using an appropriate compensating control.
This problem is also evident when an emergency patch for a vulnerable system is released because there is no system in place for you to receive a timely notification about its release. This is assuming you know whether you even have any vulnerable systems…
6. Reporting on your patching posture
The main metrics that you use to report on your patching posture are coverage (how comprehensive is your remediation, the percentage of vulnerabilities addressed), mean-time-to-patch (the speed and progress of patching), mean exposure time (how long was the exposure before the system was patched) however, it is challenging to get this data in an accurate and consumable manner in the form of time series and trend lines.
How Balbix can help
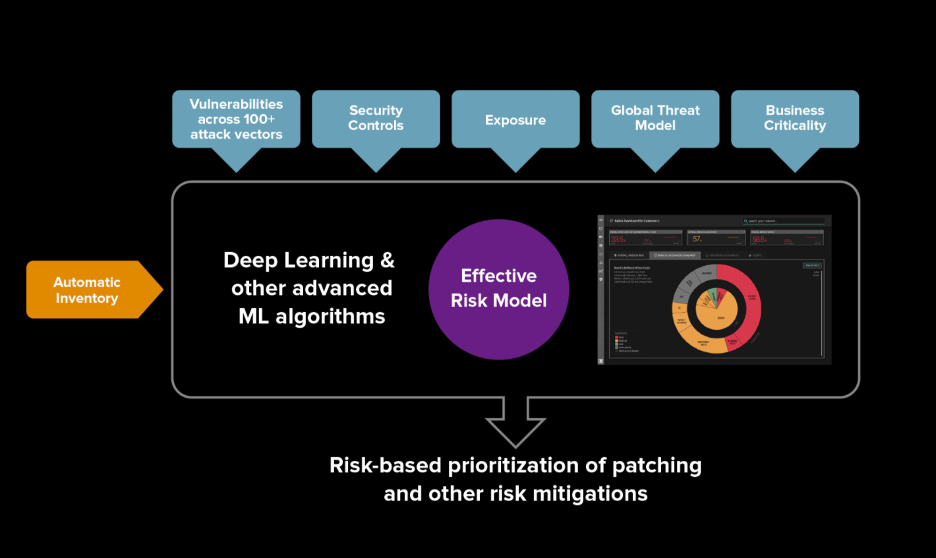
Balbix helps you keep your systems patched. The Balbix platform automatically discovers and categorizes assets, providing continuous monitoring across 100+ attack vectors so you always know what needs to be. There is no need to read through pages upon pages of vulnerabilities as the Balbix dashboard surfaces top risk insights and action items in priority order based on risk. The risk calculation takes into account vulnerabilities, threats, exposure due to usage, existing compensating controls, and business criticality of the assets to prioritize action items. Balbix also enables reporting of MTTP and MET and helps organizations keep track of their patching posture.